Local Area Networks
LAN Applications
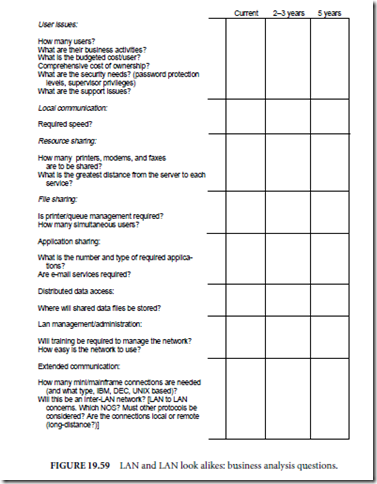
Possible business analysis questions for local area networking solutions are listed in Fig. 19.59. This list of business analysis questions is not meant to be exhaustive or all encompassing. Two important things to
remember about any list of business analysis questions are
1. The questions should dig deeper into the required information systems-related business activities.
2. The answers to these questions should provide sufficient insight as to enable the investigation of possible technical solutions.
Next, each of the business analysis questions’ categories is explained briefly.
User Issues
User satisfaction is the key to any successful network implementation. To satisfy users, their needs must be first thoroughly understood. Beyond the obvious question of: How many users must the network support? are the more probing questions dealing with specific business activities of individual users. Do users process many short transactions throughout the day? Do users require large file transfers at certain times of day? Are there certain activities which absolutely must be done at certain times of day or within a certain amount of elapsed time? These questions are important in order to establish the amount of network communication required by individual users. Required levels of security should also be addressed. Are payroll files going to be accessed via the network? Who should have access to these files and what security measures will assure authorized access? What is the overall technical ability of the users? Will technical staff need to be hired? Can support be obtained locally from an outside organization?
Local Communication
Remembering that these are business analysis questions and not technical analysis questions, users really cannot be asked how fast their network connections must be. Bits per second or megabits per second have little or no meaning for most users. If users have business activities such as computer aided design/computer aided manufacturing (CAD/CAM) or other three-dimensional modeling or graphics software that will be accessing the network, the network analyst should be aware that these are large consumers of network bandwidth and should document those information system-related business activities which may be large consumers of networking bandwidth.
Resource Sharing
It is important to identify which resources and how many are to be shared: printers, modems, faxes, and the preferred locations of these shared resources. The required distance between shared resources and users can have a bearing on acceptable technical options.
File Sharing and Application Sharing
Which programs or software packages are users going to need to perform their jobs? Which programs are they currently using? Which new products must be purchased? In many cases, network versions of software packages may cost less than multiple individual licenses of the same software package for individual PCs. The network analyst is really trying at this point to compile a listing of all applications programs which will be shared by users. Not all PC-based software packages are available in network versions and not all PC-based software packages allow simultaneous access by multiple users. Once a complete list of required shared application programs has been completed, it is important to investigate both the availability and capability of the network versions of these programs in order to assure happy, productive users and the successful attainment of business needs.
Distributed Data Access
Although users cannot be expected to be database analysts, sufficient questions must be asked in order to determine which data is to be shared by whom and where these users are located. The major objective of data distribution analysis is to determine the best location on the network for the storage of various data files. That best location is usually the one closest to the greatest number of the most active users of that data.
Some data files that are typically shared, especially in regionalized or multilocation companies, include customer files, employee files, and inventory files. Distributed data access is even more of a concern when the users sharing the data are beyond the reach of a local area network and must share the data via wide area networking solutions. A good starting point for the network analyst might be to ask the question: Has anyone done a comparison of the forms that are used in the various regional and branch offices to determine which data needs to be sent across the network?
Extended Communications
The ability of certain local area networking solutions to communicate beyond the local area network remains a key differentiating factor among local area networking alternatives. Users should be able to articulate connectivity requirements beyond the LAN. The accomplishment of these requirements is the job of the network analyst. Some possible examples of extended communications might include communications to another LAN. If this is the case, the network analyst must investigate all of the technical specifications of this target LAN in order to determine compatibility with the local LAN. The target LAN may be local (within the same building) or remote (across town or around the world). LAN to LAN connection is known as internetworking and will be studied in the next section Other examples of extended communications may be the necessity for LAN users to gain access to mainframes, either locally or remotely. Again, users are only asked what they need connections to, and where those connections must occur, it is the network analyst’s job to figure out how to make those connections function.
