MC68020 Addressing Modes
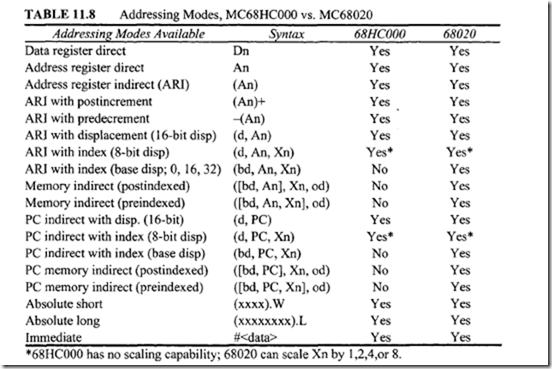
Table 11.7 lists the MC68020’s 18 addressing modes. Table 11.8 compares the addressing
TABLE 11.7 68020 Addressing Modes
 modes of the 68HC000 with those of the MC68020. Because 68HC000 addressing modes were covered earlier in this chapter in detail with examples, the 68020 modes not available in the 68HC000 will be covered in the following discussion.
modes of the 68HC000 with those of the MC68020. Because 68HC000 addressing modes were covered earlier in this chapter in detail with examples, the 68020 modes not available in the 68HC000 will be covered in the following discussion.
ARI (Address Register Indirect) with Index (Scaled) and 8-Bit Displacement
-
Assembler syntax: (d8, An, Xn.size *scale)
-
EA =(An)+ (Xn.size *scale)+ d8
-
Xn can be W or L.
If the index register (An or Dn) is 16 bits, then it is sign-extended to 32 bits and multiplied by 1, 2, 4 or 8 to be used in EA calculations. An example is MOVE • w ( 0 , A2 , D2 • W * 2) ,D1. Suppose that [A2] = $50000000, [D2.W] = $1000, and [$50002000] = $1571; then, after the execution of this MOVE, [D1]1owJ 6 bits = $1571 because EA = $5000000 + $1000 * 2 + 0 = $50002000.
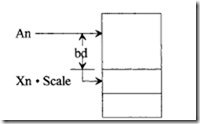
ARI (Address Register Indirect) with Index and Base Displacement
-
Assembler syntax: (bd, An, Xn.size *scale)
-
EA =(An)+ (Xn.size *scale)+ bd
-
Base displacement, bd, has value 0 when present or can be 16 or 32 bits.
The following figure (next page) shows the use of ARI with index, Xn, and base displacement, bd, for accessing tables or arrays:
An example is MOVE.W ($5000, A2, Dl.W * 4), D5. If [A2] = $30000000, [Dl.W) = $0200, and [$30005800] = $0174, then, after execution of this MOVE, [D5]1ow 16 hits = $0174 because EA = $5000 + $30000000 + $0200 * 4 = $30005800.
Memory Indirect
Memory indirect mode is distinguished from address register indirect mode by the use of square brackets in the assembler notation. The concept of memory indirect mode is depicted in the following figure:
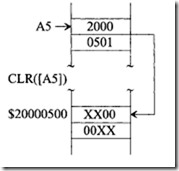 Here, register A5 points to the effective address $20000501. Because CLR ( [AS] ) is a 16-bit clear instruction, 2 bytes in location $20000501 and $20000502 are cleared to 0.
Here, register A5 points to the effective address $20000501. Because CLR ( [AS] ) is a 16-bit clear instruction, 2 bytes in location $20000501 and $20000502 are cleared to 0.
Memory indirect mode can be indexed with scaling and displacements. There are two types of memory indirect mode with scaled indexing and displacements: postindexed memory indirect mode and preindexed memory indirect mode. For postindexed memory indirect mode, an indirect memory address is first calculated using the base register (An) and base displacement (bd). This address is used for an indirect memory access of a long word followed by adding a scaled indexed operand and an optional outer displacement (od) to generate the effective address. Note that bd and od can be zero, 16 bits, or 32 bits. In postindexed memory indirect mode, indexing occurs after memory indirection.
