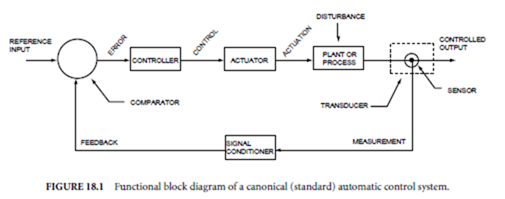
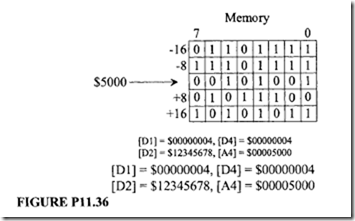
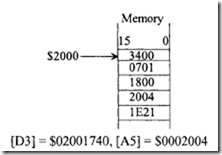
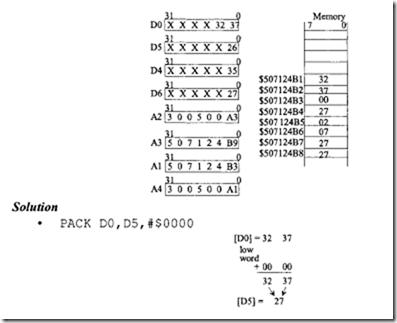
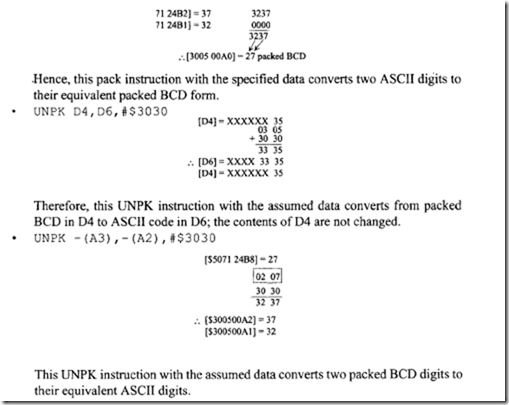
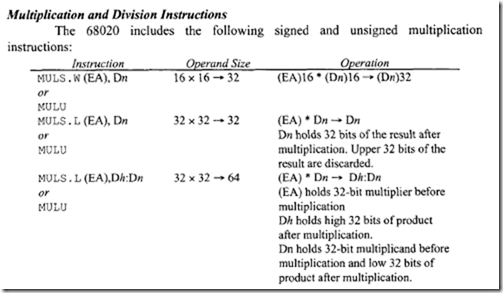
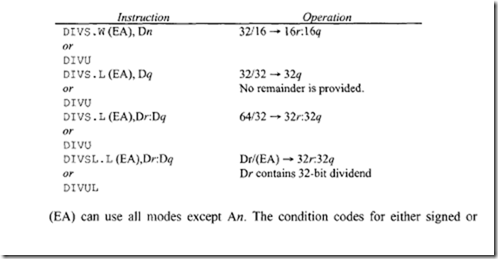
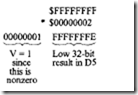
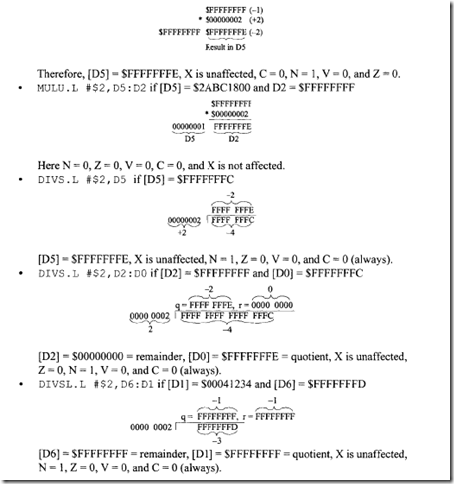
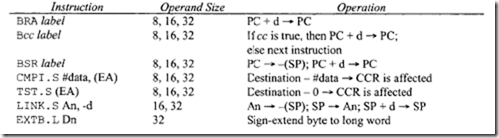
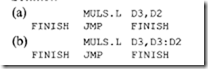
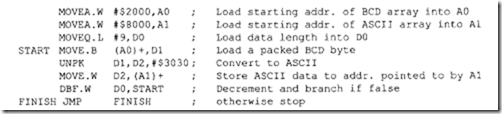
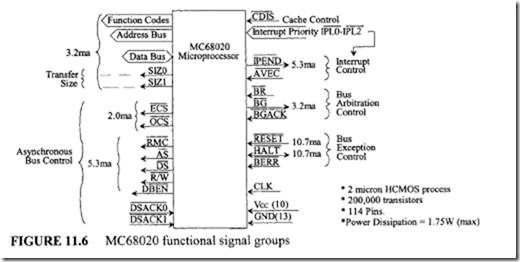
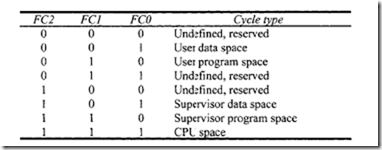
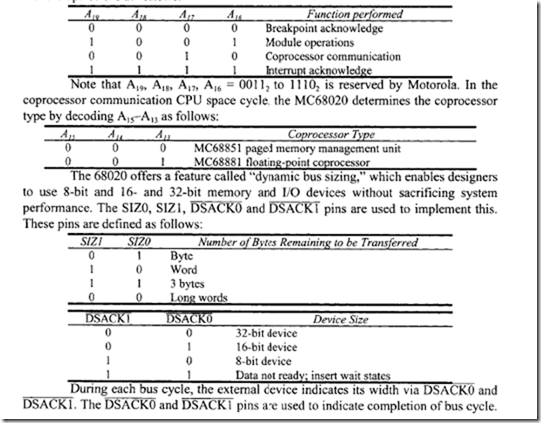
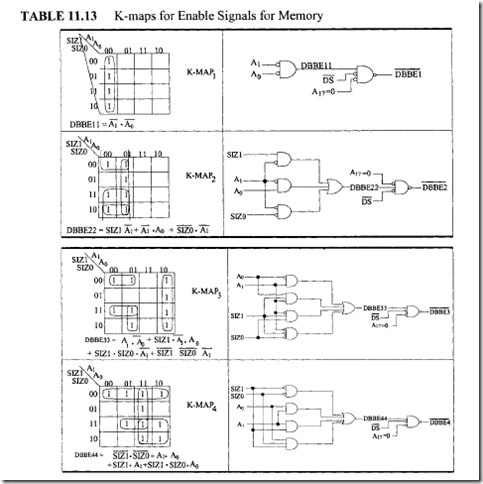
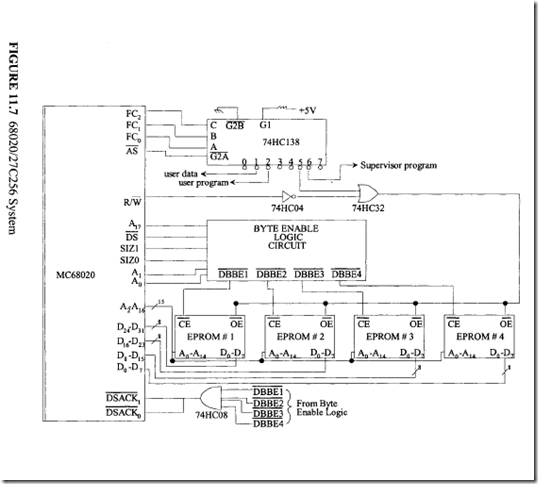
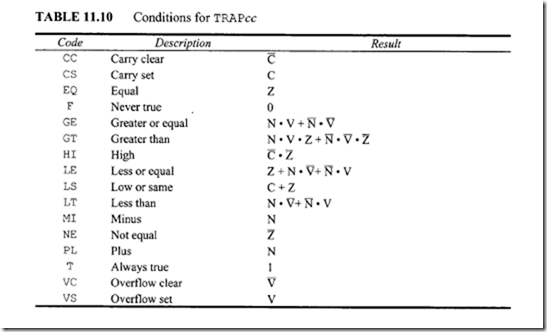
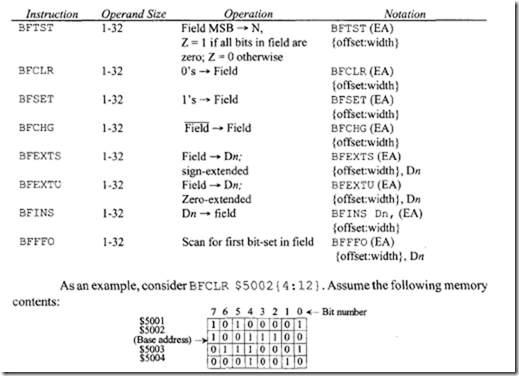
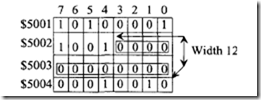
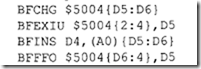
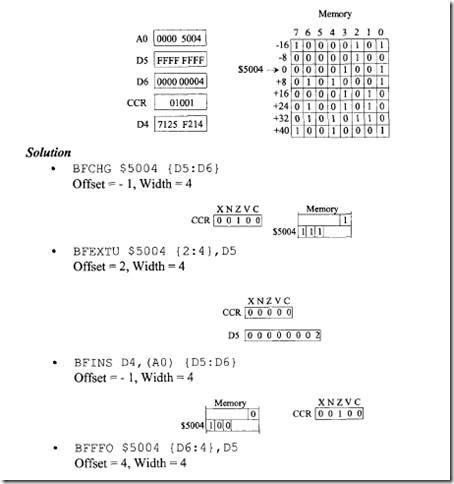
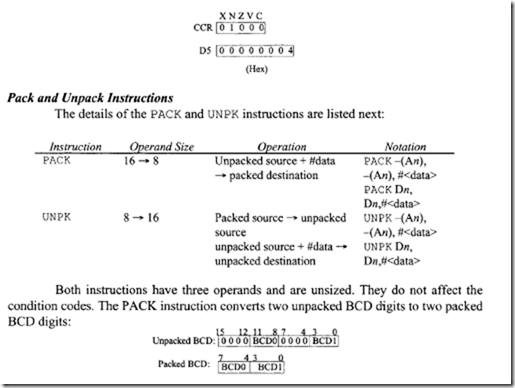
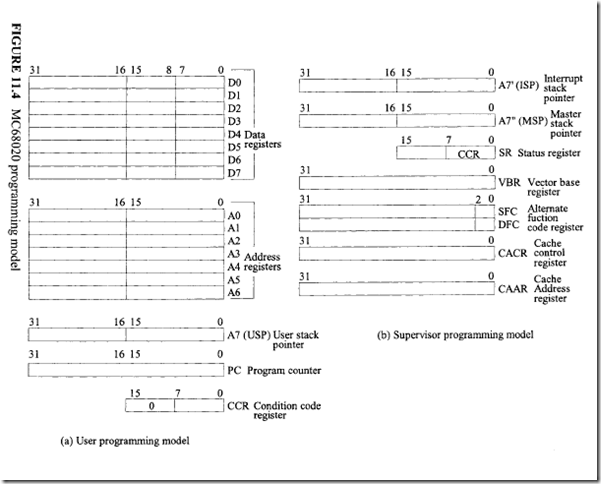
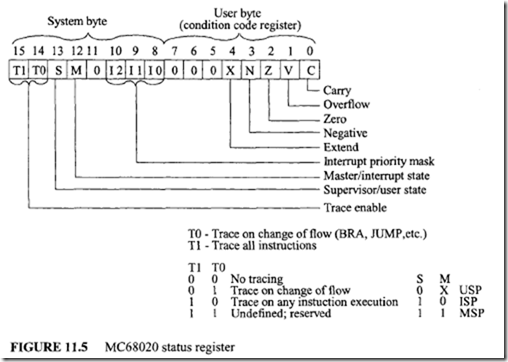
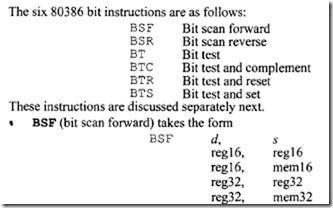
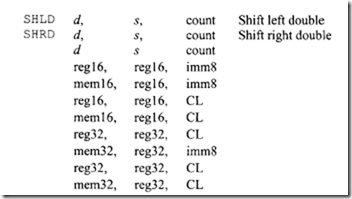
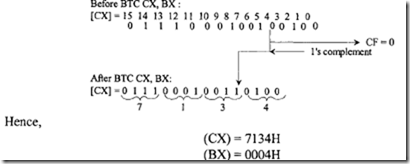
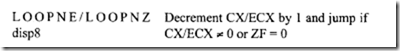18.1.1 Process Transducers
