Architectures and elements
Some distributed control systems are used in electrical power grids or electrical generation facilities. Others are used in environmental control systems, wastewater treatment plants, and sensor networks. Distributed control systems for petroleum refineries and petrochemical plants are also common.
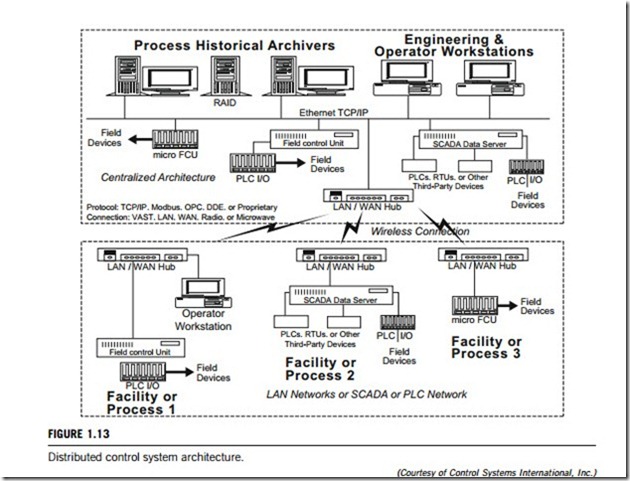
In industrial applications, different structures of distributed control systems (DCS) exist. They include fully distributed control, hybrid distributed control, open distributed control, closed distributed control, computerized distributed control, wireless distributed control, and so on. Each type has a different DCS architecture. Figure 1.13 is a graphic configuration of all distributed control system architectures. In the diagram, the upper box shows fully distributed and closed architectures (where centralized architecture means centralized distributed architecture, which is different from the centralized control system architecture mentioned earlier); the middle part depicts wireless connec- tions in distributed control systems; the lower box shows that there are control networks in distributed control systems. These control networks include local area networks (LANs), SCADA networks, PLC networks, etc. The whole of Figure 1.13 illustrates an open and hybrid distributed control system architecture.
(1) Hardware components
(a) Operator interfaces
The operator interface features high-resolution graphics and graphical user interface (GUI) windows. Its responsibilities are: to allow operators to monitor detailed activities of many types of device and send commands using command windows and group displays; to display project screens created during project development and makes them dynamic based on real-time data; to log and display alarms and other event messages, and let operators acknowledge alarms; to show trends in real-time and historical data; to allow authorized operators to monitor and override device logics; to display the status of communication between the devices and components, which helps the operator diagnose the cause of communication interrupts.
(b) I/O subsystem
It is necessary for distributed control systems to support standard, off-the-shelf I/O subsystems, so that the same logic can be used to manipulate different I/O subsystems without the need to change programming or operational parameters of the configured system. This allows a distributed control system to replace another without requiring replacement of the I/O subsystem. In addition, when the I/O subsystem is replaced, no change in logic is required since distributed control system logic can be hardware-independent.
(c) Connection buses
In distributed control systems, Ethernet is a local area network (LAN) protocol that uses a bus or star typology and supports data transfer rates of 10 Mbps. To handle simultaneous demands, Ethernet uses carrier sense multiple access/collision detection (CSMA/CD) to monitor network traffic.
Fieldbus is a bi-directional communication protocol used for communications among field instrumentation and control systems. The process Fieldbus (PROFIBUS®) is a popular, open com- munication standard used in factory automation, process automation, motion control, and safety applications.
Network protocols for distributed control systems (DCS) also include controller area network bus (CANbus), control network (ControlNet), DeviceNet, INTERBUS, and PROFIBUS, and other protocols.
(d) Field control units
Field elements are controlled by PLC, PC or remote terminal units running under any operating system. The controller software executes sequential and regulatory control schemes that are down- loaded from the engineering workstation. It also provides real-time scanning and control of remote I/O. The SCADA Data Server is another component to communicate with devices that cannot be directly scanned by the PLC or remote terminal units. The SCADA data server is a generalized, flexible, and user-configurable application designed to interface to other control systems, proprietary protocol drivers, or specialized software.
