Internetworking
Applications: What Can Internetworking Do for You?
It is nearly inevitable that sooner or later nearly any organization will need to share information across multiple information platforms or architectures. This sharing may be between LANs that may differ in net- work architecture or network operating systems. Information systems that combine multiple computing platforms or a variety of network architectures and network operating systems are often referred to as enterprise computing environments. Underlying this enterprise computing environment is an enterprise network or internetwork. The key to successful internetworking is that to the end user sitting at a LAN-attached workstation, the connectivity to enterprise computing resources should be completely transparent.
In other words, an end user should not need to know the physical location of a database server or disk drive to which they need access. All the user needs to know is a node name or drive indicator letter and the fact that when these node name or drive letters are entered, data is properly accessed from wherever it may be physically located. That physical location may be across the room or across the country.
As information has become increasingly recognized as a corporate asset to be leveraged to competitive advantage, the delivery of that information in the right form, to the right person at the right place and time has become the goal of information systems and the role of internetworking. Mergers, acquisitions, and enterprise partnerships have accelerated the need to share information seamlessly across geographic or physical LAN boundaries. Intelligent inter-LAN devices perform the task of keeping track of what network attached resources are located and where and how to get a packet of data from one LAN to another. This task is further complicated by the fact that LANS can differ in any of the following categories: (1) network architecture, (2) media, (3) network operating system, and (4) operating system.
This collection of differences is defined by rules or protocols that define how certain clearly defined aspects of network communications are to take place. When LANs that need to share information operate according to different protocols, an inter-LAN device that has protocol conversion capabilities must be employed. In cases such as this, the inter-LAN device would be transmitting data across logical, as opposed to physical or geographic, boundaries. Among the inter-LAN devices which will be explored in this section
are repeaters, bridges, routers, and gateways. Although the differences in functionality of these devices will be distinguished from a technical standpoint, there is no guarantee that manufacturers will follow this differentiation. Functional analysis of data communications devices is the best way to assure that inter-LAN devices will meet internetworking connectivity needs. Internetworking analysis and design is a highly complex and confusing area of study. The purpose of this section is to familiarize the reader with internetworking technology and applications and to provide a list of resources for further study.
The OSI Model and Internetworking Devices
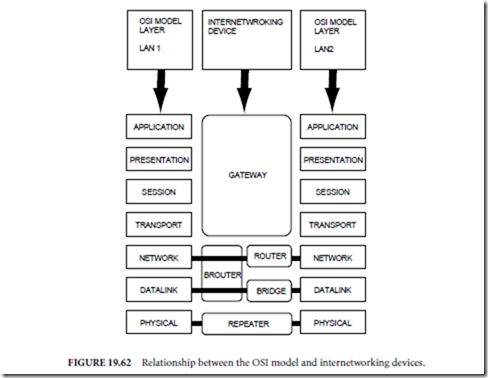
The OSI model was first introduced in Sec. 19.7.1 as a common framework or reference model within which protocols and networking systems could be developed with some assurance of interoperability. In this section, the OSI model provides a most effective framework in which to distinguish between the operational characteristics of the previously mentioned internetworking devices. Figure 19.62 depicts the relationship between each type of internetworking device and its related OSI layer. Each device as well as the related OSI model layer will be explained in detail.
Internetworking Technology
Repeaters: Layer 1—The Physical Layer
Remember that all data traffic on a LAN is in a digital format of discrete voltages of discrete duration traveling over one type of physical media or another. Given this, a repeater’s job is fairly simple to understand:
1. Repeat the digital signal by regenerating and retiming the incoming signal.
2. Pass all signals between all attached segments.
3. Do not read destination addresses of data packets.
4. Allow for the connection of different types of media.
5. Effectively extend overall LAN distance by repeating signals between LAN segments.
A repeater is a nondiscriminatory internetworking device. It does not discriminate between data pack- ets. Every signal which comes into one side of a repeater gets regenerated and sent out the other side of the repeater. Repeaters are available for both ethernet and token ring network architectures for a wide variety of media types. A repeater is a physical layer device concerned with physical layer signaling protocols relating to signal voltage levels and timing. It cannot distinguish between upper layer protocols such as between ethernet vs. token ring frames (layer 2 , data link protocols). Therefore, repeaters must be specifically manufactured for either ethernet or token ring network architectures. The primary reasons for employing a repeater are (1) increase the overall length of the network media by repeating signals across multiple LAN segments, (2) isolate key network resources onto different LAN segments, and (3) some repeaters also allow network segments of the same network architecture but different media (layer 1—physical) types to be interconnected.
