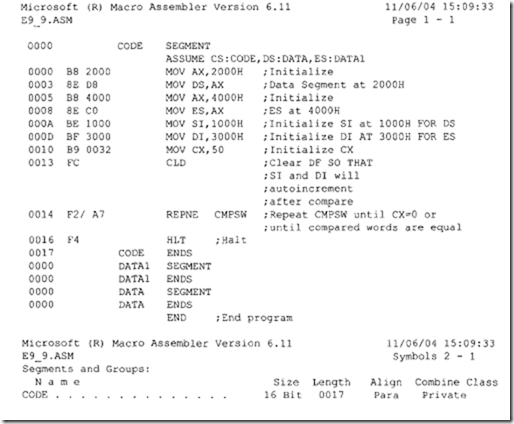
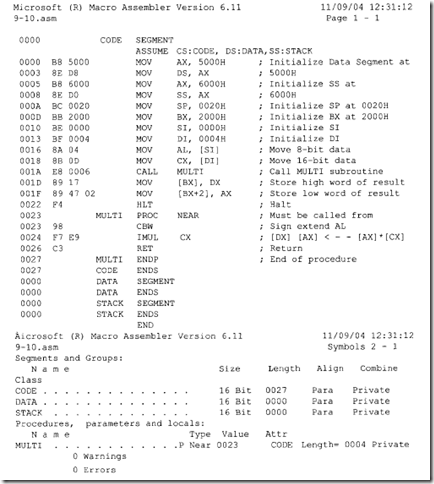
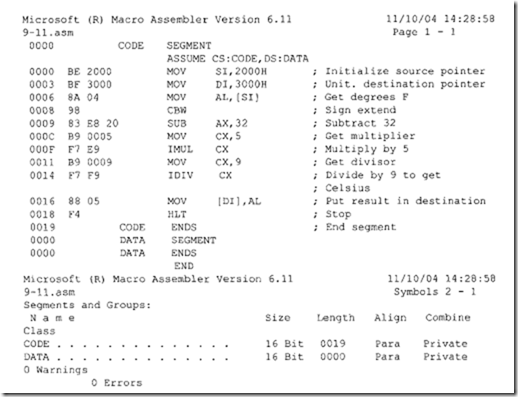
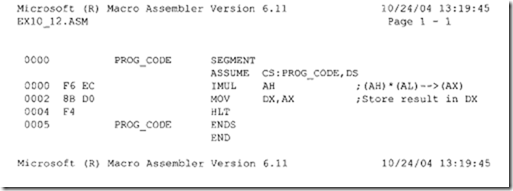
9.9 System Desi :n Usin : the 8086
This section covers the basic concepts associated with interfacing the 8086 with its support chips such as memory and I/O . Topics such as timing diagrams and 8086 pins and signals will also be included. Appendix E provides data sheets for Intel 8086 and support chips.
9.9.1 8086 Pins and Signals
The 8086 pins and signals are shown in Figure 9.8. As mentioned before, the 8086 can operate in two modes. These are the minimum (uniprocessor systems with a single 8086) and maximum mode (multiprocessor system with more than one 8086). MN/MX is an input pin used to select one of these modes.
When MN/MX is HIGH, the 8086 operates in the minimum mode. In this mode, the 8086
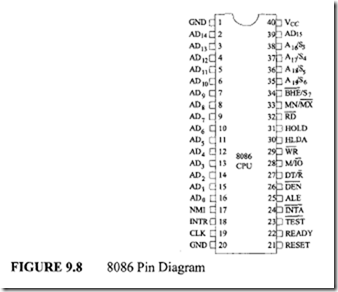
is configured (that is, pins are defined) to support small single-processor systems using a few devices that use the system bus. When MN/MX is low, the 8086 is configured (that is, some of the pins are redefined in maximum mode) to support multiprocessor systems. In this case, the Intel 8288 bus controller is added to the 8086 to provide bus control and compatibility with the multibus architecture. Note that, in a particular application, MN/ MX must be tied to either HIGH or LOW.
The AD0-AD15 lines are a 16-bit multiplexed address/data bus. During the first clock cycle, AD0-AD15 are the low-order 16-bit address. The 8086 has a total of20 address lines. The upper four lines, A 16/S3, A 17/S4, A 18/S5, and A 1c/S6, are multiplexed with the status signals for the 8086. During the first clock period of a bus cycle (read or write
cycle), the entire 20-bit address is available on these lines. During all other cycles for memory and I/O , AD0-AD15 lines contain the 16-bit data, and the multiplexed address I status lines become S3, S4 , S5, and S6• S3 and S4 are decoded as follows:
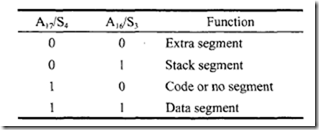
Therefore, after the first clock cycle of an instruction execution, the A 17/S4 and A 16/S3 pins specify which segment register generates the segment portion of the 8086 address. Thus, by decoding these pins and then using the decoder outputs as chip selects for memory chips, up to four megabytes (one megabyte per segment) can be included. This provides a degree of protection by preventing erroneous write operations to one segment
from overlapping onto another segment and destroying the information in that segment. A 18/S5 and A 19/S6 are used as A 18 and A 19, respectively, during the first clock cycle of an instruction execution. If an I/O instruction is executed, they stay LOW for the first clock
period. During all other cycles, A 18/S5 indicates the status of the 8086 interrupt enable flag
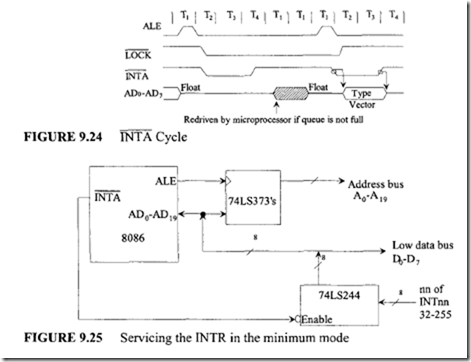
and A19/S6 becomes S6; a LOW S6 pin indicates that the 8086 is on the bus. During a hold acknowledge clock period, the 8086 tristates the A 19/S6 pin and this allows another bus master to take control of the system bus. The 8086 tristates AD0-AD15 during interrupt acknowledge or hold acknowledge cycles.