LAN Management and Administration
Another key differentiating factor among LAN alternatives is the level of sophistication required to manage and administer the network. If the LAN requires a full time, highly trained manager, then that manager’s salary should be considered as part of the purchase cost as well as the operational cost of the proposed LAN. Secondly, the users may have requirements for certain management or administration features which must be present. Examples might be user-identification creation or management, or control of access to files or user directories.
Budget Reality
The most comprehensive, well documented, and researched networking proposal is of little value if its costs are beyond the means of the funding organization or business. Initial research into possible networking solutions is often followed by feasibility option reports that outline possible network designs of varying price ranges. Senior management then dictates which options deserve further study based on financial availability. In some cases, senior management may have an approximate project budget in mind which could be shared with network analysts. This acceptable financial range, sometimes expressed as budgeted cost per user, serves as a frame of reference for analysts as technical options are explored. In this sense, budgetary constraints are just another overall, high-level business need or perspective that helps to shape eventual networking proposals.
Anticipated Growth is Key
User needs are not always immediate in nature. These needs can vary dramatically over time. To design networking solutions that will not become obsolete in the near future, it is essential to gain a sense of what the anticipated growth in user demands might be. Imagine the chagrin of the network analyst who must explain to management that the network which was installed last year cannot be expanded and must be replaced due to unanticipated growth of network demand. One method of gaining the necessary insight into future networking requirements, illustrated in Fig. 19.59, is to ask users the same set of business analysis questions with projected time horizons of 2–3 years and 5 years. Incredible as it may seem, 5 years is about the maximum projected lifetime for a given network architecture or design. Of course, there are exceptions. End users may not have the information or knowledge necessary to make these projections. Management can be very helpful in the area of projected growth and informational needs, especially if the company has engaged in any sort of formalized strategic planning methodology.
Network Applications: What Can a LAN Do for You ?
Beyond merely being able to share the same application software packages (spreadsheets, word processing, databases), which ran on individuals PCs before they were networked together over a LAN, networking PCs together provides some unique opportunities to run additional networked applications, which can significantly increase worker productivity and/or decrease costs.
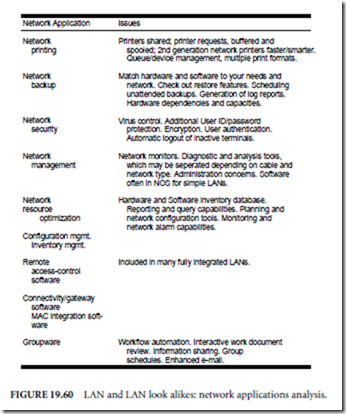
Figure 19.60 summarizes the attributes and issues of some of the most popular uses of a LAN. It should be noted that the uses, features, and issues described next apply only to the listed applications functioning on a local area network. Many of these same functions become much more complicated when running across multiple LANs (internetworking) or over long distance WANs. A short description of each of these LAN applications follows
Network Printing
Network printing continues to evolve as user demands change and technology changes to meet those demands.
On a typical LAN, a networked PC would send a request for printing out onto the network through a network interface card. The networked request for printing services would be accepted by a device in charge of organizing the print requests for a networked printer. Depending on the LAN implementation configuration, that device may be a PC with attached printer, a specialized print server with attached printers, or a directly networked printer. Some type of software must manage all of this requesting, spooling, buffering, queuing and printing. The required software may be part of an overall network operating system or may be specifically written for only network printer management.
Network Backup
Backing up data and application files on a network is essential to overall network security and the ability to recover from the inevitable data-destroying disaster. Although the process and overall components are relatively simple, the implementation can be anything but simple. Basically there are only two components to a network backup system: (1) the software, which manages the backup, and (2) the hardware device, which captures the backed-up files.
