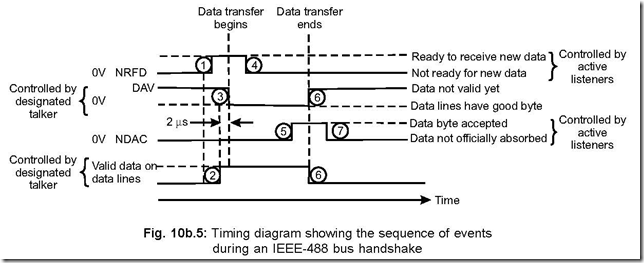
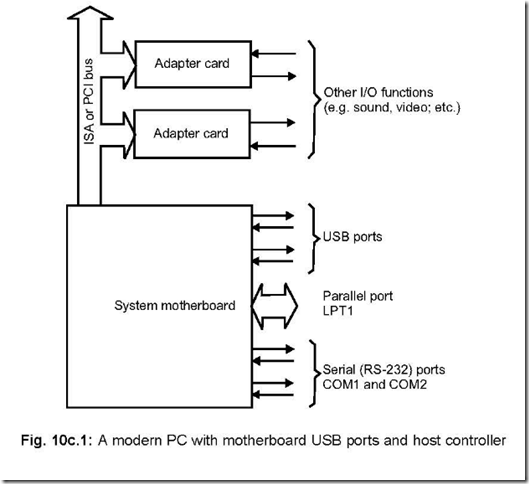
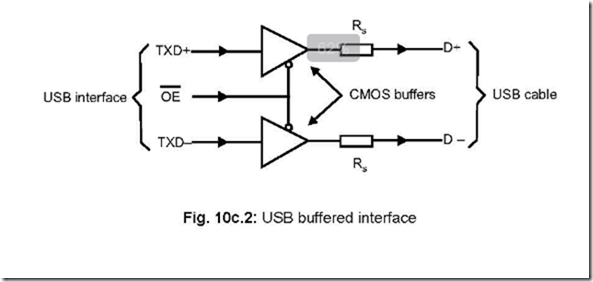
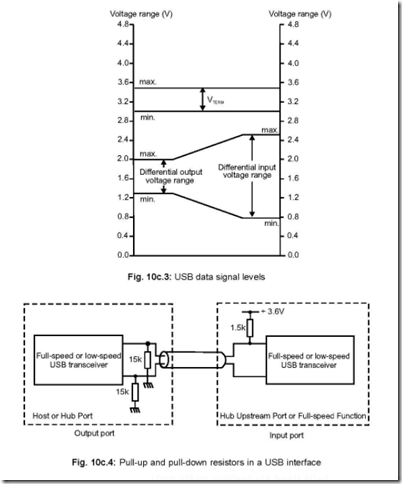
The Instruction Set of 8086
1. How many instructions are there in the instruction set of 8086? Ans. There are 117 basic instructions in the instruction set of 8086.
2. Do 8086 and 8088 have the same instruction set? Ans. Yes, both 8086 and 8088 have the same instruction set.
3. Mention the groups in which the instruction set of 8086 can be categorised. Ans. The instruction set of 8086 can be divided into the following number of groups,
namely:
z Data transfer instructions
z Arithmetic instructions
z Logic instructions
z Shift instructions
z Rotate instructions
z Flag control instructions
z Compare instructions
z Jump instructions
z Subroutines and subroutine handling instructions
z Loop and loop handling instructions
z Strings and string handling instructions.
4. Mention the different types of data transfer instructions. Ans. The different types include:
z Move byte or word instructions (MOV)
z Exchange byte or word instruction (XCHG)
z Translate byte instructions (XLAT)
z Load effective address instruction (LDA)
z Load data segment instruction (LDS)
z Load extra segment instruction (LES)
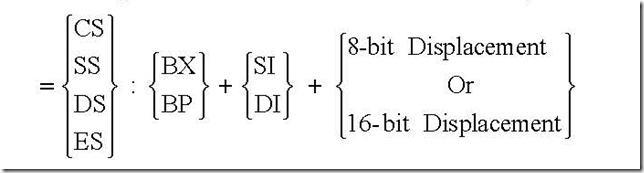
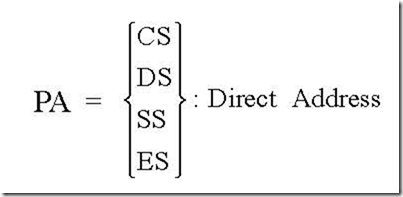
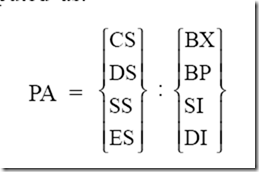
5. Can the MOV instruction transfer data directly between a source and destination that both reside in external memory?
Ans. No, it cannot. With the first MOV instruction, data from the source memory is to be moved into an internal register-normally accumulator. The second MOV instruction places the accumulator content into the destination memory.