This section discusses transducers used in measuring and controlling the process variables most frequently encountered in industrial processes, namely
✁ Fluid pressure
✁ Fluid flow
✁ Liquid level
✁ Temperature
Fluid Pressure Transducers
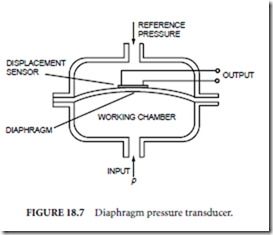
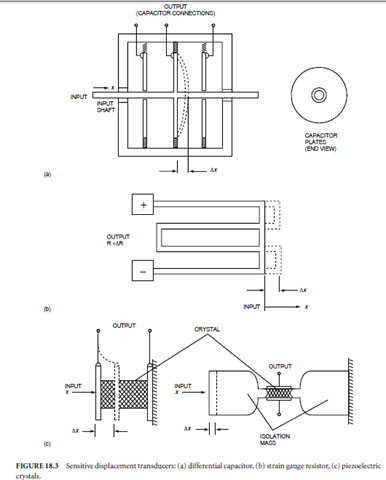
Most fluid pressure transducers are of the elastic type, in which the fluid is confined in a chamber with at least one elastic wall, and the deflection of the elastic wall is taken as an indication of the pressure. The Bourdon tube and the bellows are examples of elastic pressure transducers, which are used in laboratory-grade transducers and in some industrial process control applications. The fluid pressure transducer depicted in Fig. 18.7, which uses an elastic diaphragm to separate two chambers, is the type most frequently encountered in industrial process control. Diaphragms are constructed from one of a variety of elastic materials ranging from thin metal to polymerized fabric.
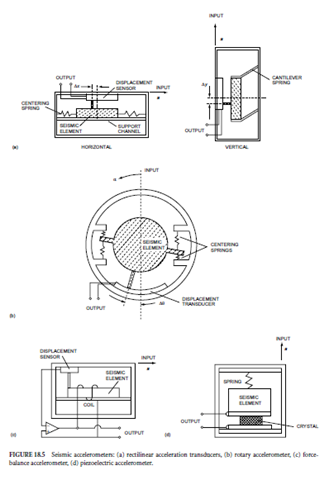
For gross pressure measurements, the displacement of the diaphragm is sensed by a potentiometer or LVDT; for more sensitive pressure measurements, any one of the three sensitive displacement sensors described earlier is used. In the most common configuration for sensitive pressure transducers, a