19.7 Network Communication
19.7.1 General Principles of Network Analysis and Design
Use of Top-Down Business Oriented Approach
Network communication is the transport of data, voice, video, image, or facsimile (fax) from one location to another achieved by compatibly combining elements of hardware, software, and media. From a business perspective, network communications is delivering the right information to the right decision maker at the right place and time for the right cost. Because there are so many variables involved in the analysis, design, and implementation of such networks, a structured methodology must be followed in order to assure that the implemented network meets the communications needs of the intended business, organization, or individual.
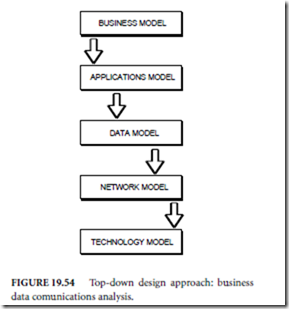
One such structured methodology is known as the top-down approach. Such an approach can be graphically illustrated in a top-down model as shown in Fig. 19.54. Using a top-down approach as illustrated in the top-down model is relatively straight- forward.
One must start with the business level objectives. What is the company (organization, individual) trying to accomplish by installing this network? With- out a clear understanding of business level objectives, it is nearly impossible to configure and implement a successful network.
Once business level objectives are understood, one must understand the applications which will be running on the computer systems attached to these networks. After all, it is the applications that will be generating the traffic that will travel over the implemented network.
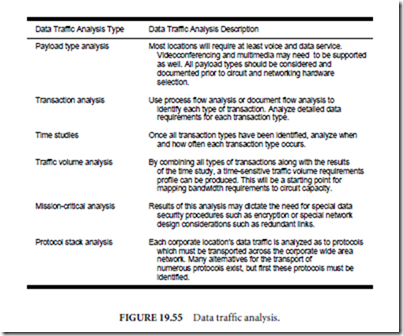
Once applications are understood and have been documented, the data which those applications generate must be examined. In this case, the term data is used in a general sense as today’s networks are likely to transport a variety of payloads including voice, video, image, and fax in addition to true data. Data traffic analysis must determine not only the amount of data to be transported, but also must determine important characteristics about the nature of that data. A summarization of data traffic analysis is outlined in Fig. 19.55. It is also during this stage of the top-down analysis in which the geographic proximity of the nodes of the network are examined.
Geographic proximity is one differentiating factor among different categories of networking, which will be examined further subsequently.
Once data traffic analysis has been completed, the following should be known:
1. Physical locations of data (Where?)
2. Data characteristics and compatibility issues (What?)
3. Amount of data generated and transported (How much?)
Given these requirements as determined by the upper layers of the top-down model, the next job is to determine the requirements of the network that will possess the capability to deliver this data in a timely, cost-effective manner. Details on the determination of these requirements comprise the remainder of this section on network communications. These network performance criteria could be referred to as what the implemented network must do in order to meet the business objectives outlined at the outset of this top-down analysis. These requirements are also sometimes referred to as the logical network design.
The technology layer analysis, in contrast, will determine how various hardware and software components will be combined to build a functional network which will meet predetermined business objectives. The delineation of required technology is often referred to as the physical network design.
Overall, the relationship between the layers of the top-down model could be described as follows: analysis at upper layers produces requirements that are passed down to lower layers while solutions meeting these requirements are passed back to upper layers. If this relationship among layers holds true throughout the business oriented network analysis, then the implemented technology (bottom layer) should meet the initially outlined business objectives (top layer).
Use of Open Systems Interconnection (OSI) Model
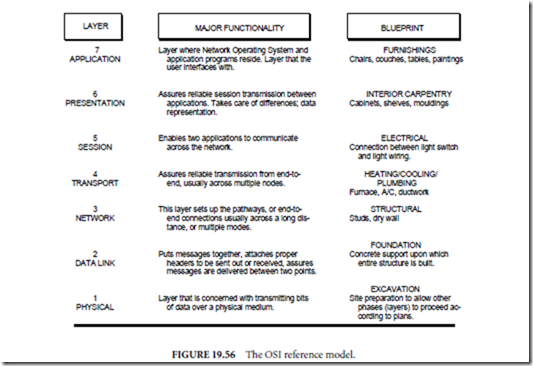
Determining which technology to employ to meet the requirements determined in the logical network de- sign (network layer) requires a structured methodology of its own. Fortunately, a framework for organizing networking technology solutions has been developed by the International Standards Organization (ISO) and is known as the open systems interconnection (OSI) model. The OSI model is illustrated in Fig. 19.56. The OSI model divides the communication between any two networked computing devices into seven layers or categories. The OSI model allows data communications technology developers as well as standards developers to talk about the interconnection of two networks or computers in common terms without dealing in proprietary vendor jargon.
These common terms are the result of the layered architecture of the seven-layer OSI model. The architecture breaks the task of two computers communicating to each other into separate but interrelated tasks, each represented by its own layer. As can be seen in Fig. 19.56, the top layer (layer 7) represents the application program running on each computer and is therefore aptly named the application layer. The bottom layer (layer 1) is concerned with the actual physical connection of the two computers or networks and is therefore named the physical layer. The remaining layers (2–6) may not be as obvious but, nonetheless, represent a sufficiently distinct logical group of functions required to connect two computers, as to justify a separate layer.
To use the OSI model, a network analyst lists the known protocols for each computing device or network node in the proper layer of its own seven-layer OSI model. The collection of these known protocols in their proper layers in known as the protocol stack of the network node. For example, the physical media employed, such as unshielded twisted pair, coaxial cable, or fiber optic cable, would be entered as a layer 1 protocol, whereas ethernet or token ring network architectures might be entered as a layer 2 protocol.