Bridges: Layer 2—The Data Link Layer
Bridge Functionality
The primary reasons for employing bridges are (1) network traffic on a LAN segment has increased to the point where performance is suffering, and (2) access from the departmental LAN to the corporate LAN backbone needs to be controlled so that local LAN data is not unnecessarily causing congestion problems on the corporate backbone network.
By dividing users across multiple LAN segments connected by a bridge, a substantial reduction in LAN traffic on each segment can be achieved provided the division of users is done in a logical manner. Users should be divided according to job function, need to communicate with each other, and need to access data stored on particular servers. The rule of thumb for segmenting users is that 80% of LAN traffic should remain within the LAN segment and only about 20% should cross the bridge to adjacent LAN segments. Controlling access to the corporate backbone via a bridge can ensure the viability of enterprise communications by only allowing essential network communication onto the corporate backbone. Servers and other internetworking devices can be connected directly to the corporate backbone while all user’s workstations are connected to LAN segments isolated from the corporate backbone by bridges.
When users on one LAN need occasional access to data or resources from another LAN, an internetworking device, which is more sophisticated and discriminating than a repeater, is required. From a comparative standpoint on the functionality of bridges vs repeaters, one could say that bridges are more discriminating. Rather than merely transferring all data between LANs or LAN segments like a repeater, a bridge reads the destination address of each data frame on a LAN, decides whether the destination is local or remote (on the other side of the bridge), and only allows those data frames with nonlocal destination addresses to cross the bridge to the remote LAN.
How does the bridge know whether a destination is local or not? Data-link protocols such as ethernet contain source addresses as well as destination addresses within the predefined ethernet frame layout. A bridge also checks the source address of each frame it receives and adds that source address to a table of known local nodes. After each destination address is read, it is compared with the contents of the known local nodes table in order to determine whether the frame should be allowed to cross the bridge or not (whether the destination is local or not). Bridges are sometimes known as a forward-if-not-local device.
This reading, processing, and discriminating indicates a higher level of sophistication of the bridge, afforded by installed software.
Bridge Categorization
Bridges come in many varieties. Physically, bridges may be cards that can be plugged into an expansion slot of a PC, or they may be standalone devices. Although it is known that the bridge will do the internetwork processing between two LANs, the exact nature of that processing, as well as the bridge’s input and output interfaces, will be determined by the characteristics of the two LANs that the bridge is internetworking. In determining the attributes of the input and output bridge one must consider the following issues: MAC sublayer protocol, speed of LANs, local or remote, and wide area network services and media.
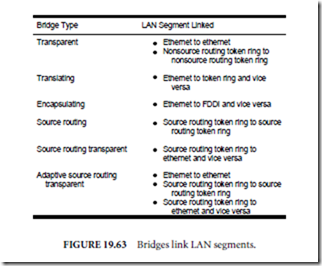
1. MAC Sub-Layer Protocol: Depending on the MAC sublayer or network architecture of the LANs to be bridged, any of the following types of bridges may be required: transparent bridges, translating
bridges, encapsulating bridges, source routing bridges, source routing transparent bridges, and adaptive source routing transparent bridges. First and foremost, are the two LANs which are to be bridged ethernet or token ring? Bridges that connect LANs of similar data link format are known as transparent bridges. A special type of bridge that includes a format converter can bridge between ethernet and token ring. These special bridges may also be called multiprotocol bridges or translating bridges. A third type of bridge, somewhat like a translating bridge, is used to bridge between ethernet and FDDI networks. Unlike the translating bridge, which must actually manipulate the data-link layer message before repackaging it, the encapsulating bridge merely takes the entire ethernet data link layer message and stuffs it in an envelope (data frame) that conforms to the FDDI data-link layer protocol. Source routing bridges are specifically designed for connecting token ring LANs. Bridges that can support links between source routing token ring LANs and nonsource routing LANs, such as ethernet, are known as source routing transparent bridges. Finally, bridges that can link transparent bridged ethernet LAN segments to each other, source routing token ring LAN segments to each other, or any combination of the two are known as adaptive source routing transparent bridges. Figure 19.63 outlines these various bridge possibilities.