Some network backup software and hardware work with only certain network operating systems. Other network backup software will work with only the hardware device with which it is sold. The interaction between hardware devices and software such as operating systems or network operating systems is often controlled by specialized software programs (drivers). It is essential to make sure that the necessary drivers are supplied by either the tape backup device vendor or software vendor in order to ensure the operability of the tape backup device. Hardware devices may be various types of tape subsystems, or optical drives. Key differences among hardware devices include
1. How much? What is the storage capacity of the backup device?
2. How fast? How quickly can data be transferred from a PC or server to the backup device? This
attribute is important if you are backing up large capacity disk drives.
3. How compressed? Can data be stored on the backup device in compressed form? If so, it may save significant room on the backup media.
Remember, backup is not necessarily a one way process. Restoration of backed up files and the ease with which that restoration can be accomplished is a major purchasing consideration. Being able to schedule unattended backups or restorals as well as the ability to spool or print log reports of backup/restoral activity are also important to network managers.
Network Management
The overall task of network management is usually broken down into at least three distinct areas of operation. First, networks must be monitored. Therefore, one of the foremost jobs of network management software is to monitor the LAN to detect any irregular activity such as malfunctioning network adapter cards, or an unusually high data transmission rate monopolizing the available network bandwidth to be shared among all attached workstations. Sophisticated LAN monitoring programs can display maps of the network on graphics terminals. Operators can zoom in on a particular node or workstation for more information or performance statistics. Some monitoring programs also have the ability to compare current network activity to preset acceptable parameters and to set off alarms on network monitor terminals, perhaps by turning a node symbol bright red on the screen, when activity goes beyond acceptable limits. Monitoring software is also written specifically for monitoring file servers on a LAN. Besides monitoring server performance and setting off alarms, some monitoring packages have the ability to dial and set off pagers belonging to network managers who may be away from the network console.
Once a problem has been monitored and identified, it must be analyzed and diagnosed. This is the second major task of network management software. Diagnosis is often done by a class of devices known as protocol analyzers or by the more common name, sniffers. These devices are attached to the LAN and watch, measure, and in some cases, record every bit of data that passes their way. By using multiple sniffers at various points on a LAN, otherwise known as distributed sniffers, bottlenecks can be identified and performance degradation factors can be pinpointed. LAN testing devices must be able to test and isolate the three major segments of any LAN: (1) the wire or cable of the network, (2) the network adapter cards, which interface between the cable and the workstation, and (3) the workstation or PC that generates the network activity.
Having diagnosed the cause of the networking problem, corrective action must be taken against that problem. Perhaps a misbehaving network interface card must be disabled or an application on a workstation that is monopolizing network resources must be logged out. The power to do these things is sometimes called network administration or management. In this case, the term administration is preferable in order to provide a contrast to the previous more general use of the term network management. Most often, the required network management software to manage LANs is included in the network operating system itself.
LAN monitoring software and other specialized network management functions are available as an add-on product for most network operating systems. When these add-on products are manufactured by a company other than the original network operating system vendor, they are known as third-party products. These third-party enhancements are often of high quality but should be purchased with caution. Compatibility with associated software or future releases of the network operating system are not necessarily guaranteed.
Network Security
In addition to the typical security features, such as password protection and directory access control supplied with most network operating systems, more sophisticated network security software/hardware is available for LANs. For instance, security software may be added to workstations and or servers which will
1. Require user identification and valid password to be entered before the PC can be booted.
2. Encrypt important data or application files to prevent tampering.
3. Automatically logout inactive terminals to prevent unauthorized access to system resources.
4. Allow certain users to run only certain applications.
5. Require verification of user authenticity by security verifiers.
Another area of network security that is receiving a lot of attention is that of viruses. Virus control software is sometimes included in network security packages. Virus control is really a three-step process, implying that effective virus control software should address at least the following three areas:
1. Virus protection: User access to systems is sufficiently controlled as to prevent an unauthorized user from infecting the LAN.
2. Virus detection: Sophisticated software to find viruses regardless of how cleverly they may be disguised.
3. Virus eradication: Sometimes called antibiotic programs, this software eliminates all traces of the virus.
Groupware
Groupware is the name of a category of software that seeks to take advantage of the fact that workers are networked together electronically in order to maximize worker productivity. Groupware is a general term that describes all or some of the following software categories: workflow automation, interactive work, group scheduling, document review, information sharing, electronic whiteboard, and enhanced electronic mail.