6. Explain the following two examples:
(a) MOV CX, CS
(b) MOV AX, [ALPHA]
Ans. (a) MOV CX, CS: It stands for, “move the contents of CS into CX”. If CS contains 1234 H, then on execution of this instruction, content of CX would become 1234 H i.e., content of CH = 12 H and Content CL = 34 H.
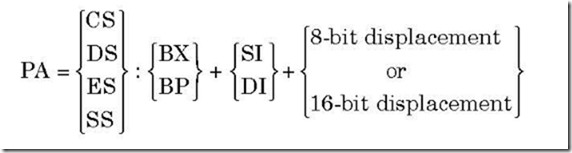
(b) MOV AX, [ALPHA]: Let, data segment register DS contains 0300 H and ALPHA
corresponds to a displacement of 1234 H. Then the instruction stands for, “move the content of the memory location offset by 1234 H from the starting location 0300 H of the current data segment into accumulator AX”. The physical address is
PA = 03000 H + 1234 H = 04234 H
Thus execution of the instruction results in content of memory location 04234 H is moved to AL and content of memory location 04235 H is moved to AH.
7. Show the forms of XCHG instruction and its allowed operands. Ans. These are shown below in Fig. 14.1
|
Mnemonic |
Meaning |
Format |
Operation |
Flags affected |
|
XCHG |
Exchange |
XCHG D,S |
(D)↔(S) |
None |
(a)
|
Destination |
Source |
|
Accumulator Memory Register |
Reg16 Register Register |
(b)
Fig.14.1: (a) Exchange data transfer instruction (b) Allowed operands
8. Explain the instruction XCHG BX, CX.
Ans. The execution of this instruction interchanges the contents of BX and CX, i.e., original content of CX moves over to BX and original content of BX moves over to CX.
9. Explain XLAT instruction.
Ans. The translate (XLAT) data transfer instruction is shown in Fig.14.2. It can be used for say an ASCII to EBCDIC code conversion.
|
Mnemonic |
Meaning |
Format |
Operation |
Flags affected |
|
XLAT |
Translate |
XLAT |
((AL)+(BX)+(DS)O)→(AL) |
None |
Fig.14.2: Translate data transfer instruction
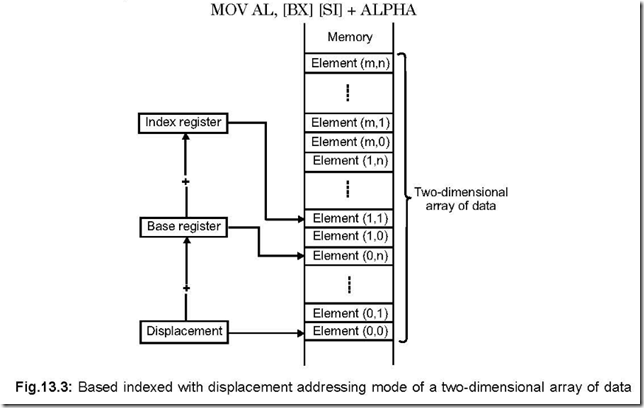
The content of BX represents the offset of the starting address of the look up table from the beginning of the current data segment while the content of AL represents the offset of the element which is to be accessed from the beginning of the look up table.
As an example, let DS = 0300 H, BX = 1234 H and AL = 05 H. Hence, PA = 03000 H + 1234 H + 05 H = 04239 H
Thus, execution of XLAT would put the content of 04239 H into AL register.
Conceptually, the content of 04239 H in EBCDIC should be the same as the ASCII
character equivalent of 05 H.
