■ SUMMARY
A high level programming language like C or Pascal allows the low-level architecture of a computer to be treated as an abstraction. An assembly language program, on the other hand, takes a form that is very dependent on the underlying architecture. The instruction set architecture (ISA) is made visible to the programmer, who is responsible for handling register usage and subroutine linkage. Some of the complexity of assembly language programming is managed through the use of macros, which differ from subroutines or functions, in that macros generate in-line code at assembly time, whereas subroutines are executed at run time.
A linker combines separately assembled modules into a single load module, which typically involves relocating code. A loader places the load module in memory and starts the execution of the program. The loader may also need to perform relocation if two or more load modules overlap in memory.
In practice the details of assembly, linking and loading is highly system-dependent and language-dependent. Some simple assemblers merely produce executable binary files, but more commonly an assembler will produce additional information so that modules can be linked together by a linker. Some systems provide linking loaders that combine the linking task with the loading task. Others separate linking from loading. Some loaders can only load a program at the address specified in the binary file, while more commonly, relocating loaders can relocate pro- grams to a load-time-specified address. The file formats that support these processes are also operating-system dependent.
Before compilers were developed, programs were written directly in assembly language. Nowadays, assembly language is not normally used directly since compilers for high-level languages are so prevalent and also produce efficient code, but assembly language is still important for understanding aspects of computer architecture, such as how to link programs that are compiled for different calling conventions, and for exploiting extensions to architectures such as MMX and AltiVec.
■ FURTHER READING
Compilers and compilation are treated by (Aho et al, 1985) and (Waite and Carter, 1993). There are a great many references on assembly language programming. (Donovan, 1972) is a classic reference on assemblers, linkers, and loaders. (Gill et al., 1987) covers the 68000. (Goodman and Miller, 1993) serves as a good instructional text, with examples taken from the MIPS architecture. The appendix in (Patterson and Hennessy, 1998) also covers the MIPS architecture. (SPARC, 1992) deals specifically with the definition of the SPARC, and SPARC assembly language.
Aho, A. V., Sethi, R., and Ullman, J. D., Compilers, Addison Wesley Longman, Reading, Massachusetts (1985).
Donovan, J. J., Systems Programming, McGraw-Hill, (1972).
Gill, A., E. Corwin, and A. Logar, Assembly Language Programming for the 68000, Prentice-Hall, Englewood Cliffs, New Jersey, (1987).
Goodman, J. and K. Miller, A Programmer’s View of Computer Architecture, Saun- ders College Publishing, (1993).
Patterson, D. A. and J. L. Hennessy, Computer Organization and Design: The Hardware / Software Interface, 2/e, Morgan Kaufmann Publishers, San Mateo, California, (1998).
SPARC International, Inc., The SPARC Architecture Manual: Version 8, Prentice Hall, Englewood Cliffs, New Jersey, (1992).
Waite, W. M., and Carter, L. R., An Introduction to Compiler Construction, Harper Collins College Publishers, New York, New York, (1993).
■ PROBLEMS
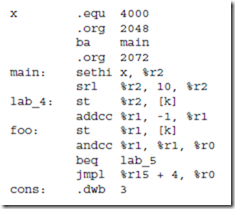
5.1 Create a symbol table for the ARC segment shown below using a form similar to Figure 5-7. Use “U” for any symbols that are undefined.
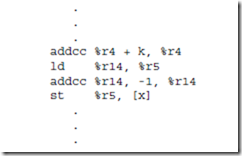
5.2 Translate the following ARC code into object code. Assume that x is at location (4096)10.
5.3 Create a symbol table for the program shown in Figure 5-8, using a form similar to Figure 5-7.
5.4 Translate subroutine add_64 shown in Figure 5-8, including variables A,
B, and C, into object code.
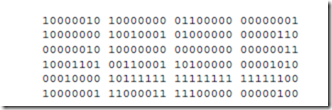
5.5 A disassembler is a software program that reads an object module and recreates the source assembly language module. Given the object code shown below, disassemble the code into ARC assembly language statements. Since there is not enough information in the object code to determine symbol names, choose symbols as you need them from the alphabet, consecutively, from ‘a’ to ‘z.’
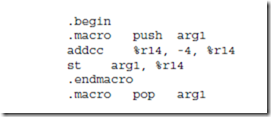
5.6 Given two macros push and pop as defined below, unnecessary instruc- tions can be inserted into a program if a push immediately follows a pop. Expand the macro definitions shown below and identify the unnecessary instructions.
5.7 Write a macro called return that performs the function of the jmp 1 statement as it is used in Figure 5-5.
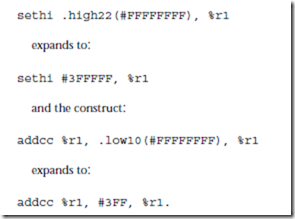
5.8 In Figure 4-16, the operand x for sethi is filled in by the assembler, but the statement will not work as intended if x ³ 222 because there are only 22 bits in the imm22 field of the sethi format. In order to place an arbitrary 32-bit address into %r5 at run time, we can use sethi for the upper 22 bits, and then use addcc for the lower 10 bits. For this we add two new pseudo-ops: .high22 and .low10, which construct the bit patterns for the high 22 bits and the low 10 bits of the address, respectively. The construct:
Rewrite the calling routine in Figure 4-16 using .high22 and .low10 so that it works correctly regardless of where x is placed in memory.
5.9 Assume that you have the subroutine add_64 shown in Figure 5-8 avail-
able to you. Write an ARC routine called add_128 that adds two 64-bit numbers, making use of add_64. The two 128-bit operands are stored in memory locations that begin at x and y, and the result is stored in the memory location that begins at z.
5.10 Write a macro called subcc that has a usage similar to addcc, that sub- tracts its second source operand from the first.
5.11 Does ordinary, nonrecursive macro expansion happen at assembly time or at execution time? Does recursive macro expansion happen at assembly time or at execution time?
5.12 An assembly language programmer proposes to increase the capability of the push macro defined in Figure 5-9 by providing a second argument, arg2. The second argument would replace the addcc %r14, -4, %r14 with addcc arg2, -4, arg2. Explain what the programmer is trying to accomplish, and what dangers lurk in this approach.