strain gauge resistor with a rosette pattern is bonded to the diaphragm. In another configuration, the outer walls of the pressure sensor serve as capacitor plates and the diaphragm serves as the common plate of a differential capacitor. In a very sensitive and highly integrated configuration, the diaphragm is a silicon wafer with a piezoresistive strain gauge and signal conditioningcircuits integrated into silicon.
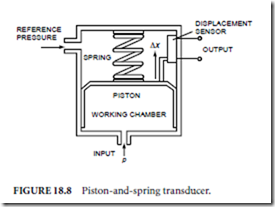
High-vacuum (very low pressure) measurements, usually based on observations of viscosity, thermal conductivity, acoustic properties, or ionization potential of the fluid, will not be included in this discussion. Transducers used in high-pressure hydraulic systems (70 MPa (10,000 psi) or greater) are usually of the piston and spring type (Fig. 18.8).
In either of the pressure transducers, the output is actually a measure of the difference in pressure between the working chamber and the reference chamber of the transducer (i.e., pOUT = p − pREF). The measurement is called
✁ An absolute pressure if the reference chamber is sealed and evacuated (i.e., pREF = 0 and pOUT = p)
✁ A gauge pressure if the reference chamber is vented to the atmosphere (i.e., pOUT = p − pATM)
✁ A differential pressure if any other pressure is applied to the reference chamber
Fluid Flow Transducers (Flowmeters)
Flowmetering, because of the number of variables involved, encompasses a wide range of measurement technology and applications. In industrial processes, the term fluid is applied not only to gases and liquids, but also to flowable mixtures (often called slurries or sludges) such as concrete, sewage, or wood pulp. Control of a fluid flow, and hence the type of measurement required, may involve volumetric flow rate, mass flow rate, or flow direction. Gas flows may be compressible, which also influences the measurement technique. In addition, the condition of the flow—whether or not it is homogenous and clean (free of suspended particles)—has a bearing on flowmeter technology. Another factor to be considered is flow velocity; slow moving laminar flows of viscous material require different measurement techniques than those used for high-velocity turbulent flows. Still another consideration is confinement of the flow. Whereas most fluid flow measurements are concerned with full flow through closed channels such as ducts and pipes, some applications require measurements of partial flow through open channels such as troughs and flumes. Only the most widely used flowmeters are considered here.