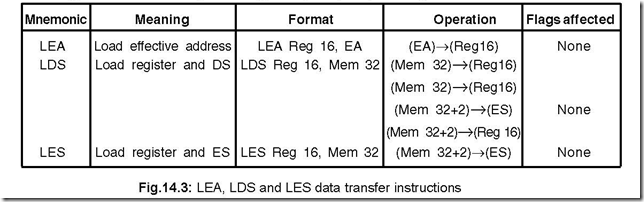
10. Explain the instruction LEA, LDS and LES.
Ans. These three instructions are explained in Fig.14.3. These instructions stand for load register with effective address (LEA), load register and data segment register (LDS) and load register and extra segment register (LES) respectively..
LEA instruction loads a specified register with a 16-bit offset value. LDS and LES instructions load the specified register as well as DS or ES segment register respectively. Thus a new data segment will be activated by a single execution.
11. Indicate the different types of arithmetic instructions possible with 8086.
Ans. The different arithmetic instructions are addition, subtraction, multiplication and division and are shown in Fig.14.4.
|
Addition |
|
|
ADD |
Add byte or word |
|
ADC |
Add byte or word with carry |
|
INC |
Increment byte or word by 1 |
|
AAA |
ASCII adjust for addition |
|
DAA |
Decimal adjust for addition |
|
Subtraction |
|
|
SUB |
Subtract byte or word |
|
SBB |
Subtract byte or word with borrow |
|
DEC |
Decrement byte or word by 1 |
|
NEG |
Negate byte or word |
|
AAS |
ASCII adjust for subtraction |
|
DAS |
Decimal adjust for subtraction |
|
Multiplication |
|
|
DIV |
Divide byte or word unsigned |
|
IDIV |
Integer divide byte or word |
|
AAD |
ASCII adjust for division |
|
CBW |
Convert byte to word |
|
CWD |
Convert word to double word |
Fig.14.4: Arithmetic instructions
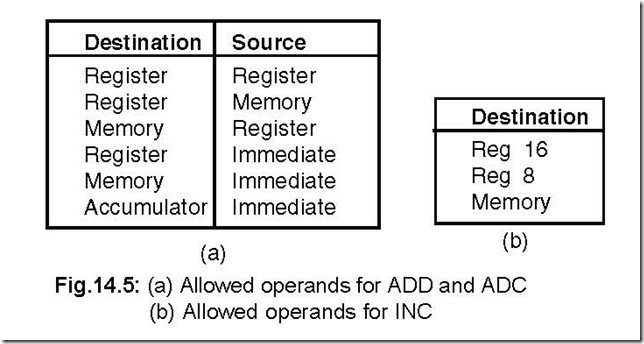
12. Show the allowed operands for the instruction ADD, ADC and INC.
Ans. The allowed operands for ADD and ADC are shown in Fig.14.5 (a) and for INC it is shown in Fig.14.5 (b).
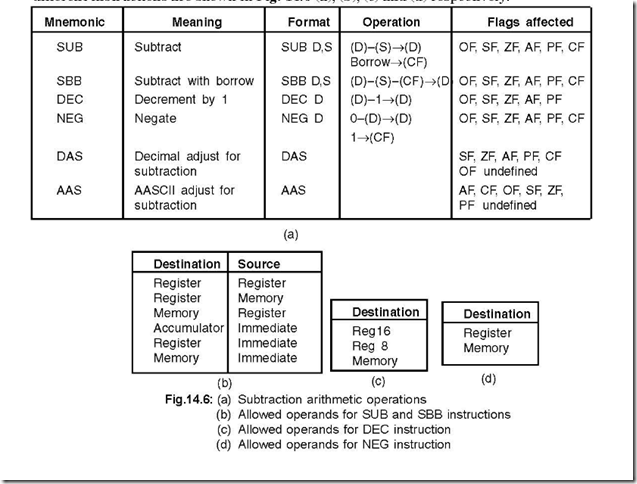
13. Show the different subtraction arithmetic instructions. Also show the allowed operands for (a) SUB and SBB (b) DEC and (c) NEG instructions.
Ans. The different subtraction arithmetic instructions and the allowed operands, for the different instructions are shown in Fig. 14.6 (a), (b), (c) and (d) respectively.