-
Assembler syntax: ([bd, An], Xn.size *scale, od)
-
EA = ([bd +An])+ (Xn.size *scale+ od)
AnexampleisMOVE.W ( [$0004, Al], Dl.W * 2, 2), D2.If[Al)=$20000000, [$2000004] = $00003000, [D1.W] = $0002, and [$00003006] = $1A40, then, after execution of this MOVE, intermediate pointer= (4 + $20000000) = $20000004, [$2000004], which is $00003000 used as a pointer. Therefore, EA = $00003000 + $00000004 + 2 = $00003006. Hence, [D2]10w 16 bits= $1A40.
For memory indirect preindexed mode, the scaled index operand is added to the base register (An) and base displacement (bd). This result is then used as an indirect address into the data space. The 32-bit value at this address is read and an optional outer displacement (od) is added to generate the effective address. The indexing, therefore, occurs before indirection.
-
Assembler syntax: ([bd, An, Xn.size * scale], od)
-
EA = (bd, An+ Xn.size *scale)+ od
As an example of the preindexed mode, consider several I/O devices in a system. The addresses of these devices can be held in a table pointed to by An, bd, and Xn. The actual programs for these devices can be stored in memory pointed to by the respective device addresses plus od.
The memory indirect preindexed mode will now be illustrated by a numerical example. Consider
MC68020 Instruction Set
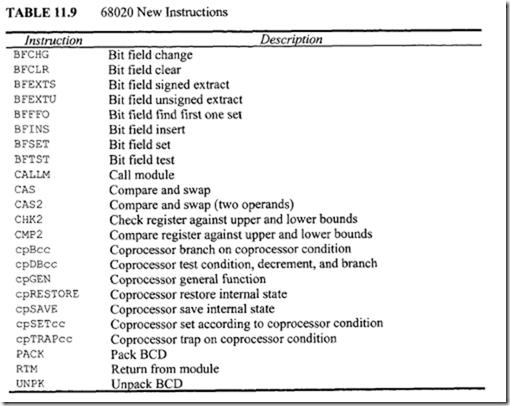
The MC68020 instruction set includes all68HC000 instructions plus some new ones. Some of the 68HC000 instructions are enhanced. Over 20 new instructions are added to provide new functionality. A list of these instructions is given in Table 11.9.
Succeeding sections will discuss the 68020 instructions listed next:
-
68020 new privileged move instructions
-
RTD instruction
-
CHK/CHK2 and CMP/CMP2 instructions
-
TRAPcc instructions
-
Bit field instructions
-
PACK and UNPK instructions
-
Multiplication and division instructions
-
68HC000 enhanced instructions
68020 New Privileged Move Instructions
The 68020 new privileged move instructions can be executed by the 68020 in the supervisor mode. They are listed below:
The operand size (.L) indicates that the MOVEC operations are always long word.
Notice that only register to register operations are allowed. A control register (Rc) can be copied to an address or a data register (Rn) or vice versa. When the 3 bit SFC or DFC register is copied into Rn, all 32 bits of the register are overwritten and the upper 29 bits are "0."
The MOVES (move to alternate space) instruction allows the operating system to access any addressed space defined by the function codes. It is typically used when an operating system running in the supervisor mode must pass a pointer or value to a previously defined user program or data space. The operand size (.S) indicates that the MOVES instruction can be byte (.B), word (.W), or long word (.L). The MOVES instruction allows register to memory or memory to register operations. When a memory to register move occurs, this instruction causes the contents of the source function code register to be placed on the external function hardware pins. For a register to memory move, the processor places the destination function code register on the function code pins. The MOVES instruction can be used to move information from one space to another.
Example 11.3
(a) Find the contents of address $70000023 and the function code pins FC2, FC1 , and FC0 after execution of MOVES. B DS, (AS). Assume the following data prior to execution of this MOVES instruction: [SFC] = 0012 , [DFC] = 1012 , [A5] = $70000023, [D5] = $718F2A05, [$70000020] = $01, [$70000021] = $F 1, [$70000022] = $A2, [$70000023] =$2A
Solution
After execution of this MOVES instruction,
FC2 FC1 FC0 = 1012 , [$70000023] = $05
(b) The following 68000 instruction sequence:
MOVEA. L 8 (A7) ,A0
MOVE.W (A0),D3
is used by a subroutine to access a parameter whose address has been passed into AO and then moves the parameter to D3. Find the equivalent 68020 instruction.
