WIRELESS NETWORKS
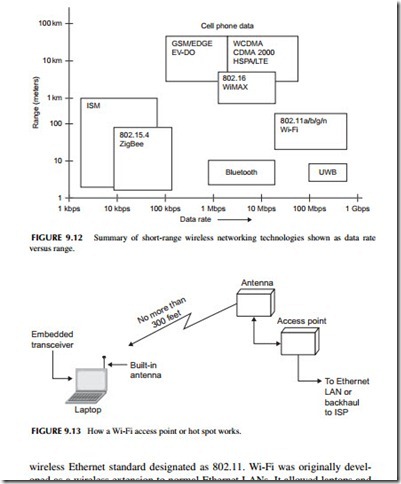
Wireless networks are usually LANs or PANs, but may also be MANs. Most wireless networks are short-range wireless connections that bring greater mobility as well as freedom from interconnecting cables to networking. Figure 9.12 shows a graph designating the various types of wireless networking schemes in use today. In this graph, each networking technology is defined in terms of its data rate as well as its range. In this section, we take a look at all of these technologies, most of which you have heard of or already use on a regular basis.
Wi-Fi
The most widely used wireless networking technology is referred to by its trade name Wi-Fi, meaning wireless fidelity. This the name given to the IEEE’s
wireless Ethernet standard designated as 802.11. Wi-Fi was originally developed as a wireless extension to normal Ethernet LANs. It allowed laptops and personal computers and even cell phones to connect to a company or organizational LAN wirelessly instead of the normal CAT5 connection. This not only simplified and in many case eliminated new wiring but also gave employees greater freedom and mobility, particularly since most employees use laptop computers rather than fixed PCs.
Figure 9.13 shows how Wi-Fi works. Each PC, laptop, or cell phone has a built-in data transceiver and antenna that communicate with a wireless access point (AP). This wireless access point is a transceiver that connects directly to an Ethernet switch, which, in turn, connects to the LAN wiring and its server. Access points are placed at strategic locations within buildings to allow as many people as possible to connect wirelessly.
There are also public access points known as hot spots. These are present in coffee shops, airports, hotels, and in many other locations, allowing anyone with a laptop or cell phone to connect. These hot spots talk back to a central point by a backhaul method, such as a T1 telephone line or microwave relay link that connects to an Internet service provider that, in turn, is connected to the Internet.
The 802.11 standard exists in several basic forms. The most popular version of this standard is 802.11b. It operates in the 2.4- to 2.483-GHz unlicensed band. It uses the direct sequence spread spectrum (DSSS) and is capable of data rates up to 11 Mbps in a range of up to 100 meters. This frequency band is divided into 11 channels, each 22 MHz wide. The computer and access point decide on which channel to use to minimize interference with other transmissions. If you are close enough to the access point, you can actually get the 11-Mbps data rate, but if you are not, the system automatically ratchets down to 5.5, 2, or even 1 bps depending on the range, interference, and noise or other environmental conditions.
Another popular version of the standard is 802.11g. It is a faster version of Wi-Fi that also operates in the 2.4-GHz band. It can achieve data rates as high as 54 Mbps up to 100 meters. It uses OFDM with 52 subcarriers. The most recent standard is 802.11n, which uses OFDM and MIMO to achieve even higher data rates up to approximately 600 Mbps. Another less popular version is 802.11a, which uses the 5-GHz unlicensed band. It too uses OFDM and can achieve data rates to 54 Mbps. The IEEE is also currently working on an advanced wireless standard that should ultimately be able to achieve a 1-Gbps data rate in the near future.
Wi-Fi is also built into most of the new smartphones. While a smartphone has data capability because of its 3G digital technology, Wi-Fi gives it one more way to access the Internet and email.
Wi-Fi is also the most popular home networking technology. With no wires to install, it is easy to set up and use with a broadband DSL connection or cable TV access.