2. Speed of LANs: The speeds of the input and output LANs must be known in order to determine what speed conversion, if any, must be performed by our bridge.
3. Local or Remote: Having determined the MAC layer protocol and speed of the LANs, their geo- graphic proximity to one another must be taken into consideration. If the two LANs are not in close enough proximity to link via traditional LAN media such as UTP, coax, or fiber, the bridge must be equipped with an interface appropriate for linking to wide area carrier services.
Bridge Performance
Bridge performance is generally measured by two criteria:
1. Filtering rate: Measured in packets per second or frames per second. When a bridge reads the destination address on an ethernet frame or token ring packet and decides whether or not that packet should be allowed access to the internetwork through the bridge, that process is known as filtering.
2. Forwarding rate: Also measured in packets per second or frames per second. Having decided whether or not to grant a packet access to the internetwork in the filtering process, the bridge now must perform a separate operation of forwarding the packet onto the internetwork media whether local or remote.
Bridges, Protocols, and the OSI Model
Bridges read the destination addresses within data frames of a predefined structure or protocol. In other words, ethernet and token ring network architectures define a bit-by-bit protocol for formation of data frames. The bridge can rely on this protocol and, therefore, knows just where to look within the ethernet data frames to find the bits, which represent the destination addresses. In terms of the OSI model, ethernet and token ring are considered MAC sublayer protocols. The MAC sublayer is one of two sublayers of OSI model layer 2—the data link layer. The other data link sublayer is known as the logical link control sublayer. Because the protocols that a bridge reads and processes are located on the MAC sublayer, bridges are sometimes referred to as MAC layer bridges.
Embedded within the data field of the ethernet frame are all of the higher OSI layer protocols. These higher layer protocols can vary independently of the data-link layer ethernet protocol. In other words, the data-link layer protocols such as ethernet and token ring are network architectures, whereas the network layer protocols could be from any one of a number of different network operating systems. Bridges only pay attention to network architecture (MAC sublayer) protocols or formats. They completely ignore upper level protocols.
Most network operating systems actually consist of stacks of protocols. In some cases, this protocol stack may consist of a separate protocol for each of layers 3–7. Each protocol of a network operating system performs a different networking related function corresponding to the generalized functional definition for the corresponding layer of the OSI model. As an example, the network layer protocol for TCP/IP suite of protocols is known as internet protocol (IP).
Routers: The Network Layer Processors
The delivery of data packets to destination addresses across multiple LANs, and perhaps over wide area network links, is the responsibility of a class of internetworking devices known as routers. Routers are primarily employed for the following reasons:
1. To build large hierarchical networks. Routers are used to create the backbone network itself.
2. To take part in or gain access to a larger hierarchical network such as the Internet.
Router Functionality
Although they both examine and forward data packets, routers and bridges differ significantly in two key functional areas. First, although a bridge reads the destination address of every data packet on the LAN to which it is attached, a router only examines those data packets that are specifically addressed to it. Second, rather than just merely allowing the data packet access to the internetwork in a manner similar to a bridge, a router is more cautious as well as more helpful. Before indiscriminately forwarding a data packet, a router first confirms the existence of the destination address as well as the latest information on available network paths to reach that destination. Next, based on the latest traffic conditions, the router chooses the best path for the data packet to reach its destination and sends the data packet on its way. The word best is a relative term, controlled by a number of different protocols, which will be examined shortly.
The router itself is a destination address, available to receive, examine, and forward data packets from anywhere on any network to which it is either directly or indirectly internetworked. The destination address on an ethernet or token ring packet must be the address of the router that will handle further internetwork forwarding. Thus, a router is addressed in the data-link layer destination address field. The router then discards this MAC sublayer envelope, which contained its address, and proceeds to read the contents of the data field of the ethernet or token ring frame.
Just as in the case of the data-link layer protocols, network layer protocols dictate a bit-by-bit data frame structure that the router understands. What looked like just data and was ignored by the data-link layer internetworking device (the bridge) is unwrapped by the router and examined thoroughly in order to determine further processing. After reading the network layer destination address and the protocol of the network layer data, the router consults its routing tables in order to determine the best path on which to forward this data packet. Having found the best path, the router has the ability to repackage the data packet as required for the delivery route (best path) it has chosen.