The major categories of flowmeters are
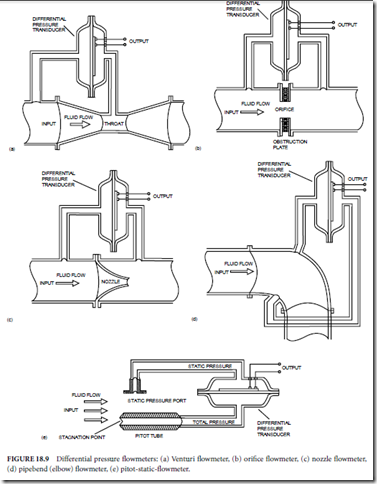
✁ Differential pressure, constriction-type (venturi, orifice, flow nozzle, elbow (or pipe bend), and pitot static) (Fig. 18.9)
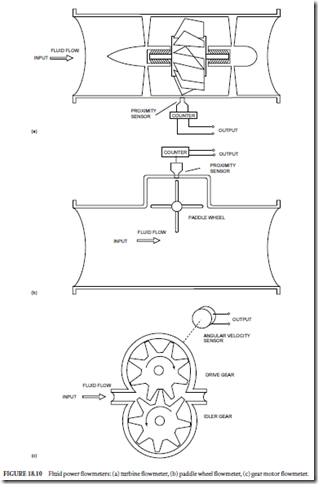
✁ Fluid-power (gear motors, turbines and paddle wheels) (Fig. 18.10)
✁ Ultrasound (Fig. 18.11)
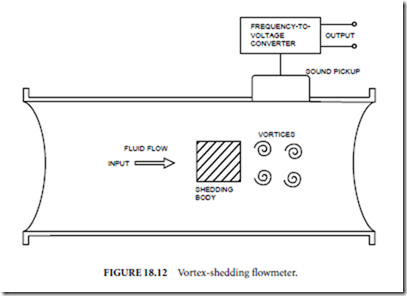
✁ Vortex shedding (Fig. 18.12)
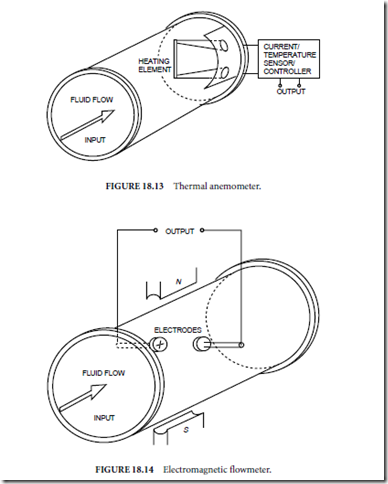
✁ Thermal anemometer (Fig. 18.13)
✁ Electromagnetic (Fig. 18.14)
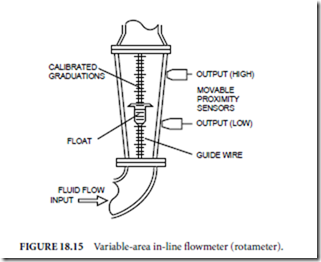
✁ Rotameter (variable-area in-line flowmeter) (Fig. 18.15)
Differential pressure flowmeters are suited to high- and moderate-velocity flow of gas and clean, low- viscosity liquids. Venturi flowmeters (Fig. 18.9(a)) are the most accurate, but they are large and expensive. Orifice flowmeters (Fig. 18.9(b)) are smaller, less expensive, and much less accurate than venturi flowmeters. Nozzle flowmeters (Fig. 18.9(c)) are a compromise between venturi and orifice flowmeters. Pipe-bend flowmeters (Fig. 18.9(d)), which can essentially be installed in any bend in an existing piping system, are used primarily for gross flow rate measurements. Pitot-static flowmeters (Fig. 18.9(e)) are used in flows which have a large cross-sectional area, such as in wind tunnels. Pitot-static flowmeters are also used in freestream applications such as airspeed indicators for aircraft.