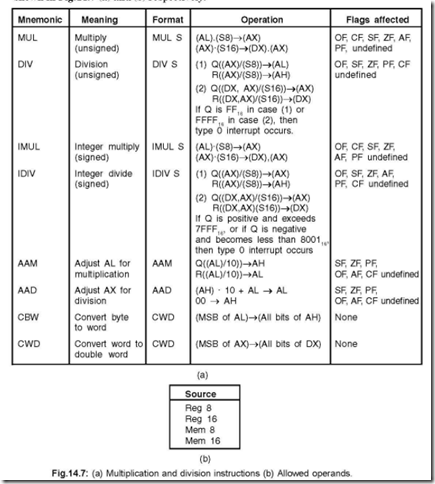
14. Show the different multiplication and division instructions and also the allowed operands.
Ans. The different multiplication and division instructions and also the allowed operands are shown in Fig.14.7 (a) and (b) respectively.
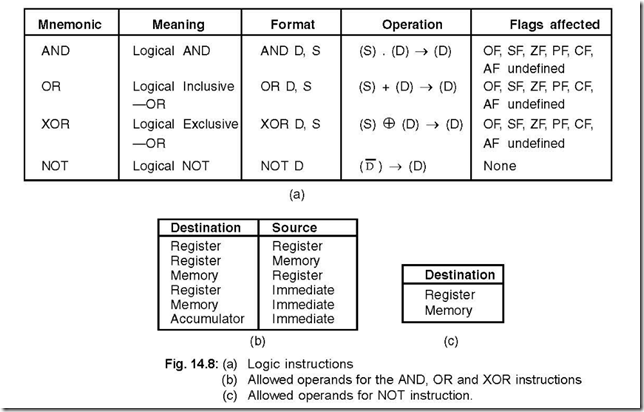
15. Show the different logic instructions and also the allowed operands for
(a) AND, OR and XOR (b) NOT instructions.
Ans. The different logic instructions as also the allowed operands for different instructions are shown in Fig.14.8 (a), (b) and (c) respectively.
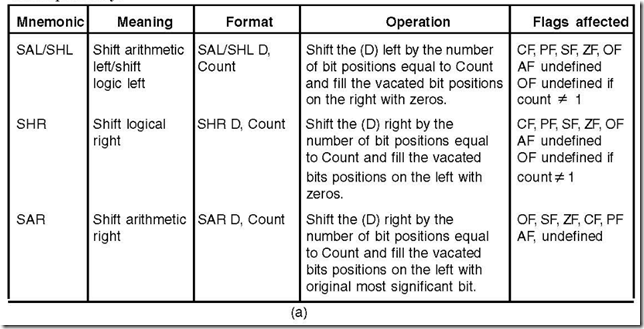
16. What are the two basic shift operations?
Ans. The two basic shift operations are logical shift and arithmetic shift.
The two logical shifts are shift logical left (SHL) and shift logical right (SHR), while
the two arithmetic shifts are shift arithmetic left (SAL) and shift arithmetic right (SAR).
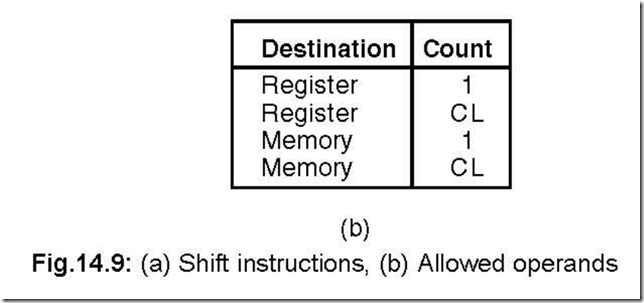
17. Show the different shift instructions and the allowed operands.
Ans. The various shift instructions and the allowed operands are shown in Fig. 14.9 (a) and
(b) respectively.
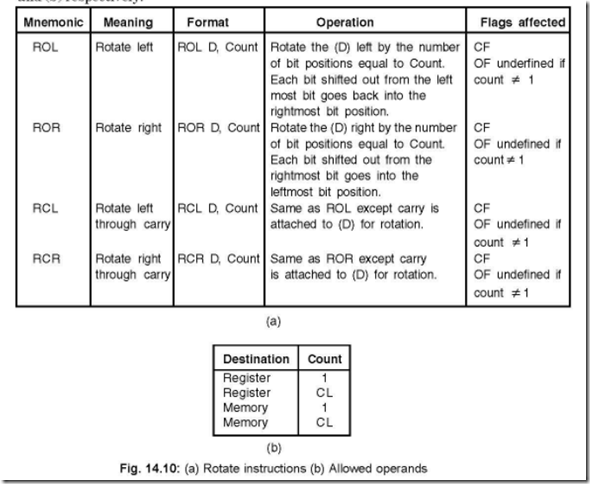
18. Show the different Rotate instructions and the allowed operands.
Ans. The different Rotate instructions and the allowed operands are shown in Fig. 14.10 (a) and (b) respectively.