As an example, if a packet switched data network was chosen as the wide area link for delivery, then the local router would encapsulate the data packet in compliant envelope. On the other hand, if the best path was over a local ethernet connection, the local router would put the data packet back into a fresh ethernet envelope and send it on its way.
Unlike the bridge, which merely allows access to the internetwork (forward-if-not-local logic), the router specifically addresses the data packet to a distant router. Before a router actually releases a data packet onto the internetwork, however, it confirms the existence of the destination address to which this data packet is bound. Only once the router is satisfied with both the viability of the destination address, as well as with the quality of the intended path, will it release the carefully packaged data packet. This meticulous processing activity on the part of the router is known as forward-if-proven-remote logic.
Determination of Best Path
The best path can take into account variables such as
1. Number of intermediate hops. That is, how many other routers will the packet have to be processed by before it reaches its final destination? Every router takes time to process the data packet. Therefore, the fewer the routers, the faster the overall delivery.
2. The speed or condition of the communications circuits. Routers can dynamically maintain their routing tables keeping up to the minute information on network traffic conditions.
3. The protocol of the network operating system, for instance, remembering that multiple protocols can be sealed within ethernet envelopes. We may ask the router to open the ethernet envelopes and forward all NetWare (IPX) traffic to one network and all TCP/IP (IP) to another. In some cases, a certain protocol may require priority handling.
Multiprotocol Routers
Routers are made to read specific network layer protocols in order to maximize filtering and forwarding rates. If a router only has to route one type of network protocol, then it knows exactly where to look for destination addresses every time and can process packets much faster. However, realizing that different network layer protocols will have different packet structures with the destination addresses of various lengths and positions, some more sophisticated routers known as multiprotocol routers have the capability to interpret, process, and forward data packets of multiple protocols.
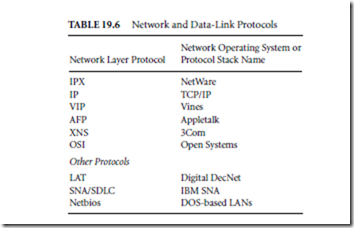
Some common network layer protocols and their associated network operating systems or upper layer protocols as well as other protocols which are actually data-link control protocols processed by some routers are listed in Table 19.6. Remembering that bridges are used to process data-link layer protocols, those routers that can also perform the functionality of a bridge are called bridging routers or brouters.
Like bridges, routers generally take one of the two physical forms: (1) stand-alone variety, self-contained; and (2) modularized for installation in a slotted chassis. Routers may be installed to link LAN segments either locally or remotely. Boundary routing recognizes the need for simple, affordable wide area network devices at remote offices while providing full routing capabilities throughout the wide area network. Bound- ary routing’s physical topology is sometimes referred to as a hub and spoke topology due to the fact that each remote branch is connected to a hub office via a single WAN link. If redundant links are a business requirement of a particular node, then it must be a full-function router and not a boundary router in this topology. Full-function routers are placed at each hub or central node, while less sophisticated boundary routers, or branch-office routers, are placed at each remote or spoke node. Since there are only connected to a single WAN link, these boundary routers make only one decision when examining each piece of data, “If these data are not addressed to a local destination, then it should be forwarded.” This forward-if-not-local logic should suggest that, in fact, these boundary routers are acting as bridges.
Gateways
Recalling that in terms of the OSI model, repeaters are considered a physical layer (layer 1) device, bridges are considered a data-link layer (layer 2) device, and routers are considered a network layer (layer 3) device, it could be said that gateways provide for interoperability on the session, presentation, and application layers (layers 5–7). Whereas repeaters, bridges and routers provide increasingly more sophisticated connection between two LANs, gateways provide transparent connection between two totally different computing environments. Specialized gateways also translate between different database management systems and are called database gateways, or between different e-mail systems and are called e-mail gateways.
The gateway is usually a computer with physical connections to both computing environments to be linked. In addition, the gateway also executes specially written software, which can translate messages between the two computing environments. Unlike other internetworking devices described, gateways are more concerned with translation than with processing destination addresses and delivering messages as efficiently as possible.