 BHE/S 7 is used as BHE (bus high enable) during the first clock cycle of an instruction execution. The 8086 outputs a LOW on this pin during the read, write, and interrupt acknowledge cycles in which data are to be transferred in a high-order byte (AD15-AD8) of the data bus. BHE can be used in conjunction with AD0 to select memory banks. A thorough discussion is provided later. During all other cycles, BHE/S 7 is used as S7 and the 8086 maintains the output level (BHE) of the first clock cycle on this pin. S7 is the same as BHE and does not have any special meaning.
BHE/S 7 is used as BHE (bus high enable) during the first clock cycle of an instruction execution. The 8086 outputs a LOW on this pin during the read, write, and interrupt acknowledge cycles in which data are to be transferred in a high-order byte (AD15-AD8) of the data bus. BHE can be used in conjunction with AD0 to select memory banks. A thorough discussion is provided later. During all other cycles, BHE/S 7 is used as S7 and the 8086 maintains the output level (BHE) of the first clock cycle on this pin. S7 is the same as BHE and does not have any special meaning.
TEST is an input pin and is only used by the WAIT instruction. The 8086 enters a wait state after execution of theW AIT instruction until a low is seen on the TEST pin. This input is synchronized internally during each clock cycle on the leading edge of the clock.
INTR is the maskable interrupt input. This line is not latched, so INTR must be held at a HIGH level until it is recognized to generate an interrupt.
NMI is the nonmaskable interrupt pin input activated by a positive edge.
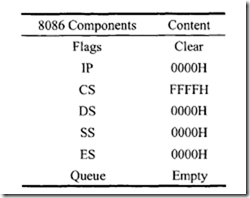
RESET is the system reset input signal. This signal must be HIGH for at least four clock cycles to be recognized, except on power-on, which requires a 50-f.!sec reset pulse. It causes the 8086 to initialize registers DS, ES, SS, IP, and flags to zeros. It also initializes CS to FFFFH. Upon removal of the RESET signal from the RESET pin, the 8086 will fetch its next instruction from a 20-bit physical address FFFF0H (CS = FFFFH, IP = 0000H). When the 8086 detects a positive edge of a pulse on RESET, it stops all activities until the signal goes LOW. Upon hardware reset, the 8086 initializes the system as follows:
As mentioned before, the 8086 can be configured in either minimum or maximum mode using the MN/MX input pin. In minimum mode, the 8086 itself generates all bus control signals. These signals are as follows:
-
DTIR (data transmit/receive) is an output signal required in a minimum system that uses an 8286/8287 data bus transceiver. It is used to control direction of data flow through the transceiver.
-
DEN (data enable) is provided as an output enable for the 8286/8287 in a minimum system that uses the transceiver. DEN is active LOW during each memory and 1/0 access and for INTA cycles.
-
ALE (address latch enable) is an 8086 output signal that can be used to demultiplex the multiplexed 8086 pins including AD0-AD15 into A0-A15 and D0-D15 at the falling edge of ALE.
-
M/IO is an 8086 output signal. It is used to distinguish a memory access (M/IO = HIGH) from an 110 access (M/lO= LOW). When the 8086 executes an 1/0 instruction such as IN or OUT, it outputs a LOW on this pin. On the other hand, the 8086 outputs HIGH on this pin when it executes a memory reference instruction such as MOV AX, [SI].
-
WR is used by the 8086 for a write operation. The 8086 outputs a low on this pin to indicate that the processor is performing a write memory or write I/O operation, depending on the M/IO signal. Similarly, RD is low whenever the 8086 is reading data from memory or an I/O location.
-
For interrupt acknowledge cycles (for the INTR pin), the 8086 outputs LOW on the INTApin.
-
HOLD (input) and HLDA (output) pins are used for DMA. A HIGH on the HOLD pin indicates that another master is requesting to take over the system bus. The processor receiving the HOLD request will output a HIGH on the HLDA as an acknowledgment. At the same time, the processor tristates the system bus. Upon receipt of LOW on the HOLD pin, the processor places LOW on the HLDA pin and takes over the system bus.
-
CLK (input) provides the basic timing for the 8086 and bus controller.
-
READY (input) pin is used for slow peripheral devices.