(e) Wireless subsystem
If replacing Ethernet and some connection buses with wireless Ethernet and wireless connections in a distributed control system, it will thereby contain a wireless subsystem. In most applications, wireless subsystems are used for remote communication between parts of the distributed control system which are physically distant.
(f) Component redundancy
Most advanced distributed control systems support selective redundancy at all levels, including redundant field controllers, field buses, and redundant I/O components.
(2) Software modules
(a) History module
This module stores the configurations of the distributed control system, as well as the configurations of all the points in the controlled system. It also stores the graphic files that are shown on the console and in most systems. These files can be used to store some operating data of the control systems and of the controlled systems. All the data stored and managed by the history module can be kept on hard disks in the PC used as the operator interface.
(b) Control modules
These modules carry out control functions on the target systems. They are the brain of a distributed control system. Custom function blocks are especially found in these modules, and are responsible for operating control algorithms such as PID, fuzzy-logic, ratio control, simple arithmetic and dynamic compensation, and more advanced control features.
(c) I/O modules
These modules manage the input and output of a distributed control system. The input and output can be digital or analog.On and off, start and stop signals are examples of digital I/O modules. Most process measurements and controller outputs are I/O modules analog. These points are hardwired with the field elements.
(3) Network models
(a) The Ethernet LAN model
Ethernet is the most common physical layer in distributed control systems, but it is also used as the transport mechanism in a distributed control system. The Ethernet network protocols are referred to as TCP/IP. This set of protocols accommodates different kinds of data for different applications.
Ethernet provides communication at a faster data rate on an office LAN. A remote hard drive is just as accessible as a local one because the network is able to deliver the requested data quickly. Fast Ethernet 100BASE-Y and Gigabit Ethernet, are the two kinds of Ethernet most used in distributed control systems.
Fast Ethernet 100BASE-T is 10BASE-T with the original Ethernet Media Access Controller (MAC) at 10 times the speed. It allows three physical-layer implementations, all part of IEEE 802.3u: 100BASE-TX, which has two pairs of Category 5 UTP or Type 1 STP cabling and is most popular for horizontal connections; 100BASE-FX, which has two strands of multimode fibre and is most popular for vertical or backbone connections; 100BASE-T4, which has four pairs of Category 3 or better cabling and is not common.
Gigabit or 1000-Mb Ethernet is the 1998 IEEE 802.3z standard and includes the Gigabit Ethernet MAC and three physical layers. Gigabit uses 8B/10B encoding and encompasses four physical standards: 1000BASE-SX Fibre (horizontal fibre), 1000BASE-LX Fibre (vertical or campus back- bone), 1000BASE-CX Copper, and 1000BASE-T.
(b) The OSI network model
The standard model for networking protocols and distributed applications is the International Standard Organization’s Open System Interconnect (ISO/OSI) model. It defines seven network layers.
Layer 1 is Physical. The physical layer defines the cable or physical medium itself. All media are functionally equivalent. The main difference is in convenience and cost of installation and mainte- nance. Converters (digital to analog and vice versa) from one media to another operate at this level.
Layer 2 is Data Link. The data link layer defines the format of data on the network: a network data frame, or packet, includes checksum, source and destination address, and data. The largest packet that can be sent through a data link layer defines the Maximum Transmission Unit (MTU). The data link layer handles the physical and logical connections to the packet’s destination, using a network interface. A host connected to an Ethernet would have an Ethernet interface to handle connections to the outside world, and a loopback interface to send packets to it.
Layer 3 is Network. NFS uses Internetwork Protocol (IP) as its network layer interface. IP is responsible for routing, and directing a datagram from one network to another. The network layer may have to break large datagrams, larger than the MTU, into smaller packets, and the host receiving the packet will have to reassemble the fragmented datagram. The Internetwork Protocol identifies each host by a 32-bit IP address. IP addresses are written as four, dot-separated, decimal numbers between 0 and 255. The leading 1-3 bytes of the IP address identify the network, and the remaining bytes identify the host on that network. For large sites, the first two bytes represents the network portion of the IP address, and the third and fourth bytes identify the subnet and host respectively. Even though IP packets are addressed using IP addresses, hardware addresses must be used to actually transport data from one host to another. The Address Resolution Protocol (ARP) is used to map between IP addresses and hardware addresses.