Local Area Network Architectures
The choice of a particular network architecture will have a definite bearing on the choice of network adapter cards and less of an impact on the choice of media or network operating system. For instance, an ethernet network architecture requires ethernet adapter cards. As will soon be seen, it is the adapter card which holds the key, or media access control (MAC) layer protocol, which determines whether a network is ethernet, token ring, fiber distributed data interface (FDDI) or any other network architecture. Ethernet runs over thick or thin coaxial cable, shielded or unshielded twisted pair, fiber or wireless—clearly a wide choice of media options.
Ethernet
Ethernet, adhering to the IEEE 802.3 standard, is a carrier sense multiple access with collision detection- (CSMA/CD-) based network architecture traditionally installed in a bus configuration, but most often installed in a hub-based star physical topology. Every device, most often network adapter cards, attached to an ethernet network has a unique hardware address assigned to it at time of manufacture. As new devices are added to an ethernet network, their addresses become new possible destinations for all other attached ethernet devices.
The media access layer protocol elements of ethernet form data packets for transmission over the shared media according to a standardized format. This ethernet packet format is nearly equivalent to the IEEE 802.3 standard, and the two terms are often used interchangeably.
The potential for collisions and retransmission exists on an ethernet network thanks to its CSMA/CD access methodology. In some cases, ethernet networks with between 100 and 200 users barely use the capacity of the network. However, the nature of the data transmitted is the key to determining potential network capacity problems. Character-based transmissions, such as typical data entry, in which a few characters at a time are typed and sent over the network are much less likely to cause network capacity problems than the transfer of graphical user interface (GUI) screen oriented transmission such as Windows-based applications. CAD/CAM images are even more bandwidth intensive. Simultaneous requests for full screen Windows-based transfers by 30 or more workstations can cause collision and network capacity problems on an ethernet network. As with any data communication problem, there are always solutions or workarounds to these problems. The point in relaying these examples is to provide some assurance that although ethernet is not unlimited in its network capacity, in most cases, it provides more than enough bandwidth.
Token Ring
IBM’s token ring network architecture, adhering to the IEEE 802.5 standard, utilizes a star physical topology, sequential message delivery, and a token passing access methodology scheme. Since the sequential logical topology is equivalent to passing messages from neighbor to neighbor around a ring, the token ring network architecture is sometimes referred to as: logical ring, physical star. The token ring’s use of the token passing access methodology furnishes one of the key positive attributes of this network architecture. The guarantee of no data collisions with assured data delivery afforded by the token passing access methodology is a key selling point in some environments where immediate, guaranteed delivery is essential.
FDDI
As far as trends in network architecture go, as more and more users are attached to LANS, the demand for overall network bandwidth increases. LANs are increasing both in size and overall complexity. Internet- working of LANs of various protocols via bridges and routers means more overall LAN traffic. Network applications are driving the demand for increased bandwidth as well. The concepts of distributed comput- ing, data distribution, and client/server computing all rely on a network architecture foundation of high bandwidth and high reliability. Imaging, multimedia, and data/voice integration all require high amounts of bandwidth in order to transport and display these various data formats in real time. In other words, if full-motion video is to be transported across the LAN as part of a multimedia program, there should be sufficient bandwidth available on that LAN for the video to run at full speed and not in slow motion. Likewise, digitized voice transmission should sound normal when transported across a LAN of sufficient bandwidth.
FDDI supplies not only a great deal of bandwidth, but also a high degree of reliability and security while adhering to standards-based protocols. FDDI’s reliability comes not only from the fiber itself which, as we know, is immune to both electromagnetic interference (EMI) and radio frequency interference (RFI). An additional degree of reliability is achieved through the design of the physical topology of FDDI.
FDDI’s physical topology comprises not one, but two, separate rings around which data moves simultaneously in opposite directions. One ring is the primary data ring while the other is a secondary or backup data ring to be used only in the case of the failure of the primary ring. Whereas both rings are attached to a single hub or concentrator, a single point of failure remains in the hub while achieving redundancy in the network media. In addition to speed and reliability, distance is another key feature of an FDDI LAN. Another positive attribute of FDDI is its ability to interoperate easily with ethernet networks. In this way, a business does not have to scrap its entire existing network in order to upgrade a piece of it to FDDI.
