■ SUMMARY
Communication involves the transfer of information between systems. As a rule, data is transferred in bit-serial fashion because the time-of-flight delays dominate the transfer time for high speed networks. However, modulation schemes allow many bits to be encoded in a single sample, such as for a dibit. The choice of modulation scheme impacts the introduction of errors into the transmission of information. Error detection and correction are made possible through redundancy, in which there are more bit patterns possible than the number of valid bit patterns. If the error bit patterns do not have a single closest valid code word, then error detection is possible but error correction is not possible. If every error bit pattern is reachable from only one valid bit pattern, then error correction is also possible.
Local area networks (LANs) manage complexity by using layering that is based on the OSI model. These days, LANs are typically connected to wide area networks (WANs), most notably, the Internet. The Internet is based on the TCP/IP protocol suite. User data is encapsulated at the Application, Transport, Network, and Link layers, and is sent through the Internet and de-encapsulated (de muxed) on the receiving system. As it is passed through the Internet, the data traverses various transmission media, that vary in bandwidth and distance capabilities.
■ FURTHER READING
(Needleman, 1990) and (Schnaidt, 1990) give a thorough treatment of local area networks according to the OSI model, and (Tanenbaum, 1996) is a good reference on network communication in general. (Halsall, 1996) gives a thorough and readable treatment of network media types. (dePrycker, 1993) gives an in-depth account of ATM and its characteristics.
(Tanenbaum, 1999) and (Stallings, 1996) give readable explanations of Ham- ming encoding. (Hamming, 1986) and (Peterson and Weldon, 1972) give more detailed treatments of error-correcting codes.
Halsall, F., Data Communications, Computer Networks, and Open Systems, 4/e, Addison-Wesley, (1996).
Hamming, R. W., Coding and Information Theory, 2/e, Prentice-Hall, (1986). Needleman, R., Understanding Networks, Simon and Schuster, New York,
(1990).
Peterson, W. Wesley and E. J. Weldon, Jr., Error-Correcting Codes, 2/e, The MIT Press, (1972).
de Prycker, Martin, Asynchronous Transfer Mode: Solution for Broadband ISDN, 2/e, Ellis Horwood, (1993).
Schnaidt, P., LAN Tutorial, Miller Freeman Publications, California, (1990). Stallings, W., Computer Organization and Architecture: Designing for Performance,
4/e, Prentice Hall, Upper Saddle River, (1996).
Tanenbaum, A., Computer Networks, 3/e, Prentice Hall, Upper Saddle River, (1996).
Tanenbaum, A., Structured Computer Organization, 4/e, Prentice Hall, Engle- wood Cliffs, (1999).
■ PROBLEMS
9.1 What is the Hamming distance for the ASCII SEC code discussed in Section 9.4.2?
9.2 Construct the SEC code for the ASCII character ‘Q’ using even parity.
9.3 For parts (a) through (d) below, use a SEC code with even parity.
(a) How many check bits should be added to encode a six-bit word?
(b) Construct the SEC code for the six-bit word: 1 0 1 1 0 0. When construct- ing the code, number the bits from right to left starting with 1 as for the method described in Section 9.4.2.
(c) A receiver sees a two-bit SEC encoded word that looks like this: 1 1 1 0 0. What is the initial two-bit pattern?
d) The 12-bit word: 1 0 1 1 1 0 0 1 1 0 0 1 complete with an SEC code (even parity) is received. What 12-bit word was actually sent?
9.4 How many check bits are needed for a SEC code for an initial word size of 1024?
9.5 Construct a checksum word for EBCDIC characters ‘V’ through ‘Z’ using
vertical redundancy checking with even parity. DO NOT use longitudinal redundancy checking.
9.6 Compare the number of bits used for parity in the SEC code with the simple parity VRC code, for 1024 eight-bit characters:
(a) Compute the number of check bits generated using SEC only (horizon- tally).
(b) Compute the number of checksum bits using VRC only.
9.7 The SEC code discussed in Section 9.4.2 can be turned into a double error detecting/SEC (DED/SEC) code by adding one more bit that creates even parity over the SEC code (which includes the parity bit being added.) Explain how double error detection works while also maintaining single error correction with this approach.
9.8 Compute the CRC for a message to be transmitted M(x) = 101100110 and a generator polynomial G(x) = x3 + x2 + 1.
9.9 What is the longest burst error that CRC-32 is sure to catch?
9.10 To which IPv4 class does address 165.230.140.67 belong?
9.11 How many networks (not hosts) can the IPv4 class A, B, and C addresses support? That is, how many distinct class A, B, and C network addresses can there be? Do not consider reserved addresses.
9.12 Network media always carry data in bit-serial fashion, and virtually never in parallel. That is not to say that data could not be carried over a network in byte-parallel or word-parallel fashion; there simply is no advantage to doing it this way. To see why this is the case, calculate the time required to transmit a 32-bit word between two computers over a 32-foot network. The network speed is 1 Gbps per channel. The time-of-flight delay imposed by the distance is 1 ns per foot. Calculate the time to transmit the 32-bit word using a single channel (bit-serial fashion) and using 32 channels (word-parallel fashion).
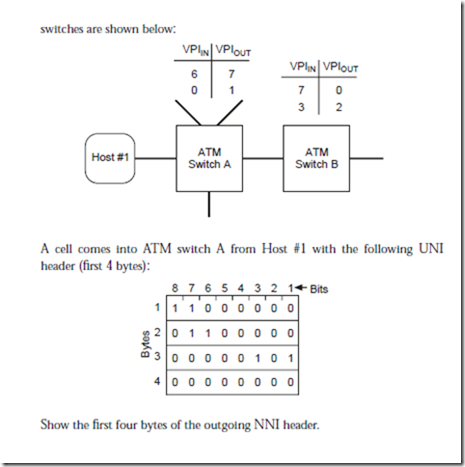
9.13 An ATM network has two switches A and B that switch on the virtual path identifier only. The network topology and the routing tables for the