19. Name the different flags control instructions, the operations performed by them and also the flags affected.
Ans. Fig. 14.11 shows the different flags control instructions, their meaning and the flags affected by respective instructions.
|
Mnemonic |
Meaning |
Operation |
Flags affected |
|
LAHF |
Load AH from flags |
(AH) ← (Flags) |
None |
|
SAHF |
Store AH into flags |
(Flags) ← (AH) |
SF, ZF, AF, PF, CF |
|
CLC |
Clear 0carry flag |
(CF) ← |
CF |
|
STC |
Set ca1rry flag |
(CF) ← |
CF |
|
CMC |
Complement carry flag |
(CF) ← (CF) |
CF |
|
CLI |
Cle0ar interrupt flag |
(IF) ← |
IF |
|
STI |
Se1t interrupt flag |
(IF) ← |
IF |
![]() Fig. 14.11: Flag control instructions
Fig. 14.11: Flag control instructions
20. Which register plays an important part in flag control instructions?
Ans. It is the accumulator register AH which plays an important part in flag control instructions.
For instance, if the present values in the flags are to be saved in some memory location then they are first to be loaded in the AH register and transfered to memory location, say M1, i.e.,
LAHF → Load AH from flags
MOV M1, AH → Move contents of AH into memory location M1.
As a second example, if the content of memory location, Say M2, is to be placed into flags, then
MOV AH, M2 → Move contents of memory location M2 into AH register.
SAHF → Store AH into flags.
21. List the characteristics of CMP instructions.
Ans. The following are the characteristics of CMP instruction:
z Can compare two 8-bit or two 16-bit numbers.
z Operands many reside in memory, a register in the CPU or be a part of an instruction.
z Results of comparison is reflected in the status of the six status flags—CF, AF, OF, PF, SF and ZF.
z CMP is a subtraction method—it uses 2’s complement for this.
z Result of CMP is not saved—but based on CMP result, appropriate flags are either set/reset.
22. Explain CMP instruction.
Ans. The compare instruction, different operand combinations and the flags affected are shown in Fig. 14.12.
|
Mnemonic |
Meaning |
Format |
Operation |
Flags affected |
|
CMP |
Compare |
CMP D, S |
(D) – (S) is used in setting or resetting the flags |
CF, AF, OF, PF, SF, ZF |
(a)
|
Destination |
Source |
|
Register Register Memory Register Memory Accumulator |
Register Memory Register Immediate Immediate Immediate |
(b)
Fig.14.12: (a) Compare instruction (b) Operand combination
23. What are the two basic types of unconditional jumps? Explain.
Ans. The two basic types of unconditional jumps are intrasegment jump and intersegment jump.
The intrasegment jump is a jump for which the addresses must lie within the current
code segment. It is achieved by only modifying the value of IP.
The intersegment jump is a jump from one code segment to another. For this jump
to be effective, both CS and IP values are to be modified.
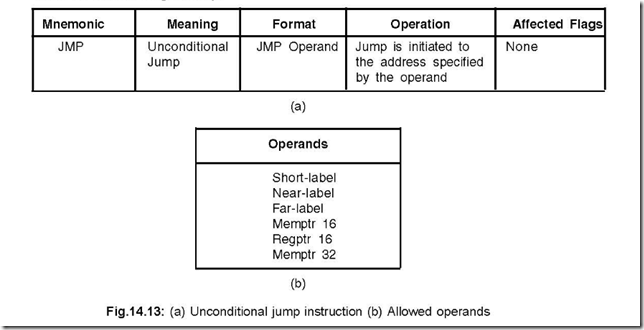
24. Show the unconditional jump instructions and the allowed operands.
Ans. The unconditional jump instruction, along with the allowed operands are shown in Fig.
14.13 (a) and (b) respectively.
Jump instructions carried out with a Short-label, Near-label, Memptr 16 or Regptr 16 type of operands represent intrasegment jumps, while Far-label and Memptr 32 represent intersegment jumps.