There are four versions of the 8086. They are 8086, 8086-1, 8086-2, and 8086-4. There is no difference between the four versions other than the maximum allowed clock speeds. The 8086 can be operated from a maximum clock frequency of 5 MHz. The maximum clock frequencies of the 8086-1, 8086-2 and 8086-4 are 10 MHz, 8 MHz and 4 MHz, respectively. Because the design of these processors incorporates dynamic cells, a minimum frequency of2 MHz is required to retain the state of the machine. The 8086-4, 8086, and 8086-2 will be referred to as 8086 in the following discussion.
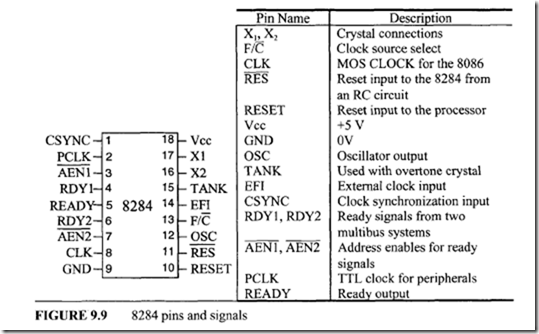
The reset, clock, and the ready signals of the 8086 can be generated by the Intel 8284. Figure 9.9 shows the pins and signals of the 8284.
The 8284 is an 18-pin chip designed for providing three input signals for the 8086:
1. 8086 CLK input
2. 8086 Reset input
3. 8086 Ready input
The 8284 pins and signals are described in the following.
Clock Generation Signals
Because the 8086 has no on-chip clock generator circuitry, the 8284 chip is required to provide the 8086 clock input. The 8284 F/C input pin is provided for clock source selection. When the F/C pin is connected to LOW, a crystal connected between 8284’s X 1 and X2 pins is used. On the other hand, when F/C is connected to HIGH, an external clock source is used; the external clock source is connected to the 8284 EFI (external frequency input) pin. The 8284 divides the clock inputs at the X 1X2 pins or the EFI pin by 3. This means that if a 15-MHz crystal is connected at the X 1X2 or EFI pins, the 8284 CLK output pin will be 5 MHz. The 8284 CLK pin will be connected to the 8086 CLK pin. This provides the clock input for the 8086. When selecting a crystal for use with the 8284, the crystal series resistance should be as low as possible. The oscillator delays in the 8284 appear as inductive elements to the crystal and cause the 8284 to run at a frequency below that of the pure series resonance: a capacitor CL should be placed in series with the crystal and the 8284 X2 pin. The capacitor cancels the inductive element. The impedance of the capacitor Xc = 11(2rcfCJ wherefis the crystal frequency. Intel recommends that the crystal series resistance plus Xc should be kept less than 1 KQ.
As the crystal frequency increases, CL should be decreased. For example, a 12- MHz crystal may require CL = 24 pf whereas a 22-MHz crystal may require CL = 8pf. CL values of 12 to 15 pf may be used with a 15-MHz crystal. Two crystal manufacturers recommended by Intel are Crystle Corp., Model CY 15A (15 MHz), and CTS Knight, Inc., Model CY 24A (24 MHz). Note that the 8284 CLK output pin is the MOS clock for the 8086.
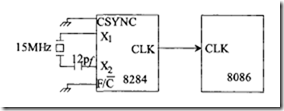
There are two more clock outputs on the 8284, the PCLK (peripheral clock) pin and the OSC (oscillator) clock pin. These signals are provided to drive peripheral ICs. The 8284 divides the frequency of the crystal at the X 1X2 pins or the external clock at the EFI pin by 6 to provide the PCLK. Therefore, the frequency of the PCLK is half the frequency of the 8284 CLK output pin. This means that for a 15-MHz crystal, the PCLK and CLK outputs are 2.5 MHz and 5 MHz respectively. Furthermore, PCLK is provided at the TTL-compatible level rather than at the MOS level. The OSC clock, on the other hand, is derived from the crystal oscillator inside the 8284 and has the same clock frequency as the crystal. Therefore, the OSC output is three times that of the CLK output. The OSC is also TTL compatible. Finally, the CSYNC (clock synchronization) input pin when connected to HIGH provides external synchronization in systems that employ multiple clocks. A typical8284 interface to the 8086 for providing a 5-MHz clock to the 8086 is shown in the following figure:
 Reset Signals
Reset Signals
When designing the microprocessor’s reset circuit, two types of reset must be considered: power-up reset and manual reset. These reset circuits must be designed using the parameters specified by the manufacturer.
Therefore, a microprocessor must be reset when its Vcc pin is connected to power. This is called "power-up reset." After some time during normal operation the microprocessor can be reset upon activation of a manual switch such as a pushbutton. A reset circuit, therefore, needs to be designed following the timing parameters associated with the microprocessor’s reset input pin specified by the manufacturer. The reset circuit, once designed, is connected to the microprocessor’s reset pin.
As mentioned before, the 8086 reset input provides a hardware mechanism for initializing the 8086 microprocessor. This is typically done at power-up to provide an orderly start-up of the system. The 8284 RES (reset input) pin when driven active LOW generates a HIGH on the 8284 reset output pin. The 8284 reset pin is connected to the 8086 reset (input) pin. As mentioned before, Intel designed the 8086 in such a way that the 8086 requires its reset pin to be HIGH for at least four clock cycles in order to obtain the physical address (FFFFOH) of the first instruction to be executed, except after power-on, which requires a 50-f.Lsec reset pulse.