Layer 4 is Transport. The transport layer subdivides the user-buffer into network-buffer sized datagrams and enforces desired transmission control. Two transport protocols, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), sit at the transport layer. Reliability and speed are the primary difference between the two protocols. TCP establishes connections between two hosts on the network through sockets, which are determined by the IP address and port number. TCP keeps track of packet delivery order and of which packets that must be resent. Maintaining this information for each connection makes TCP a state protocol. UDP on the other hand provides a low overhead transmission service, but with less error checking. NFS is built on top of UDP because of its speed and statelessness. Statelessness simplifies crash recovery.
Layer 5 is Session. The session protocol defines the format of data sent over the connections. NFS uses the Remote Procedure Call (RPC) for its session protocol. RPC may be built on either TCP or UDP. Login sessions use TCP, whereas NFS and broadcast use UDP.
Layer 6 is Presentation. External Data Representation (XDR) sits at the presentation level. It converts a local representation of data to its canonical form, and vice versa. The canonical form uses a standard byte ordering and structure packing convention, independent of the host.
Layer 7 is Application. This layer provides the network with services to the end-users. Mail, FTP, telnet, DNS and NFS are examples of network applications.
(c) The TCP/IP network model
It is generally agreed that the TCP/IP model should have fewer levels than the seven of the OSI model. Most descriptions present from three to five layers. The structure of TCP/IP is built as information is passed down from applications to the physical network layer. When data are sent, each layer treats all of the information it receives from the layer above as data, and puts control information at the front of that data. This control information is called a header, and the addition of a header is called encapsulation. When data are received, the opposite procedure takes place as each layer removes its header before passing the data to the layer above. This textbook gives a TCP/IP model of four layers.
The top layer of the TCP/IP model is the application layer. In TCP/IP the application layer includes the functions of OSI presentation layer and session layer. In this book, we follow the convention that an application is any process that occurs above the transport layer, including all processes that involve user interaction. The application determines the presentation of the data, and controls the session. In TCP/IP the terms, socket and port are used to describe the path over which applications communicate. There are numerous application-level protocols in TCP/IP, including Simple Mail Transfer Protocol (SMTP) and Post Office Protocol (POP), which are used for e-mail, Hyper Text Transfer Protocol (HTTP) used for the World-Wide Web, and File Transfer Protocol (FTP). Most application-level protocols are associated with one or more port number.
The layer below the application layer is the transport layer. In the TCP/IP model, there are two transport layer protocols. The Transmission Control Protocol (TCP) guarantees that information is received as it was sent. The User Datagram Protocol (UDP) performs no end-to-end reliability checks.
The layer below the transport layer is the internet layer. In the OSI Reference Model the network layer isolates the upper layer protocols from the details of the underlying network, and manages the connections across the network. The Internet Protocol (IP) is normally described as the TCP/IP network layer. Because of the inter-networking emphasis of TCP/IP this is commonly referred to as the internet layer. All upper and lower layer communications travel through IP as they are passed through the TCP/IP protocol stack.
The lowest layer is the network access layer. In TCP/IP the data link layer and physical layer are normally grouped together. TCP/IP makes use of existing data link and physical layer standards rather than defining its own. The data link layer describes how IP utilizes existing data link protocols such as Ethernet, Token Ring, FDDI, HSSI, and ATM. The characteristics of the hardware that carries the communication signal are typically defined by the physical layer. This describes attributes such as pin configurations, voltage levels, and cable requirements. Examples of physical layer standards are RS-232C, V.35, and IEEE 802.3.
Related posts:
Incoming search terms:
- Elements of distributed control system
- control layer in dcs
- different data sokets for diatributed control system
- explain architecture of DC
- explain with DCS architecture
- layer of distrubuted control system
- use of data sockets for distributed control
- use of different data sockets for distributed control system