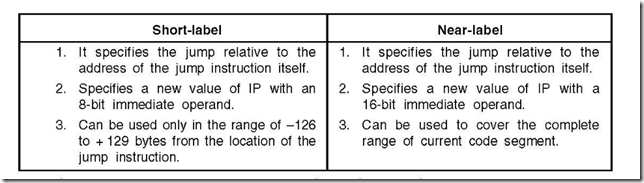
25. Distinguish between Short-label and Near-label jump instructions. Ans. The distinction between the two is shown in a tabular form.
26. Describe the Memptr 16 and Regptr 16 jump instructions.
Ans. Both these types permit a jump to any location (address) in the current code segment.
Again the contents of a memory or register indirectly specifies the address of the jump,
as the case may be.
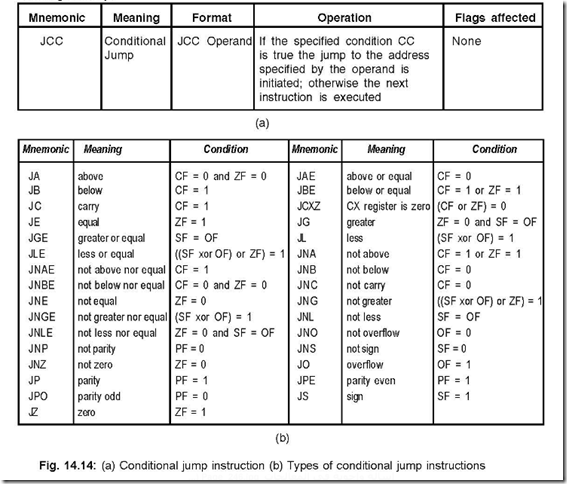
27. Show the conditional jump instruction and their different types.
Ans. The conditional jump instruction and their different types are shown in Fig. 14.14 (a) and
(b) respectively.
28. Show the subroutine CALL instruction and the allowed operands.
Ans. The CALL instruction and the allowed operands are shown in Fig.14.15(a) and
(b) respectively.2929.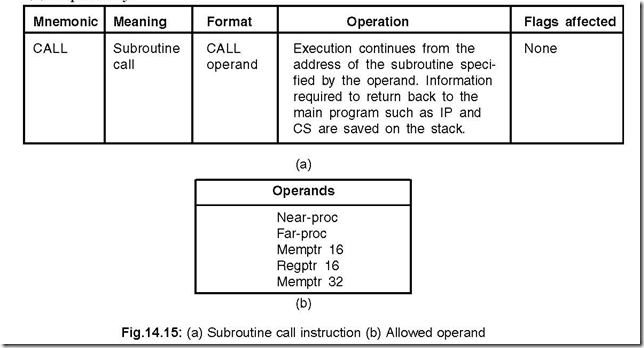
29.What are the two types of CALL instructions? Discuss.
Ans. The two types are: intrasegment CALL and intersegment CALL.
If the operands are Near-proc, Memptr16 and Regptr16, then they specify intrasegment
CALL while Far-proc and Memptr32 represent intersegment CALL.
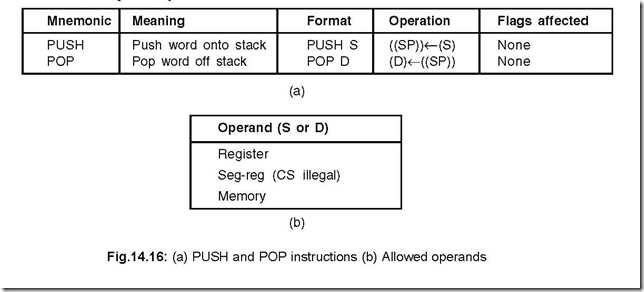
30. Show the PUSH and POP instructions, as also the allowed operands.
Ans. The PUSH and POP instructions, as also the allowed operands are shown in Fig.14.16
(a) and (b) respectively.
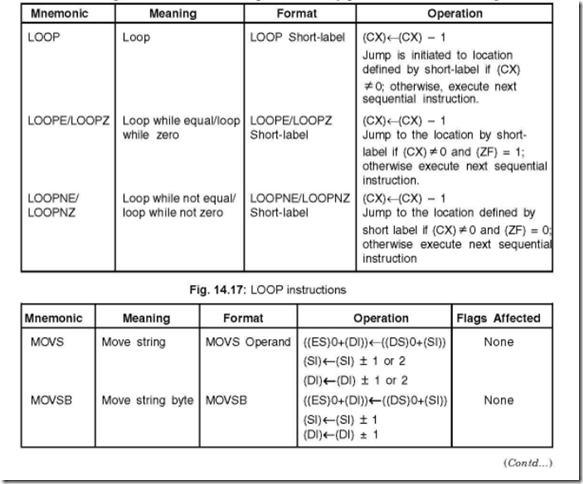
31. How many loop instructions are there and state their use.
Ans. There are in all three loop instructions. They can be used in place of certains conditional jump instructions. These instructions give the programmer a certain amount of flexibility in writing programs in a simpler manner.