Other examples of possible protocols in respective layers will be explored in the remainder of this section. The OSI model allows network analysts to produce an accurate inventory of the protocols present on any given network node. This protocol profile represents a unique personality of each network node and gives the network analyst some insight into what protocol conversion, if any, may be necessary in order to get any two network nodes to communicate successfully. Ultimately, the OSI model provides a structured methodology for determining what hardware and software technology will be required in the physical network design in order to meet the requirements of the logical network design.
Perhaps the best analogy for the OSI reference model, which illustrates its architectural or framework purpose, is that of a blueprint for a large office building or skyscraper. The various subcontractors on the job may only be concerned with the layer of the plans that outlines their specific job specifications. However, each specific subcontractor needs to be able to depend on the work of the lower layers subcontractors just as the subcontractors of the upper layers depend on these subcontractors performing their function to specification. Similarly, each layer of the OSI model operates independently of all other layers, while depending on neighboring layers to perform according to specification while cooperating in the attainment of the overall task of communication between two computers or networks.
Differentiation Among Major Categories of Networking
As part of the top-down analysis, geographic proximity of computers or network nodes was mentioned as a key piece of analysis information. Although there are no hard and fast rules for network categorization, following are a few of the more common categories of networking:
✁ Remote connectivity: A single remote user wishes to access local network resources. This type of networking is particularly important to mobile professionals such as sales representatives, service technicians, field auditors, etc.
✁ Local area networking: Multiple users’ computers are interconnecting for the purpose of sharing applications, data, or etworked technology such as printers or CD-ROMs. Local area networks (LANs) may have anywhere from two or three users to several hundred. LANs are often limited to a single department or floor in a building, although technically any single location corporation could be networked via a LAN.
✁ Internetworking: Also known as LAN-to-LAN networking or connectivity, internetworking involves the connection of multiple LANs and is very common in corporations in which users on departmental LANs now need to share data or otherwise communicate. The challenge of internet working is in getting departmental LANs of different protocol stacks (as determined by use of the OSI model) to talk to each other, while only allowing authorized users access to the internetwork and other LANs. Variations of internetworking also deal with connecting LANs to mainframes or minicomputers rather than to other LANs.
✁ Wide area networking: Also known as enterprise networking, involves the connection of computers, network nodes, or LANs over a sufficient distance as to require the purchase of wide area network (WAN) service from the phone company or alternative carrier. In some cases, the wide area portion of the network may be owned and operated by the corporation itself. Nonetheless, the geographic distance between nodes is the determining factor in categorizing a wide area network. A subset of WANs known as metropolitan area networks (MANs) are confined to a campus or metropolitan area of usually not more than a few miles in diameter.
The important thing to remember is that categorization of networking is somewhat arbitrary and that what really matters is that the proper networking technology (hardware and software) is specified in any given networking opportunity in order to meet stated business objectives.
19.7.2 Personal Remote Connectivity
Applications
The overall methodology for analysis and design of remote connectivity networking can be summarized as follows:
1. Needs analysis
2. Logical topology choice
3. Physical topology or architecture choice
4. Technology review and specification
Remote Connectivity Needs Analysis
Remote connectivity needs analysis involves documenting the nature and extent of the use of local LAN resources by the remotely connected user. Choices of logical or physical topology for this remote LAN connectivity may be limited depending on the outcome of the remote connectivity needs analysis. Among the possible information sharing needs of remote users are the following: (1) exchange e-mail, (2) upload and download files, (3) run interactive application programs remotely, and (4) utilize LAN attached resources such as printers. One additional question will have a direct impact on topology choice: (5) How many remote users will require simultaneous access to local LAN attached resources?
Remote connectivity architectures comprise the combination of a chosen remote connectivity logical topology and a chosen remote connectivity physical topology.
Logical Topologies
Remote connectivity logical topologies are differentiated by: (1) location of application program execution (local or remote PC) and (2) nature of the data traffic between the local and remote PC. The two most common remote connectivity logical topologies or operations modes are: (1) remote client mode and (2) remote control mode.
Remote Client Mode
Remote client mode, alternatively known as remote access node, executes and often stores applications on the remote PC, using only shared data and other locally attached LAN resources connected to the local LAN server. A single local LAN server or specialized communications server can service multiple remote PC clients. The remote node has the same full capabilities as any local node on the network. The fact that the client PC is remote to the local server is transparent. The data traffic between the remote PC and local LAN server are data packets particular to the network operating system, which both the remote PC and local LAN server have installed.
Remote Control Mode
Remote control mode requires a dedicated local PC to be assigned to each remote PC since applications are stored and executed on the local PC. Shared data and other LAN-attached resources are accessed from the LAN server through the local PC. The remote PC is really nothing more than a simple input/output device. All processing is performed on the local PC. Only keystrokes and screen images are transmitted between the remote PC and the local PC. This setup is really just a remote keyboard and monitor for a local PC. The remote PC controls the local PC and all of its LAN attached resources, hence the name, remote control mode.
Figure 19.57 outlines some of the details, features and requirements of these two remote PC modes of operation or logical topologies.
Physical Topologies
Remote connectivity physical topologies refer to the physical arrangement of hardware and media which offers access to the local LAN for the remote user. As Fig. 19.58 illustrates, there are three basic ways in which a remote PC user can gain access to the local LAN resources. (1) a LAN attached PC, (2) communications server, and (3) LAN modem.
It is important to understand that the actual implementation of each of these LAN access arrangements may require additional hardware and/or software. They may also be limited in their ability to utilize all LAN attached resources.