Solution MOVE. W ( [ 8, A 7] ) ,D3
Return and DeIocate Instruction
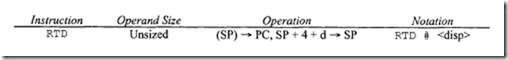
The return and delocate (RTD) instruction is useful when a subroutine has the responsibility to remove parameters off the stack that were pushed onto the stack by the calling routine. Note that the calling routine’s JSR (jump to subroutine) or BSR (branch to subroutine) instructions do not automatically push parameters onto the stack prior to the call as do the CALLM instructions. Rather, the pushed parameters must be placed there using the MOVE instruction. The format of the RTD instruction is shown next:
As an example, consider RTD #8, which, at the end of a subroutine, deallocates 8 bytes of unwanted parameters off the stack by adding 8 to the stack pointer and returns to the main program. The size of the displacement is 16-bit.
CHK/CHK2 and CMP/CMP2 Instructions
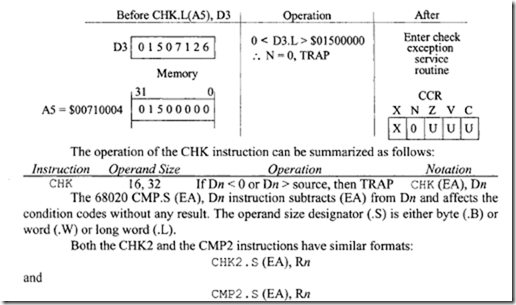
The 68020 check instruction (CHK) compares a 32-bit twos complement integer value residing in a data register (Dn) against a lower bound (LB) value of zero and against an upper bound (UB) value of the programmer’s choice. The upper bound value is located at the effective address (EA) specified in the instruction format. The CHK instruction has the following format: CHK. S (EA), Dn where the operand size (.S) designates word (.W) or long word (.L).
If the data register value is less than zero (Dn < 0) or if the data register is greater than the upper bound (Dn > UB), then the processor traps through exception vector 6 (offset $18) in the exception vector table. Of course, the operating system or the programmer must define a check service handler routine at this vector address. The condition codes after execution of the CHK are affected as follows: If Dn < 0 then N = 1; if Dn > UB (upper bound) then N =0. If 0 Dn UB then N is undefined. X is unaffected and all other flags are undefined and program execution continues with the next instruction.
The CHK instruction can be used for maintaining array subscripts because all subscripts can be checked against an upper bound (i.e., UB =array size- 1). If the compared subscript is within the array bounds (i.e., 0 subscript value UB value), then the subscript is valid, and the program continues normal instruction execution. If the subscript value is out of array limits (i.e., 0 > subscript value or subscript value> UB value), then the processor traps through the CHK exception.
Example 11.4
Determine the effects of execution of CHK.L (AS), D3, where AS represents a memory pointer to the array’s upper bound value. Register D3 contains the subscript value to be checked against the array bounds. Assume the following data prior to execution of this CHK instruction:
Solution
[D3] = $01S07126
[AS]= $00710004
[$00710004] = $01S00000
The long word array subscript value $01S07126 contained in data register D3 is compared against the long word UB value $01S00000 pointed to by address register AS. Because the value $01S07126 contained in D3 exceeds the UB value $01S00000 pointed to by AS, the N bit is cleared. (X is unaffected and the remaining CCR bits are undefined.) This out-of bounds condition causes the program to trap to a check exception service routine.
They compare a value contained in a data or address register (designated by Rn ) against two (2) bounds chosen by the programmer. The size of the data to be compared (.S) may be specified as byte (.B), word (.W), or long word (.L). As shown in the following figure, the lower bound (LB) value must be located in memory at the effective address (EA) specified in the instruction, and the upper bound (UB) value must follow immediately at the next higher memory address. That is, UB addr = LB addr + size, where size= B (+1), W (+2), or L (+4).