Bluetooth
Bluetooth was developed as a personal area network (PAN) for connecting computers, cell phones, and other devices up to a range of about 30 feet. It is a low-speed data transmission method. Bluetooth operates in the same 2.4- to 2.483-GHz unlicensed spectrum as Wi-Fi. It uses a technique known as frequency hopping spread spectrum (FHSS), where the data is divided into chunks and transmitted via a carrier that hops from one random frequency to another. Data is transmitted at a 1-Mbps rate using FSK. An enhanced data rate (EDR) version of Bluetooth is also available to transmit at higher speeds up to 3 Mbps. Even newer versions can give data rates as high as 24 Mbps and even higher rates are possible in future versions of the standard. The standard is managed by the Bluetooth Special Interest Group (SIG).
One of the basic features of Bluetooth is that it is capable of forming small networks called piconets. It does this by linking two Bluetooth devices together. One serves as a master controller and it can connect to seven other Bluetooth slave devices. Once the PAN has been set up, the various connected devices can exchange information with one another through the master.
By far the most common application for Bluetooth is cordless headsets for cell phones. But you will also encounter it in some wireless connections between laptops and cell phones. It is also used in some computer peripheral devices such as PC-to-printer connections.
ZigBee
ZigBee is another short-range PAN network technology with the IEEE desig- nation 802.15.4. It uses low power, so the range is typically 100 meters or less, basically depending on the antennas and the physical environment where it is used. ZigBee also operates in that unlicensed spectrum from 2.4 to 2.483 GHz.
The IEEE 802.15.4 standard defines the basic radio technology. It uses direct-frequency spread spectrum (DSSS) and a version of QPSK that gives a data rate of 250 Kbps. The frequency spectrum is divided into 16 1-MHz channels.
The basic function for ZigBee is monitoring and control. Monitoring refers to telemetry that allows sensors to collect information, which is then transmit- ted by radio to some central collection point. It also allows for remote control of the devices such as lights, motors, and other items. The ZigBee Alliance, the organization that promotes and enhances this wireless technology, has developed a series of applications for industrial monitoring and control, home monitoring and control, energy monitoring (automatic meter reading) and con- trol, and several others.
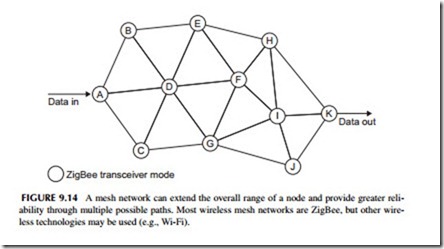
A major feature of the ZigBee technology is its ability to perform mesh net- works. While a typical ZigBee radio node may only have a range of 30 meters or less, the range can be extended by simply transmitting data from one node to another in a mesh network that may cover hundreds of meters, or in some cases even miles. A mesh is shown in Figure 9.14. Each circuit is a ZigBee transceiver node and each line is a wireless path. Mesh networks have many different paths for data and, therefore, are extremely reliable. If one path is blocked or disabled, data can usually find its way to the desired destination by way of another path. For example, in Figure 9.14, a direct path may be from A-D-F-I-K, but if the D-to-F link is blocked or the I node is disabled, the mesh would automatically reroute the data through another path such as A-D-G-J-K.
A forthcoming application of the 802.15.4 standard is the replacement of the current infrared (IR) TV remote controls. An RF version called RF4CE is gradually expected to replace IR remotes in all consumer electronic equipment providing longer range and no line of sight limitations. Two-way communications are expected to be implemented.
Ultra Wideband
Ultra wideband (UWB) technology is a very broadband, high-speed PAN designed for transmitting audio, video, and high-speed data. It uses OFDM in the frequency spectrum from 3.1 GHz to roughly 5 GHz. Higher frequencies up to 10.6 GHz are available but not widely used. Ultra wideband has a maximum data rate of 480 Mbps, but the actual rate depends on the range between nodes.