According to Intel, in order to guarantee a reset from power-up, the 8086 reset input must remain below 1.05 V for 50 f!Sec after Vee has reached the minimum supply voltage of 4.5 V. The 8284 RES input can be driven by an RC circuit as shown in the following figure:
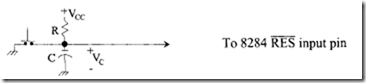
The voltage across the capacitor initially is zero upon connecting +Vee to power. If the switch is not depressed, the capacitor charges to +Vee through the resistor after a definite time determined by the time constant RC.
The charging voltage across the capacitor can be determined from the following equation. Capacitor voltage, VcCt) = vee X [1 – exp(-t/RC)], where t =50 f!Sec and VcCt) = 1.05 V, and vee = 4.5 V. Substituting these values in the equation, RC = 188 f!Sec. For example, if Cis chosen to be 0.1 f.LF, then R is 1.88 KQ.
When the switch is depressed, the 8284 RES input pin is short-circuited to ground. This takes the 8284 RES pin to LOW and thus discharges the capacitor. As the switch is released, the direct short to ground is broken. However, the 8284 RES pin remains effectively short-circuited to ground through the discharged capacitor. The capacitor now starts to recharge with time toward the +Vee voltage level.
The 8284 generates a reset signal from an internal Schmitt trigger input. A Schmitt trigger is a special analog circuit that shifts the switching threshold based on whether the input changes from LOW to HIGH or from HIGH to LOW. To illustrate this, consider a TTL Schmitt trigger inverter. Suppose that the input of this inverter is at 0 V (logic 0). The output will be approximately 3.4 V (logic 1). Now, because of the Schmitt trigger circuit, if the input voltage is increased, the output will not go to low until the value is about I.7 V. Also, after reaching a low output, the inverter will not produce a HIGH output until the input is decreased to about 0.9 V. Thus, the switching threshold for positive-going input changes is about 1.7 V and for negative-going input changes is about 0.9 V.
The difference between the two thresholds is called "hysteresis." The Schmitt trigger inverter provides I.7 V – 0.9 V = 0.8 V of hysteresis. Schmitt trigger inputs provide high noise immunity and will normally not respond to the noise encountered in microprocessor systems if its hysteresis is greater than the noise amplitude.
As the voltage across the capacitor increases with time, it remains at logic 0 level as long as the logic 1 threshold of the Schmitt trigger. Thus, the 8284 RES input is maintained at logic 0 for at least four clock cycles so that the 8284 RESET output will apply a HIGH at the 8086 reset input for at least four clock cycles. Note that whenever the 8282 RES input is at logic 0, the reset output pin of the 8284 is switched to logic I according to the timing parameters.
Ready Signals
The 8284 Ready (output) pin is connected to the 8086 Ready (input) pin to insert wait states for slow peripheral devices connected to the 8086. There are two main ways to disable this function when not used. One way is to connect the 8086 Ready pin to HIGH, and keep the 8284 Ready output pin floating. The other way is to connect the 8284 RDYI and RDY2 pins to LOW, and the AENI and AEN2 to HIGH, which will permanently disable this function. The 8284 Ready (output) pin can then be connected to the 8086 Ready input pin.
The RDYl, AENI and RDY2, AEN2 input signals provide logic for operation with multiprocessor systems and the 8284 ready output. In multiprocessor systems, these signals are used to control access over the system bus by several 8086’s. The 8284 TANK pin is replaced by the ASYNC input pin on the newer version of 8284. The ASYNC pin can be driven to LOW by a slower device to generate the 8284 READY output pin which can be connected to the 8086 READY pin. This makes it easier for the slower devices to
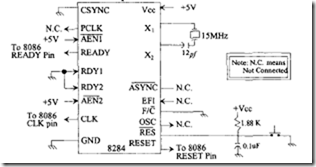 interface to the 8086. Typical8284 clock (using a 15-MHz crystal), reset, and ready signal (unused) connections to single 8086-appropriate pins are shown in the above figure.
interface to the 8086. Typical8284 clock (using a 15-MHz crystal), reset, and ready signal (unused) connections to single 8086-appropriate pins are shown in the above figure.
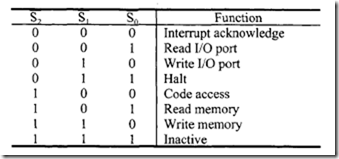
In the maximum mode, some of the 8086 pins in the minimum mode are redefined. For example, pins HOLD, HLDA, WR, M/10, DTJR, DEN, ALE, and INTA in the minimum mode are redefined as RQ/GTO, RQ/GTI, LOCK, Sb s;-, S0, QS0, and QS1 , respectively. In maximum mode, the 8288 bus controller decodes the status information from S0, s;-, and S2 to generate the bus timing and control signals that are required for a bus cycle. S0, S1, and S2 are 8086 outputs and are decoded as follows:
 The RQ/GT0 and RQ/GTl request/grant pins are used by other local bus masters to force the processor to release the local bus at the end of the processor’s current bus cycle. Each pin is bidirectional, with RQ/GTO having higher priority than RQ/GTl.These pins have internal pull-up resistors so that they may be left unconnected. The request/grant function of the 8086 works as follows:
The RQ/GT0 and RQ/GTl request/grant pins are used by other local bus masters to force the processor to release the local bus at the end of the processor’s current bus cycle. Each pin is bidirectional, with RQ/GTO having higher priority than RQ/GTl.These pins have internal pull-up resistors so that they may be left unconnected. The request/grant function of the 8086 works as follows:
-
A pulse (one clock wide) from another local bus master (RQ/GTO or RQ/GTl pin) indicates a local bus request to the 8086.