An FDDI to ethernet bridge is the specific technology employed in such a setup.
The uses of the FDDI network architecture typically fall into three categories:
1. Campus backbone: Not necessarily implying a college campus, this implementation is used for connecting LANs located throughout a series of closely situated buildings.
2. High bandwidth workgroups: The second application category is when the FDDI LAN is used as a truly local area network, connecting a few PCs or workstations which require high bandwidth com- munication with each other. Multimedia workstations, engineering workstations, or CAD/CAM workstations are all good examples of high bandwidth workstations.
3. High bandwidth subworkgroup connections: In some cases, only two or three devices, perhaps three servers, have high bandwidth requirements. As distributing computing and data distribution increase, an increasing demand for high-speed server to server data transfer has been seen.
Wireless LANs
Many of the previously mentioned network architectures function over more than one type of media. Another media option is wireless transmission (which is really the absence of any media) for local area networks. There are currently three popular wireless transmission technologies in the local area network technology area. They are microwave transmission, spread spectrum transmission, and infrared transmission.
These are all just radio transmissions at varying frequencies.
Wireless LAN Applications
A primary application of wireless LANs optimizes the ease of access of the wireless technology. Portable or notebook PCs equipped with their own wireless LAN adapters can create an instant LAN connection merely by getting within range of a server-based wireless LAN adapter or wireless hub. In this way, a student or employee can sit down anywhere and log into a LAN as long as the user is within range of the wireless hub and has the proper wireless adapter installed in the portable PC.
Meeting rooms can be equipped with wireless hubs to allow spontaneous workgroups to log into network resources without running cables all over the meeting room. Similarly, by quickly installing wireless hubs and portable PCs with wireless adapters, temporary expansion needs or emergency/disaster recovery situations can be handled quickly and with relative ease. No rerunning of wires or finding the proper cross-connects in the wiring closet are necessary.
Finally, wireless LAN technology allows entire LANs to be preconfigured at a central site and shipped ready to run to remote sites. The nontechnical users at the remote site literally just have to plug the power cords into the electrical outlets and they have an instant LAN. For companies with a great number of remote sites and limited technical staff, such a technology is ideal. No preinstallation site visits are necessary. Also avoided are costs and supervision of building wiring jobs and troubleshooting building wiring problems during and after installation.
Local Area Network Hardware
Servers
A server’s job is to manage the sharing of networked resources among client PCs. Depending on the number of client PCs and the extent of the shared resources, it may be necessary to have multiple servers and/or to specialize some servers as to the type of resources that they manage. If servers are to be specialized, then shared resources should be grouped in some logical fashion so as to optimize the server performance for managing the sharing of a particular type of resource. A list of potentially shared network resources would probably include: files, application programs, databases, printers, access to other LANs (local), access to other LANs (remote), access to information services, and access to the LAN from remote PCs.
Hubs/Multistation Access Units (MAUs)
The heart of the star physical topology, employed by both ethernet and token ring, is the wiring center, alternatively known as a hub, a concentrator, a repeater or a multistation access unit (MAU).
Repeaters
A repeater, as its name would imply, merely repeats each bit of digital data that it receives. This repeating action actually cleans up the digital signals by retiming and regenerating them before passing this repeated data from one attached device or LAN segment to the next.
Hubs
The terms hub and concentrator or intelligent concentrator are often used interchangeably. Distinctions can be made, however, between these two broad classes of wiring centers, although there is nothing to stop manufacturers from using the terms as they wish. A hub is often the term reserved for describing a stand-alone device with a fixed number of ports, which offers features beyond that of a simple repeater. The type of media connections and network architecture offered by the hub is determined at the time of manufacture as well. For example, a 10BaseT ethernet hub will offer a fixed number of RJ-45 twisted pair connections for an ethernet network. Additional types of media or network architectures are not usually supported.