Fluid-power flowmeters are used in low-velocity, moderately viscous flows. In addition to industrial control applications, turbine flowmeters (Fig. 18.10(a)) are sometime used as speed indicators for ships or boats. Paddle wheel flowmeters (Fig. 18.10(b)) are used both in closed- and open-flow applications such as liquid flow in flumes. Since a fluid-power gear motor (Fig. 18.10(c)) is a constant volume device, motor shaft speed is always a direct indication of fluid flow rate.
Ultrasound flowmeters of the transmission type (Fig. 18.11(a)), which are based on the principle that the sound transmission speed will be increased by the flow rate of the fluid, are used in all types of clean, subsonic flows. Doppler flowmeters (Fig. 18.11(b)) rely on echoes from within the fluid, and are thus only useful in dirty flows that carry suspended particles or turbulent flows that produce bubbles. Ultrasound flowmeters are nonintrusive devices, which can often be retrofitted to existing duct or pipe systems.
Vortex shedding flowmeters (Fig. 18.12) introduce a shedding body into the flow to cause production (shedding) of vortices. The sound accompanying the production and collapse of the vortices is monitored and analyzed. The dominant frequency of the sound is indicative of the rate of vortex production and collapse, and hence an indication of flow rate. Vortex shedding flowmeters are useful in low-velocity, nonturbulent flows.
Thermal anemometers (Fig. 18.13) are used in low-velocity gas flows with large cross-sectional area, such as in heating, ventilation, and air conditioning (HVAC) ducts. Convection cooling of the heating element is related to flow rate. The flow rate measurement is based either on the current required to maintain a constant temperature in the heating element, or alternatively on the change in temperature when the current is held constant.
Electromagnetic flowmeters (Fig. 18.14) are useful for slow moving flows of liquids, sludges, or slurries. The flow material must support electrical conduction between the electrodes, and so in some cases it is necessary to ionize the flow upstream from the measurement point in order to use an electromagnetic flowmeter.
Variable-area in-line flowmeters (Fig. 18.15), or rotameters, are sometimes referred to as sight gauges because they provide a visible indication of flow rate. These devices, when fitted with proximity sensors (such as capacitive pickups), which sense the presence of the float, can be used in on-off control applications.
Liquid Level Transducers
Liquid-level measurements are relatively straightforward, and the transducers fall into the categories of contact or noncontact. Measurements may be continuous, in which the liquid level is monitored continuously throughout its operating range, or point, in which the liquid level is determined to be above or below some predetermined level.
The contact transducers encountered most frequently are
✁ Float
✁ Hydrostatic pressure
✁ Electrical capacitance
✁ Ultrasound
The noncontact transducers encountered most frequently are
✁ Capacitive proximity sensors
✁ Ultrasound
✁ Radio frequency
✁ Electro-optical
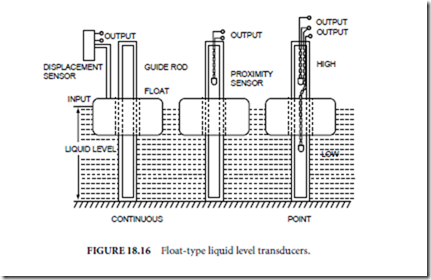
Float-type liquid level transducers are available in a wide variety of configurations for both continuous and point measurements. One possible configuration is depicted in Fig. 18.16 for continuous measurement and for both single- and dual-point measurements.
Hydrostatic pressure liquid level transducers may be used in either vented or pressurized applications (Fig. 18.17). In either case the differential pressure is directly proportional to the weight of the liquid column, since the differential pressure transducer accounts for surface pressure.
Capacitance probes (Fig. 18.18(a)) are widely used in liquid level measurements. It is possible, when the tank walls are metal, to use a single bare or insulated metal rod as one capacitor plate and the tank walls as the other. More frequently, capacitance probes consist of a metal rod within a concentric cylinder open at the ends, which makes the transducer independent of the tank construction. An interesting application of this type of capacitance probe is in aircraft fuel quantity indicators. Capacitance switches can be utilized as depicted in Fig. 18.18(b) to provide noncontact point measurements of liquid level.