-
At the end of the current 8086 bus cycle, a pulse (one clock wide) from the 8086 to the requesting master indicates that the 8086 has relinquished the system bus and tristates the outputs. Then the new bus master subsequently relinquishes control of the system bus by sending a LOW on RQ/GTO or RQ/GTl pin. The 8086 then regains bus control.
-
The 8086 outputs LOW on the LOCK pin to prevent other bus masters from gaining control of the system bus.
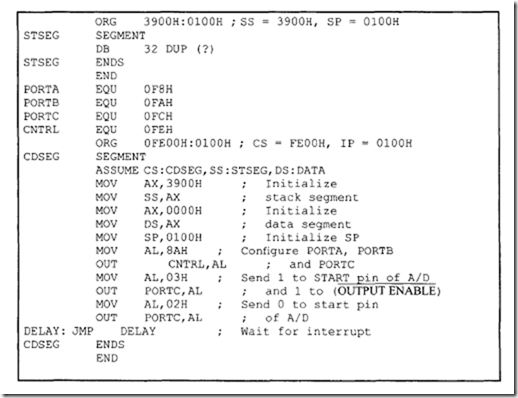
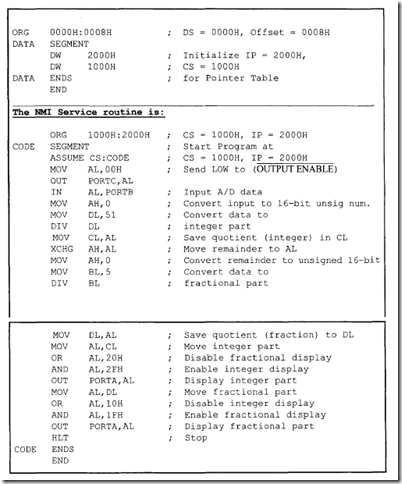
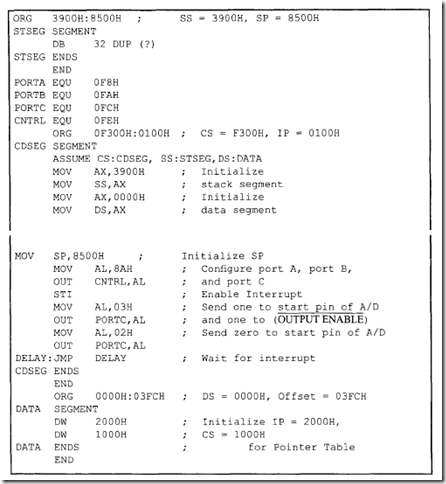
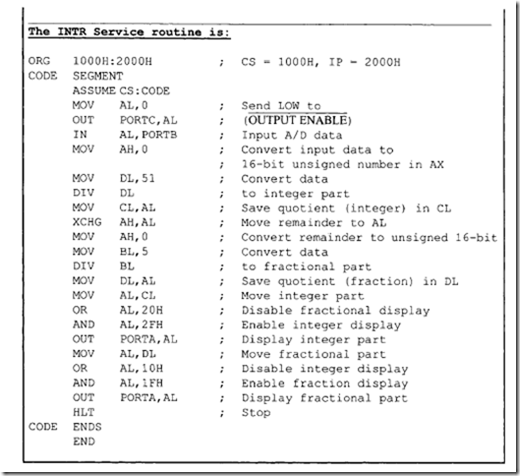
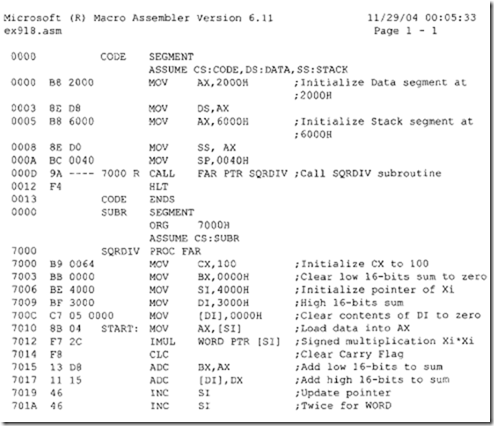
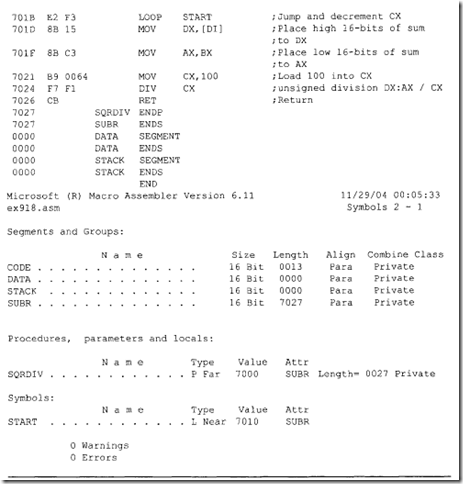
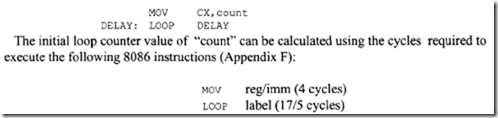
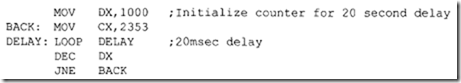
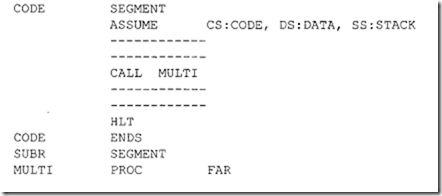
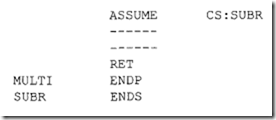
Note that since the 8086 RESET vector is located at the physical address FFFFOH, there may not be enough locations available to write programs. The following 8086 instructiQn sequence can be used with 8086 assembler (HP 64XXX) to jump to a different code segment upon hardware reset to write programs:
 The above instruction sequence will allow the 8086 to jump to the offset START (0200H) in code segment 1000H upon hardware reset where the user can write programs.