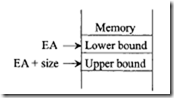 If the compared register is a data register (i.e., Rn = Dn) and the operand size (.S) is a byte or word, then only the appropriate low-order part of the data register is checked. If the compared register is an address register (i.e., Rn =An) and the operand size (.S) is a byte or word, then the bound operands are sign-extended to 32 bits and the extended operands are compared against the full 32 bits of the address register. After execution of CHK2 and CMP2, the condition codes are affected as follows:
If the compared register is a data register (i.e., Rn = Dn) and the operand size (.S) is a byte or word, then only the appropriate low-order part of the data register is checked. If the compared register is an address register (i.e., Rn =An) and the operand size (.S) is a byte or word, then the bound operands are sign-extended to 32 bits and the extended operands are compared against the full 32 bits of the address register. After execution of CHK2 and CMP2, the condition codes are affected as follows:
In the case where an upper bound equals the lower bound, the valid range for comparison becomes a single value. The only difference between the CHK2 and CMP2 instructions is that, for comparisons determined to be out of bounds, CHK2 causes exception processing utilizing the same exception vector as the CHK instructions, whereas the CMP2 instruction execution affects only the condition codes.
In both instructions, the compare is performed for either signed or unsigned bounds. The 68020 automatically evaluates the relationship between the two bounds to determine which kind of comparison to employ. If the programmer wishes to have the bounds evaluated as signed values, the arithmetically smaller value should be the lower bound. If the bounds are to be evaluated as unsigned values, the programmer should make the logically smaller value the lower bound.
The following CMP2 and CHK2 instruction examples are identical in that they both utilize the same registers, comparison data, and bound values. The difference is how the upper and lower bounds are arranged.
Example 11.5
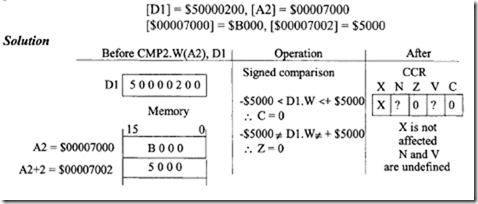
Determine the effects of execution of CMP2. W (A2) ,Dl. Assume the following data prior to execution of this CMP2 instruction:
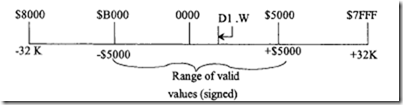
In this example, the word value $B000 contained in memory (as pointed to by address register A2) is the lower bound and the word value $5000 immediately following $B000 is the upper bound. Because the lower bound is the arithmetically smaller value, the programmer is indicating to the 68020 to interpret the bounds as signed numbers. The twos complement value $B000 is equivalent to an actual value of -$5000. Therefore,·the instruction evaluates the word contained in data register D 1 ($0200) to determine whether it is greater than or equal to the upper bound, +$5000, or less than or equal to the lower bound, -$5000. Because the compared value $0200 is within bounds, the carry bit (C) is cleared to 0. Also, because $0200 is not equal to either bound, the zero bit (Z) is cleared. The following figure shows the range of valid values that D 1 could contain:
A typical application for the CMP2 instruction would be to read in a number of user entries and verify that each entry is valid by comparing it against the valid range bounds. In the preceding CMP2 example, the user-entered value would be in register Dl and register A2 would point to a range for that value. The CMP2 instruction would verify whether the entry is in range by clearing the CCR carry bit if it is in bounds and setting the carry bit if it is out of bounds.