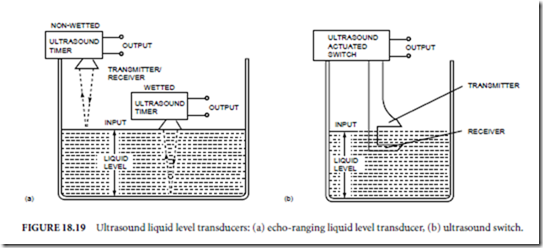
Ultrasound echo ranging transducers can be used in either wetted (contact) or nonwetted (noncontact) configurations for continuous measurement of liquid level (Fig. 18.19(a)). An interesting application of wetted transducers is as depth finders and fish finders for ships and boats. Nonwetted transducers can also be used with bulk materials such as grains and powders. Radio-frequency and electro-optic liquid level transducers are usually noncontact, echo ranging devices, which are similar in principle and application to the nonwetted ultrasound transducer.
Ultrasonic transducers can also be adapted to point measurements by locating the transmitter and the receiver opposite one another across a gap (Fig. 18.19(b)). When liquid fills the gap, attenuation of the
ultrasound energy is markedly less than when air fills the gap. The signal conditioning circuits utilize this sharp increase in the level of ultrasound energy detected by the receiver to activate a switch.
Temperature Transducers
Temperature measurement is generally based on one of the following physical principles:
✁ Thermal expansion
✁ Thermoelectric phenomena
✁ Thermal effect on electrical resistance
✁ Thermal effect on conductance of semiconductor junctions
✁ Thermal radiation
(Strictly speaking, any device used to measure temperature may be called a thermometer, but more descriptive terms are applied to devices used in temperature control.)
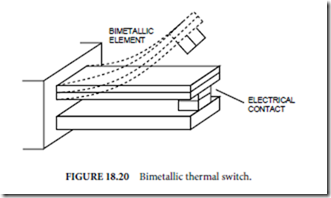
Bimetallic switches (Fig. 18.20) are widely used in on-off temperature control systems. If two metal strips with different coefficients of thermal expansion are bonded together while both strips are at the same temperature, the bimetallic structure will bend when the temperature is changed. Although these devices are often called thermal cutouts, implying that they are used in normally closed switches, they can be fabricated in either normally closed or normally open configurations. The bimetallic elements can also be fabricated in coil or helical configurations to extend the range of motion due to thermal expansion.
Thermocouples are rugged and versatile temperature sensors frequently found in industrial control systems. A thermocouple consists of a pair of dissimilar metal wires twisted or otherwise bonded at one end. The Seebeck effect is the physical phenomena which accounts for thermocouple operation, so thermocouples are known alternatively as Seebeck junctions. The potential difference (Seebeck voltage) between the free ends of the wire is proportional to the difference between the temperature at the junction and the temperature at the free ends. Thermocouples are available for measurement of temperature as low as −270◦C and as high as 2300◦C, although no single thermocouple covers this entire range. Thermocouples are identified as type B, C, D, E, G, J, K, N, R, S, or T, according to the metals used in the wire.
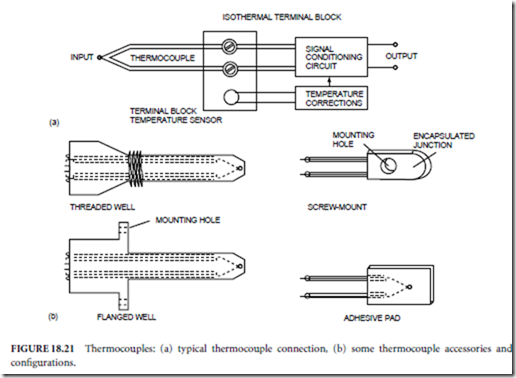
Signal conditioning and amplification of the relatively small Seebeck voltage dictates that the thermocouple wires must be connected to the terminals of a signal conditioning circuit. These connections create two additional Seebeck junctions, each of which generates its own Seebeck voltage, which must be canceled in the signal conditioning circuit. To implement cancellation to the corrections the following are necessary (Fig. 18.21(a)):
✁ The input terminals of the signal conditioning circuit must be made of the same metal.
✁ The two terminals must be on an isothermal terminal block so that each Seebeck junction created
by the connection is at the same temperature.
✁ The temperature of the terminal block must be known.