The above instruction sequence will allow the 8086 to jump to the offset START (0200H) in code segment 1000H upon hardware reset where the user can write programs.
9.9.2 Basic 8086 System Concepts
This section describes basic concepts associated with the 8086 bus cycles, address and data bus, in minimum mode.
8086 Bus Cycle
To communicate with external devices via the system for transferring data or fetching instructions, the 8086 executes a bus cycle. The 8086 basic bus cycle timing diagram is shown in Figure 9.10. The minimum bus cycle contains four microprocessor clock periods or four T states. Note that each cycle is called a T state. The bus cycle timing diagram depicted in Figure 9.10 can be described as follows:
1. During the first T state (T1), the 8086 outputs the 20-bit address computed from a segment register and an offset on the multiplexed address/data/status bus.
2. For the second T state (T2), the 8086 removes the address from the bus and either
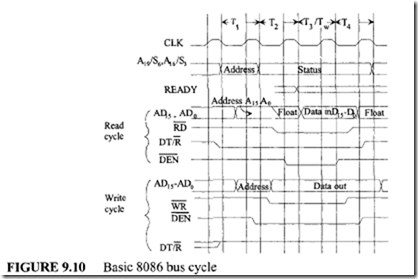
tristates or activates the AD 15-AD0 lines in preparation for reading data via the AD 15-AD0 lines during the T3 cycle. In the case of a write bus cycle, the 8086 outputs data on the AD15-AD0 lines during the T3 cycle. Also, during T2, the upper four multiplexed bus lines switch from address (A19-A16) to bus cycle status (SM S5, S4, S3). The 8086 outputs LOW on RD (for the read cycle) or WR (for the write cycle) during portion ofT2 , all ofT3, and portion ofT4 •
3. During T3 , the 8086 continues to output status information on the four A 19-A16/ S6-S3 lines and will continue to output write data or input read data to or from the AD 15-AD0 lines.
4. If the selected memory or I/O device is not fast enough to transfer data to the 8086, the memory or I/O device activates the 8086’s READY input line LOW by the start ofT3 • This will force the 8086 to insert additional clock cycles (wait
states TJafter T2 • Bus activity during Tw is the same as that during T3• When the selected device has had sufficient time to complete the transfer, it must activate the 8086 ready pin HIGH. As soon as the Tw clock period ends, the 8086 executes the last bus cycle (T4). The 8086 will latch data on the AD 15-AD0 lines during the last wait state or during T3 if no wait states are requested.
5. During T4 , the 8086 disables the command lines and the selected memory and I/O devices from the bus. Thus, the bus cycle is terminated in T4. The bus cycle appears to devices in the system as an asynchronous event consisting of an address to select the device, a register or memory location within the device, a read strobe, or a write strobe along with data.
6. The DEN and DTIR pins are used by the 8286/8287 transceiver in a minimum system. During the read cycle, the 8086 outputs DEN LOW during part of the T2 and all of the T3 cycles. This signal can be used to enable the 8286/8287 transceiver. The 8086 outputs a LOW on the DT/R pin from the start of the T1 through part of the T4 cycles. The 8086 uses this signal to receive (read) data from the receiver during T3-T4• During a write cycle, the 8086 outputs DEN LOW during part of the T1, all of the T2, and T3, and part of the T4 cycles. The signal can be used to enable the transceiver. The 8086 outputs a HIGH on DT/R throughout the 4 bus cycles to transmit (write) data to the transceiver during T3-T4 •
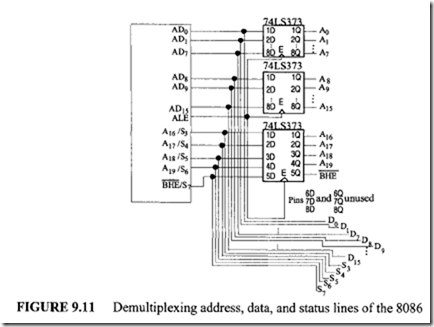
Address and Data Bus Concepts
The majority of memory and I/0 chips capable of interfacing to the 8086 require a stable address for the duration of the bus cycle. Therefore, the address on the 8086 multiplexed address/data bus during T1 should be latched. The latched address is then used to select the desired I/0 or memory location. To demultiplex the bus, the 8086 ALE pin can be used along with three 74LS373 latches.