MAUs
A MAU is IBM’s name for a token ring hub. A MAU would be manufactured with a fixed number of ports and connections for unshielded or shielded twisted pair. IBM uses special connectors for token ring over shielded twisted pair (STP) connections to a MAU. MAUs offer varying degrees of management capability.
Concentrators
The term concentrator or intelligent concentrator (or smart hub) is often reserved for a device characterized by its flexibility and expandability. A concentrator starts with a fairly empty, boxlike device often called a chassis. This chassis contains one or more power supplies and a builtin network backbone. This backbone might be ethernet, token ring, FDDI, or some combination of these. Into this backplane, individual cards or modules are inserted.
For instance, an 8- or 16-port twisted pair ethernet module could be purchased and slid into place in the concentrator chassis. A network management module supporting the SNMP (simple network management protocol) network management protocol could then be purchased and slid into the chassis next to the previously installed 10BaseT Port module. In this mix and match scenario, additional cards could be added for connection of PCs with token ring adapters, PCs, or workstations with FDDI adapters, or dumb asynchronous terminals.
This network in a box is now ready for workstations to be hooked up to it through twisted pair connections to the media interfaces on the network interface cards of the PCs or workstations. Remember that ethernet can run over UTP (unshielded twisted pair), STP, thick and thin coaxial as well as fiber.
Additional modules available for some, but not all, concentrators may allow data traffic from this network in box to travel to other local LANs via bridge or router add-on modules. (Bridges and routers will be discussed in the next section on internetworking.) These combination concentrators are sometimes called internetworking hubs. Communication to remote LANs or workstations may be available through the addition of other specialized cards, or modules, designed to provide access to wide area network services purchased from common carriers.
Switching Hubs
The network in a box or backbone in a box offered by concentrators and hubs shrinks the length of the network backbone but does not change the architectural characteristics of a particular network backbone. For instance, in an ethernet concentrator, multiple workstations may access the built in ethernet backbone via a variety of media, but the basic rules of ethernet, such as CSMA/CD access methodology still control performance on this ethernet in a box. Only one workstation at a time can broadcast its message onto the shared backbone.
A switching hub seeks to overcome this one at a time broadcast scheme, which can potentially lead to data collisions, retransmissions, and reduced throughput between high-bandwidth demanding devices such as engineering workstations or server-to-server communications.
The ethernet switch is actually able to create connections, or switch, between any two attached ethernet devices on a packet by packet basis. The one-at-time broadcast limitation previously associated with ethernet is overcome with an ethernet switch.
Wiring Centers Technology Analysis
Some of the major technical features to be used for comparative analysis are listed in Fig. 19.61. Before purchasing a hub of any type, consider the implications of these various possible features. To summarize, the following major criteria should be thoroughly considered before a hub or concentrator purchase:
(1) expandability (2) supported network architectures (3) supported media types (4) extended communications capabilities, that is, terminal support, internetworking options, and wide area networking options, (5) hub/concentrator management capabilities and (6) reliability features.
Network Interface Cards
Network adapter cards, also known as network interface cards are the physical link between a client or server PC and the shared media of the network. Providing this interface between the network and the PC or workstation requires that the network adapter card have the ability to adhere to the access methodology (CSMA/CD or token passing) of the network architecture to which it is attached. These software rules, implemented by the network adapter card which control the access to the shared network media, are known as media access control (MAC) protocols and are represented on the MAC sublayer of the data link layer (layer 2) of the OSI 7-layer reference model.
Since these are MAC layer interface cards and are, therefore, the keepers of the MAC layer interface protocol, it is fair to say that it is the adapter cards themselves that determine network architecture and its constituent protocols more than any other component. Take an ethernet adapter card out of the expansion slot of a PC and replace it with a token ring adapter card and you have a token ring workstation. In this same scenario, the media may not even need to be changed since ethernet, token ring, and FDDI/CDDI often work over the same media.
Role of Adapter Card Drivers
Assuring that the purchased adapter card interfaces successfully to the bus of the CPU as well as the chosen media of the network architecture will as sure hardware connectivity. Full interoperability, however, depends on the chosen network adapter card being able to communicate successfully with the network operating system and operating system of the PC into which it is installed.