The first two requirements are met by appropriate construction of the signal conditioning circuit. The third requirement is met by using a reference temperature sensor, probably an IC temperature transducer of the type described later.
Thermocouple and thermocouple accessories are fabricated for a variety of applications (Fig. 18.21(b)). Protective shields are used to protect thermocouple junctions in corrosive environments or where con- ducting liquids can short circuit the thermocouple voltage; however, exposed (bare) junctions are used wherever possible, particularly when fast response is essential.
Resistance temperature detectors (RTDs) are based on the principle that the electrical resistivity of most metals increases predictably with temperature. Platinum is the preferred metal for RTDs, although other less expensive metals are used in some applications. The resistivity of platinum is one of the standards by which temperature is measured. The relatively good linearity of the resistivity of platinum over a wide temperature range (−200–800◦C) makes platinum RTDs suitable for stable, accurate temperature transducers, which are easily adapted to control systems applications.
The disadvantage of the RTD is that the temperature-sensitive element is a rather fragile metal filament wound on a ceramic bobbin or a thin metal film deposited on a ceramic substrate. RTD elements are usually encapsulated and are rarely used as bare elements. The accessories and application packages used with RTDs are similar to those used with thermocouples (Fig. 18.21(b)).
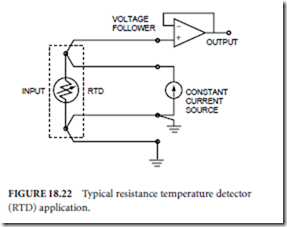
Most platinum RTDs are fabricated to have a nominal resistance of 100 Φ at 0◦C. The resistance temperature coefficient of platinum is approximately 3–4 mΦ/ Φ/◦C, so resolution of temperature to within 1◦C for a nominal 100-Φ RTD element requires resolution of the absolute resistance within 0.3–0.4 Φ. These resistance resolution requirements dictate use of special signal conditioning techniques to cancel the lead and contact resistance of the RTD element (Fig. 18.22). The circuit depicted in Fig. 18.22 is a variation of a 4-wire ohmmeter. Most RTDs are manufactured with four leads to be compatible with such circuits.
Thermistors are specially prepared metal oxide semiconductors that exhibit a strong negative temperature coefficient, in sharp contrast to the weak positive temperature coefficient of RTDs. Nominal thermistor resistance, usually specified for 25◦C, ranges from less than 1000 Φ to more than 1 MΦ, with sensitivities greater than 100 Φ/◦C. Thus, the thermistor is the basis for temperature sensors that are much more sensitive and require less special signal conditioning than either thermocouples or RTDs.
The tradeoff is the marked nonlinearity of the resistance-temperature characteristic. To minimize this problem, manufacturers provide packages in which the thermistor has been connected into a resistor network chosen to provide a relatively linear resistance-temperature characteristic over a nominal temperature range.
The development of thermistor technology has lead to the IC temperature sensor in which the temperature-sensitive junction(s) and the required signal conditioning circuits are provided in a monolithic package. The user is only required to provide a supply voltage (typically 5 V DC) to the IC in order to obtain an analog output voltage proportional to temperature. Thermistors and IC temperature sensors can be produced in very small packages, which permit highly localized temperature measurements.
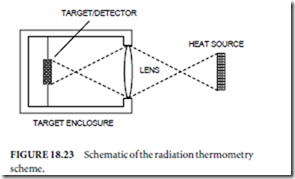
Some thermistors designed for biological research are mounted in the tip of a hypodermic needle. The shortcomings of both thermistor and IC temperature sensors are that they are not rugged, cannot be used in caustic environments, and are limited to temperatures below approximately 200◦C. Radiation thermometers are used for remote (non- contact) sensing of temperature in situations where the contact sensors cannot be used. Operation is based on the principles of heat transfer through thermal radiation. Radiation thermometers focus the infrared energy from a heat source onto a black body (target) within the radiation thermometer enclosure (Fig. 18.23). One of the contact temperature sensors described previously is incorporated into the target to measure the target temperature.
The rise in temperature at the target is related to the source temperature. Typical radiation thermometers have standoff ranges (focal lengths) of 0.5–1.5 m, but instruments with focal length as short as 1 cm or as long as 10 m are available. Radiation thermometers are available for broadband, monochromatic, or two-color thermometry.