The 74LS373 Output Control (OC) pin can be connected to ground with the 74LS373 pin represented by G or CorLE (shown as E in Figure 9.11) in data book tied to 8086 ALE. This will latch the 8086 address and BHE pins at the falling edge of ALE. Figure 9.11 shows how this can be accomplished.
The programmer views the 8086 memory address space as a sequence of one
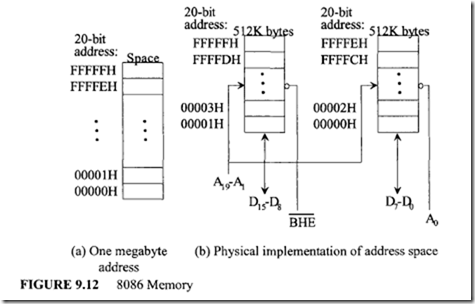
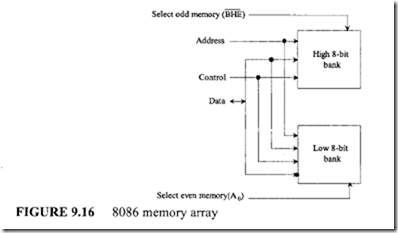
mega bytes in which any byte may contain an 8-bit data element and any two consecutive bytes may contain a 16-bit data element. There is no constraint on byte or word addresses (boundaries). The address space is physically implemented on a 16-bit data bus by dividing the address space into two banks of up to 512K bytes as shown in Figure 9.12. These banks can be selected by BHE and A0 as follows:
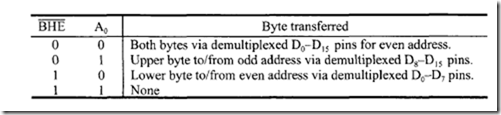
![clip_image003[1] clip_image003[1]](http://lh5.ggpht.com/-Ocq2eM63GR0/VJGzAyh05GI/AAAAAAAA9Qk/NGjAUxjdMw8/clip_image003%25255B1%25255D_thumb.gif?imgmax=800) One bank is connected to D7-D0 and contains all even-addressed bytes (A0 = 0). The other bank is connected to D 15-D8 and contains odd-addressed bytes (A0 = 1). A particular byte in each bank is addressed by A 19-A1 • The even-addressed bank is enabled by a LOW on A0, and data bytes are transferred over the DrD0 lines. The 8086 outputs a HIGH on BHE (bus high enable) and thus disables the odd-addressed bank. The 8086 outputs a LOW on BHE to select the odd-addressed bank and a HIGH on A0 to disable the even-addressed bank. This directs the data transfer to the appropriate half of the data bus.
One bank is connected to D7-D0 and contains all even-addressed bytes (A0 = 0). The other bank is connected to D 15-D8 and contains odd-addressed bytes (A0 = 1). A particular byte in each bank is addressed by A 19-A1 • The even-addressed bank is enabled by a LOW on A0, and data bytes are transferred over the DrD0 lines. The 8086 outputs a HIGH on BHE (bus high enable) and thus disables the odd-addressed bank. The 8086 outputs a LOW on BHE to select the odd-addressed bank and a HIGH on A0 to disable the even-addressed bank. This directs the data transfer to the appropriate half of the data bus.
Activation of A0 and BHE is performed by the 8086 depending on odd or even addresses and is transparent to the programmer. As an example, consider execution of the instruction MOV [ BX) ,DH. Suppose the 20-bit address computed by BX and DS is even. The 8086 outputs a LOW on A0 and a HIGH on BHE .This will select the even-addressed bank. The content of DH is placed on the D7-D0 lines by a memory chip. The 8086 writes this data via D7-D0 and automatically places it in the selected memory location. Next, consider writing a 16-bit word by the 8086 with the low byte at an even address as shown in Figure 9.13. For example, suppose that the 8086 executes the instruction MOV [BX), ex. Assume [BX] = 0004H and [DS] = 2000H. The 20-bit physical address for the word is 20004H. The 8086 outputs a LOW on both A0 and BHE, enabling both banks simultaneously. The 8086 outputs [CL] to the D7-D0 lines and [CH] to the D15-D8 lines, with WR =LOW and M/IO =HIGH. The enabled memory banks obtain the 16-bit data and write [CL] to location 20004H and [CH] to location 20005H.