Example 11.6
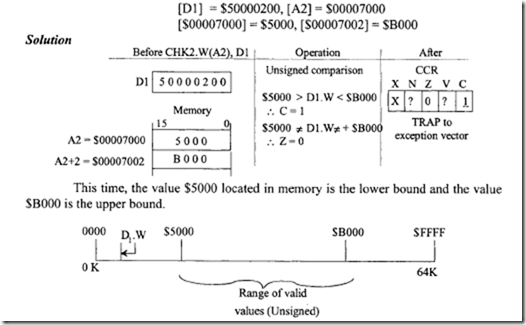
Determine the effects of execution of CHK2. W (A2) , 01. Assume the following data prior to execution of this CHK2 instruction:
Now, because the lower bound contains the logically smaller value, the programmer is indicating to the 68020 to interpret the bounds as unsigned numbers, representing only a magnitude. Therefore, the instruction evaluates the word contained in register Dl ($0200) to determine whether it is greater than or equal so the lower bound, $5000, or less than or equal to the upper bound, $B000. Because the compared value $0200 is less than $5000, the carry bit is set to indicate an out of bounds condition and the program traps to the CHK/ CHK2 exception vector service routine. Also, because $0200 is not equal to either bound, the zero bit (Z) is cleared. The figure above shows the range of valid values that Dl could contain.
A typical application for the CHK2 instruction would be to cause a trap exception to occur if a certain subscript value is not within the bounds of some defined array. Using the CHK2 example format just given, if we define an array of 100 elements with subscripts ranging from 0- 9910, and if the two words located at (A2) and (A2 + 2) contain 50 and 99, respectively, and register Dl contains 10010,then execution of the CHK2 instruction would cause a trap through the CHK/CHK2 exception vector. The operation of the CMP2 and CHK2 instructions are summarized as follows:
 Trap-on-Condition Instructions
Trap-on-Condition Instructions
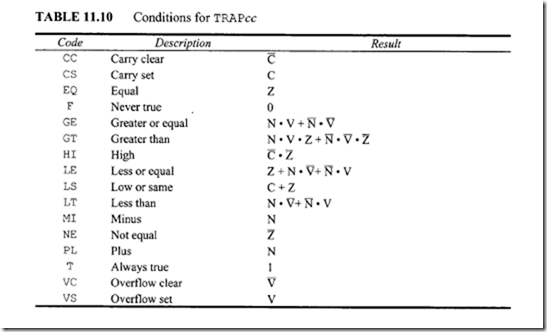
The new trap condition (TRAPcc) instruction allows a conditional trap exception on any of the condition codes shown in Table 11.10. These are the same conditions that are
allowed for the set-on-condition (Sec) and the branch-on-condition (Bee) instructions. The TRAPcc instruction evaluates the selected test condition based on the state of the condition code flags, and if the test is true, the 68020 initiates exception processing by trapping through the same exception vector as the TRAPV instruction (vector 7, offset $1C, VBR = VBR +offset). The trap-on-condition instruction format is
TRAPcc or TRAPcc.S #<data>
where the operand size (.S) designates word (.W) or long word (.L).
If either a word or long word operand is specified, a 1-or 2-word immediate operand is placed following the instruction word. The immediate operand(s) consists of argument parameters that are passed to the trap handler to further define requests or services it should perform. If cc is false, the 68020 does not interpret the immediate operand(s) but instead adjusts the program counter to the beginning of the following instruction. The exception handler can access this immediate data as an offset to the stacked PC. The stacked PC is the next instruction to be executed.
A summary of the TRAPcc instruction operation is shown next:
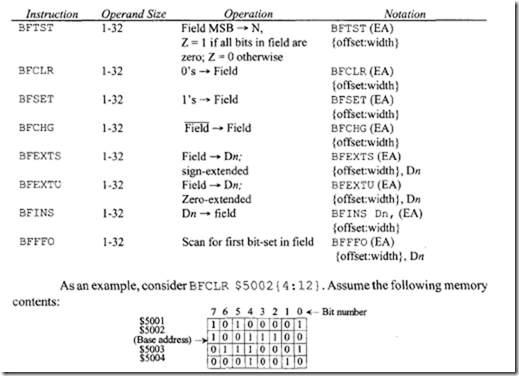
The bit field instructions, which allow operations to clear, set, ones complement, input, insert, and test one or more bits in a string of bits (bit field), are listed on the next page. Note that the condition codes are affected according to the value in the field before execution of the instruction. All bit field instructions affect the N and Z bits as shown for BFT ST. That is, for all instructions, Z = 1 if all bits in a field prior to execution of the instruction are zero; Z = 0 otherwise. N = 1 if the most significant bit of the field prior to execution of the instruction is one; N = 0 otherwise. C and V are always cleared. X is always unaffected. Next, consider BFFFO. The offset of the first bit set 1 in a bit field is placed in Dn; if no set bit is found, Dn contains the offset plus the field width.