32. List the different instructions and also the operations they perform.
Ans. The different loop instructions and the operations they perform are shown in Fig. 14.17.
33. What is meant by a ‘string’ and what are the characteristics of a string instruction?
Ans. A string is a series of data words (or bytes) that reside in successive memory locations.
The characteristics of a string instruction are:
z Can move data from one block of memory locations to another one.
z A string of data elements stored in memory can be scanned for a specific data value.
Successive elements of two strings can be compared to determine whether the two
strings are same/different.
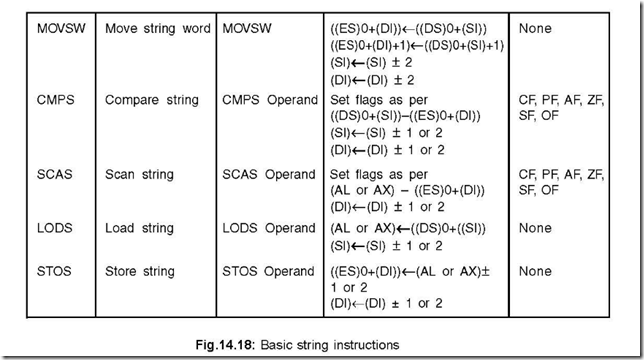
34. List the basic string instructions and the operations they perform.
Ans. The basic string instructions and the operations they perform are shown in Fig. 14.18
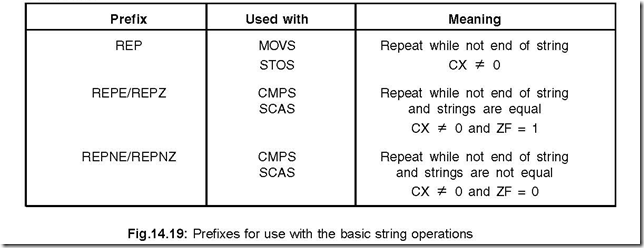
35. What is a ‘REP’ instruction? Discuss.
Ans. ‘REP’ stands for repeat and is used for repeating basic string operations—required for processing arrays of data.
There are a number of repeat instructions available and are used as a prefix in string instructions. The prefixes for use with the basic string instructions are shown in Fig. 14.19.
36. Discuss the instructions for Autoindexing of string instructions.
Ans. When the system executes some string instruction, the addresses residing in DI and SI are incremented/decremented automatically. The content of direction flag (DF) decides the above. Two instructions—CLD (clear DF flag) or STD (Set DF flag) are used for the above and shown in Fig. 14.20.![The Instruction Set of 8086 6-25-36 PM_thumb[1] The Instruction Set of 8086 6-25-36 PM_thumb[1]](http://lh5.ggpht.com/-jvsf59Z6-8U/VEveGw6SfSI/AAAAAAAAqu4/xpk-_hpgLhE/The%252520Instruction%252520Set%252520of%2525208086%2525206-25-36%252520PM_thumb%25255B1%25255D_thumb.png?imgmax=800)
Fig. 14.20: Instructions for autoincrementing and autodecrementing in string instructions
Execution of CLD (this makes DF = 0) permits autoincrement mode while execution of STD (this makes DF = 1) permits autodecrement mode.
SI or DI are autoincremented/autodecremented by one if a byte of data is processed or by two if a word of data is processed.
37. Write down the equivalent string instructions for the following two.
|
Ans. The following two are the equivalent string instructions of the given ones:
(i) STD (ii) CLD
CMP SB MOV SB
38. Where do memory source and destination addresses reside in string instructions?
Ans. The memory source and destination addresses in such cases are register SI in the data segment and DI in the extra segment.