Next, consider writing an odd-addressed 16-bit word by the 8086 using MOV [ BX J ,ex . For example, suppose the 20-bit physical address computed by the 8086 is 20005H. The 8086 accomplishes this transfer in two bus cycles. In the first bus cycle, the 8086 outputs a HIGH on A0 and a LOW on BHE, and thus enables the odd-addressed bank and disables the even-addressed bank. The 8086 also outputs a LOW on the WR and a HIGH on the M/IO pins. In this bus cycle, the 8086 writes data to odd memory bank via D15-D8 lines; the 8086 writes the contents of CL to address 20005H. In the second
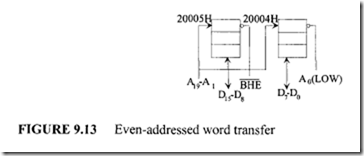
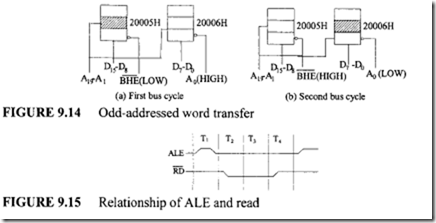 bus cycle, the 8086 outputs a LOW on A0 and a HIGH on BHE and thus enables the even addressed bank and disables the odd-addressed bank. The 8086 also outputs a LOW on the WR and a HIGH on the M/10 pins. The 8086 writes data to even memory bank via D7-D0 lines; the 8086 writes the contents of CH to address 20006H. This odd-addressed word write is shown in Figure 9.14.
bus cycle, the 8086 outputs a LOW on A0 and a HIGH on BHE and thus enables the even addressed bank and disables the odd-addressed bank. The 8086 also outputs a LOW on the WR and a HIGH on the M/10 pins. The 8086 writes data to even memory bank via D7-D0 lines; the 8086 writes the contents of CH to address 20006H. This odd-addressed word write is shown in Figure 9.14.
If memory or I/O devices are directly connected to the multiplexed bus, the designer must guarantee that the devices do not corrupt the address on the bus during T1 • To avoid this, the memory or I/O devices should have an output enable controlled by the 8086 read signal. The 8086 timing guarantees that the read is not valid until after the address is latched by ALE as shown in Figure 9.15.
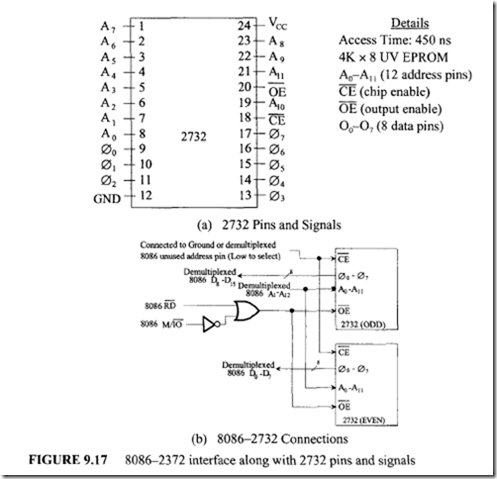
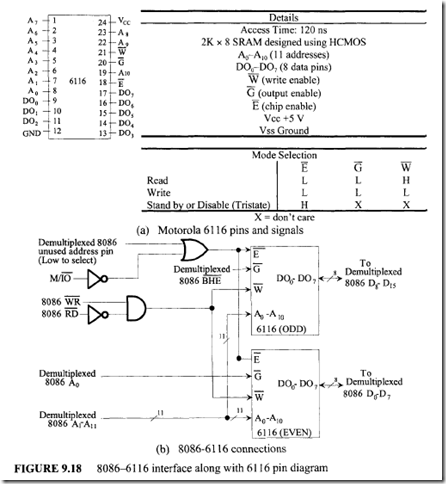
All Intel peripherals, EPROMs, and RAMs for microprocessors provide output enable for read inputs to allow connection to the multiplexed bus. Several techniques are available for interfacing the devices without output enables to the 8086 multiplexed bus. However, these techniques will not be discussed here.
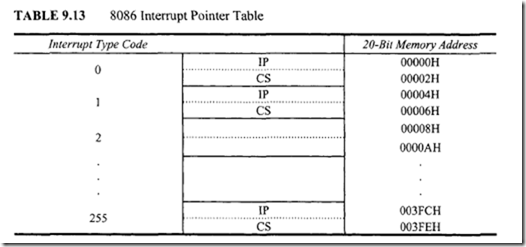
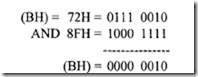
 Note here that O[BP] rather than [BP] is used because BP cannot normally be used without displacement in the 8086 assembler. Now, to set TF, the AND instruction just shown should be replaced by OR 0 [BP],OlOOH. Once TF is set to 1, the 8086 automatically generates a type 1 interrupt after execution of each instruction. The user can write a service routine at the interrupt address vector to display memory locations and/or register to debug a program. Single-step mode is nonmaskable and cannot be enabled by the STI (enable interrupt) or disabled by the CLI (disable interrupt) instruction.
Note here that O[BP] rather than [BP] is used because BP cannot normally be used without displacement in the 8086 assembler. Now, to set TF, the AND instruction just shown should be replaced by OR 0 [BP],OlOOH. Once TF is set to 1, the 8086 automatically generates a type 1 interrupt after execution of each instruction. The user can write a service routine at the interrupt address vector to display memory locations and/or register to debug a program. Single-step mode is nonmaskable and cannot be enabled by the STI (enable interrupt) or disabled by the CLI (disable interrupt) instruction.