WiMAX
WiMAX is actually a wireless MAN. It was initially designed to offer a wire- less alternative to Internet connections to homes, usually by way of cable TV systems or DSL lines of a telephone company. WiMAX is also standardized by the IEEE as 802.16. It comes in two variations, fixed and mobile. The fixed version is used for Internet connectivity in a fixed mode where the nodes in a star-like network are essentially in one position. WiMAX services are now available through an organization such as Clearwire in the United States with base stations with a range of several miles. Laptop computers containing WiMAX transceivers can connect to the network. Data rates will vary depend- ing on the service offered by the company but can be from 1 Mbps to 10Mbps or more. The technology uses OFDM with modulation schemes including BPSK, QPSK, 16-QAM, and 64-QAM. MIMO may or may not be used.
A mobile version of WiMAX is also available. It is designed for connec- tivity where laptops and other mobile devices can connect to access points or base stations even while in motion.
Most WiMAX activity takes place in the United States in the 2.5-GHz frequency range and the 3.5-GHz range in Europe, Canada, and Asia. It is expected that WiMAX will be used in the new 700-MHz band for high-speed Internet access.
Radio Frequency Identification and Near-Field Communications
Radio frequency identification (RFID) is a very short-range technology that is intended to substitute for standard bar codes. Practically everything has a printed bar code on it today so that with optical scanners the device can be rec- ognized by a particular part number or other information that identifies it. The bar code readers are normally attached to a computer and, in turn, a network.
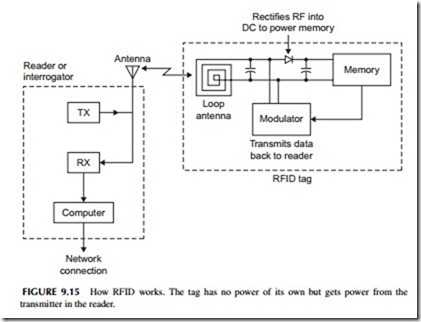
RFID devices are small thin plastic tags containing a radio chip that can be read by a wireless reader. The RFID chip contains an EEPROM memory in which is stored the device’s unique identification number and other related information. A key characteristic of the RFID tag is that it contains no power source such as a battery. Yet it is designed to transmit its digital code to some external reading device whenever it is interrogated. Figure 9.15 shows how it works.
The interrogation takes place when an external reader made up of a trans- mitter (TX) sends a radio frequency (RF) signal to the nearby tag. The radio frequency energy received by the tag’s antenna is then rectified and filtered into a DC voltage that is used to power up the memory and the modulator circuit that sends data back to the reader. The reader also contains a receiver (RX) that picks up the small signal from the tag and sends it on to a computer where identification takes place.
RFID tags are generally used for what is known as asset tracking. RFID tags are attached to any relatively expensive item whose position is to be monitored, tracked, or otherwise controlled. It is good for keeping track of capital equipment, baggage, manufacturing tools, and other items. It is also used for personnel security on badges that employees wear and is good for animal tracking. One of the most widely used applications is automatic toll collection on highways.
RFID tags come in a variety of sizes, shapes, and technologies. Some of the older tags work at a frequency of 125 kHz or 13.56 MHz. The newer tags work at UHF frequencies in the 902- to 928-MHz range. All of these tags are passive devices with no power other than that received from the reader. Some longer-range RFID tags with small batteries have also been developed.
The unique code stored in the EEPROM is stored during the tag’s manu- facture. It is then clocked out at a relatively slow rate of speed around 70 kbps. The serial binary data is used in a form of amplitude modulation called back- scatter modulation that produces minor variations in the reader’s signal that can be converted back into a binary code.
Another similar RFID-like technology is known as near-field communications (NFC). It has an even shorter range of only about 1 foot. It operates on 13.56 MHz. It is mainly designed to be used in credit cards and in cell phones to produce automatic transactions such as credit card purchases or payment for transportation (e.g., train, subway, bus) or access to some facility.