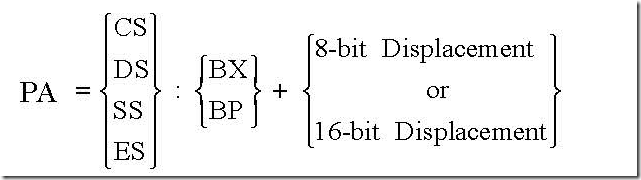
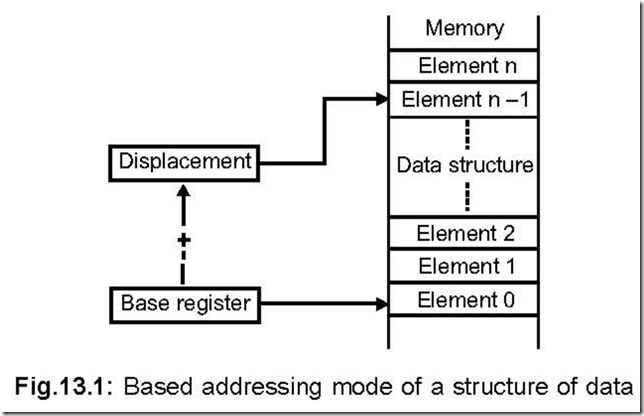
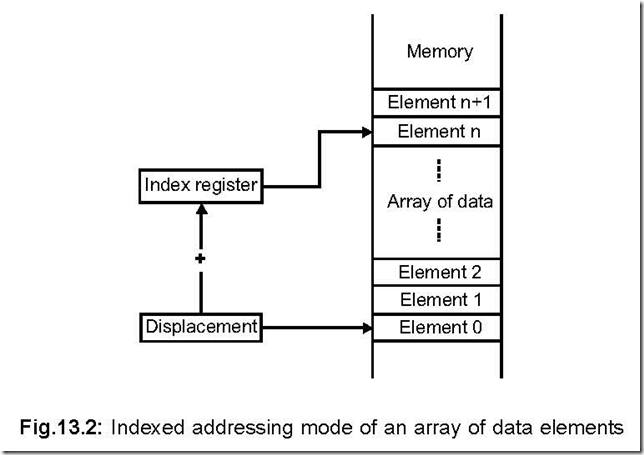
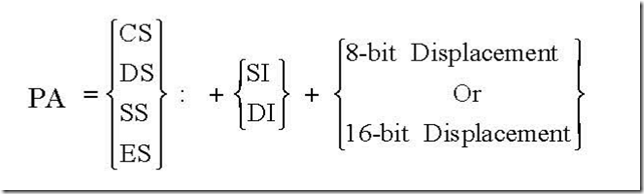
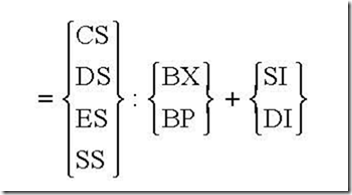

![The 8086 Microprocessor 8-56-12 PM_thumb[1] The 8086 Microprocessor 8-56-12 PM_thumb[1]](http://lh4.ggpht.com/-DXoU3bgyB5A/VEu70HWokhI/AAAAAAAAqhQ/9T0jJW_qdYU/The%2525208086%252520Microprocessor%2525208-56-12%252520PM_thumb%25255B1%25255D_thumb.png?imgmax=800)
![The 8086 Microprocessor 8-57-20 PM_thumb[1] The 8086 Microprocessor 8-57-20 PM_thumb[1]](http://lh5.ggpht.com/-KzuBgLLZeDQ/VEu8AiezLFI/AAAAAAAAqhw/pqEmflfVlqU/The%2525208086%252520Microprocessor%2525208-57-20%252520PM_thumb%25255B1%25255D_thumb.png?imgmax=800)
![The 8086 Microprocessor 9-00-29 PM_thumb[1] The 8086 Microprocessor 9-00-29 PM_thumb[1]](http://lh5.ggpht.com/-WBHRHFs7_5o/VEu821iu0pI/AAAAAAAAqkg/tpJpVDVrDZs/The%2525208086%252520Microprocessor%2525209-00-29%252520PM_thumb%25255B1%25255D_thumb.png?imgmax=800)
![The 8086 Microprocessor 9-01-10 PM_thumb[1] The 8086 Microprocessor 9-01-10 PM_thumb[1]](http://lh5.ggpht.com/-cNZLAk9z6IQ/VEu89jlbt0I/AAAAAAAAqlA/A90xq_Z1WGQ/The%2525208086%252520Microprocessor%2525209-01-10%252520PM_thumb%25255B1%25255D_thumb.png?imgmax=800)