Immediate offset is from 0 to 31, whereas offset in Dn can be specified from -231 to 231 – 1. All instructions are unsized. They are useful for memory conservation, graphics, and communications. The bit field instructions are listed below:
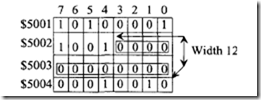
Bit 7 of the base address $5002 has the offset 0. Therefore, bit 3 of$5002 has the offset value of 4. Bit 0 oflocation $5001 has offset value -1, bit 1 of $5001 has offset value -2, and so on. The example BFCLR instruction just given clears 12 bits starting with bit 3 of$5002. Therefore, bits 0-3 of location $5002 and bits 0-7 oflocation $5003 are cleared to 0. Therefore, the memory contents change as follows:
The use of bit field instructions may result in memory savings. For example, assume that an input device such as a 12-bit AID converter is interfaced via a 16-bit port of a MC68020 based microcomputer. Now, suppose that I million pieces of data are to be collected from this port. Each 12 bits can be transferred to a 16-bit memory location or bit field instructions can be used.
Using a 16-bit location for each 12 bits:
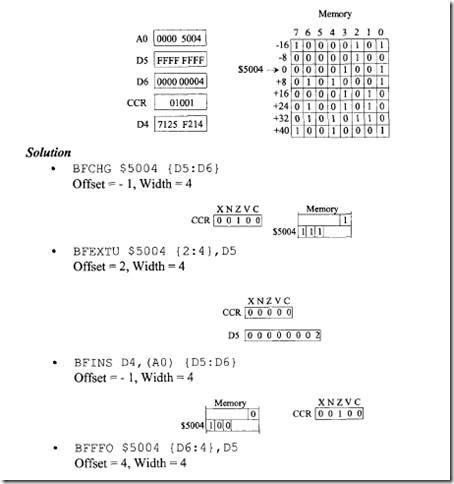
Example 11.7
Determine the effect of each of the following bit field instructions:
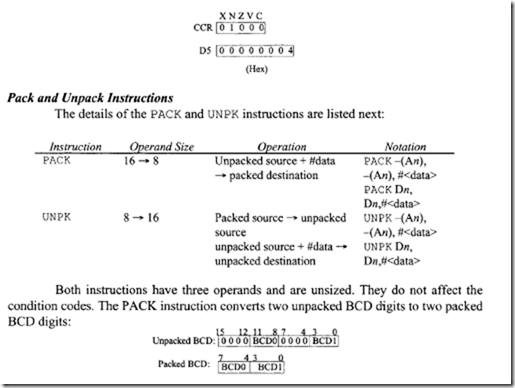
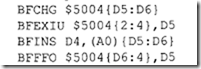 Assume the following data prior to execution of each of the given instructions. Register contents are given in hex, CCR and memory contents in binary, and offset to the left of memory in decimal.
Assume the following data prior to execution of each of the given instructions. Register contents are given in hex, CCR and memory contents in binary, and offset to the left of memory in decimal.
The UNPK instruction reverses the process and converts two packed BCD digits to two unpacked BCD digits. Immediate data can be added to convert numbers from one code to another. That is, these instructions can be used to translate codes such as ASCII or EBCDIC to a BCD and vice versa.
The PACK and UNPK instructions are useful when I/O devices such as an ASCII keyboard and an ASCII printer are interfaced to an MC68020-based microcomputer. Data can be entered into the microcomputer via the keyboard in ASCII codes. The PACK instruction can be used with appropriate adjustments to convert these ASCII codes into packed BCD. Arithmetic operations can be performed inside the microcomputer, and the result will be in packed BCD. The UNPK instruction can similarly be used with appropriate adjustments to convert packed BCD to ASCII codes for outputting to the ASCII printer.