Wide Area Networks
Applications
Wide Area Network Architecture
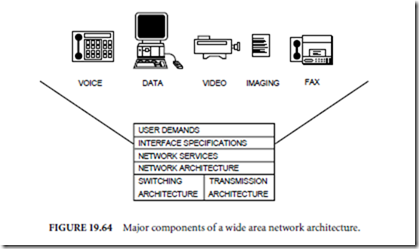
To better understand all of the current and emerging wide area networking technologies and services, a simple model defining the major segments and interrelationships of an overall wide area network architecture is shown in Fig. 19.64. User demands are the driving force behind the current and emerging
wide area network services which are offered to business and residential customers. Companies offering these services are in business to generate profits by implementing the underlying architectures that will enable them to offer the wide area networking services that users are demanding at the lowest possible cost. Users are demanding simple, transparent access to variable amounts of bandwidth as required. In addition, this wide area network access must offer support for transmission of data, video, imaging, and fax as well as voice. One of the primary driving forces of increased capacity and sophistication for wide area network services is LAN interconnection.
Circuit Switching vs. Packet Switching
Switching of some type or another is necessary in a wide area network because the alternative is unthinkable. To explain, without some type of switching mechanism or architecture, every possible source of data in the world would have to be directly connected to every possible destination of data in the world, not a very likely prospect.
Circuit Switching
Switching allows temporary connections to be established, maintained, and terminated between message sources and message destinations, sometime called sinks in data communications. In the case of the voice- based phone network with which most people are familiar, a call is routed through a central office piece of equipment known as a switch, which creates a temporary circuit between the source phone and the phone of the party to whom one wishes to talk. This connection or circuit only lasts for the duration of the call. This switching technique is known as circuit switching and is one of two primary switching techniques employed to deliver messages from here to there. In a circuit switched network, a switched dedicated circuit is created to connect the two or more parties, eliminating the need for source and destination address information such as that provided by packetizing techniques.
The switched dedicated circuit established on circuit switched networks makes it appear to the user of the circuit as if a wire has been run directly between the phones of the calling parties. The physical resources required to create this temporary connection are dedicated to that particular circuit for the duration of the connection. If system usage should increase to the point where insufficient resources are available to create additional connections, users would not get a dial tone.
Packet Switching
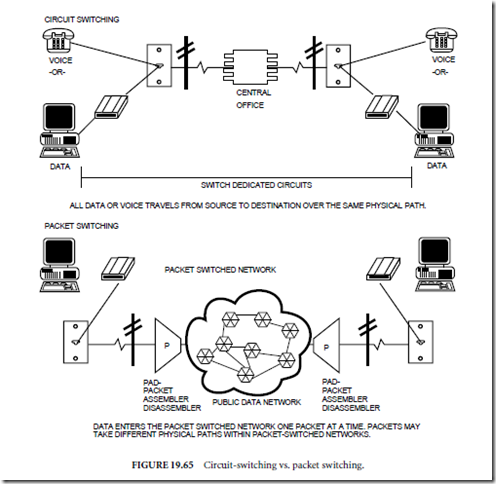
The other primary switching technique employed to deliver messages from here to there is known as packet switching. Packet switching differs from circuit switching in several key areas. First, packets travel one at a time from the message source through a packet switched network, otherwise known as a public data network, to the message destination. A packet switched network is represented in network diagrams by a symbol which resembles a cloud. Figure 19.65 illustrates such a symbol, as well as the difference between circuit switching and packet switching. The cloud is an appropriate symbol for a packet switched network since all that is known is that the packet of data goes in one side of the public data network (PDN) and comes out the other. The physical path which any packet takes may be different than other packets and in any case, is unknown to the end users. What is beneath the cloud in a packet switched network is a large number of packet switches, which pass packets among themselves as the packets are routed from source to destination. Remember that packets are specially structured groups of data, which include control and address information in addition to the data itself. These packets must be assembled (control and address information added to data) somewhere before entry into the packet switched network and must be subsequently dis- assembled before delivery of the data to the message destination. This packet assembly and disassembly is done by a device known as a packet assembler/disassembler (PAD). PADs may be stand-alone devices or may be integrated into modems or multiplexers.
These PADs may be located at an end-user location, or may be located at the entry point to the packet switched data network. Figure 19.65 illustrates the latter scenario in which the end users employ regular modems to dial up the value added network (VAN) or on-line information service, which provides the PADs to properly assemble the packets prior to transmission over the packet switched network.
Packet Switched Networks
The packet switches illustrated inside the PDN cloud in Fig. 19.65 are generically known as data switching exchanges (DSEs), or packet switching exchanges (PSEs). DSE is the packet switching equivalent of the DCE (data communications equipment) and DTE (data terminal equipment) categorization for modems and dial-up transmission.
Another way in which packet switching differs from circuit switching is that as demand for transmission of data increases on a packet switched network, additional users are not denied access to the packet switched network. Overall performance of the network may suffer, errors and retransmission may occur, or packets of data may be lost, but all users experience the same degradation of service. This is because, in the case of a packet switched network, data travel through the network one packet at a time, traveling over any available path within the network rather than waiting for a switched dedicated path as in the case of the circuit switched network.
For any packet switch to process any packet of data bound for anywhere, it is essential that packet ad- dress information be included on each packet. Each packet switch then reads and processes each packet by making routing and forwarding decisions based on the packet’s destination address and current network conditions. The full destination address uniquely identifying the ultimate destination of each packet is known as the global address.
Because an overall data message is broken up into numerous pieces by the packet assembler, these message pieces may actually arrive out of order at the message destination due to the speed and condition of the alternate paths within the packet switched network over which these message pieces (packets) traveled. The data message must be pieced back together in proper order by the destination PAD before final transmission to the destination address. These self-sufficient packets containing full source and destination address information plus a message segment are known as datagrams.
A Business Perspective on Circuit-Switching vs Packet Switching
If the top-down model were applied to an analysis of possible switching methodologies, circuit switching and packet switching could be properly placed on either the network or technology layers. In either case, in order to make the proper switching methodology decision, the top-down model layer directly above the network layer, namely, the data layer must be thoroughly examined. The key data layer question becomes: What is the nature of the data to be transmitted and which switching methodology best supports those data characteristics? The first data-related criteria to examine is the data source. What is the nature of the application program (application layer) which will produce this data? Is it a transaction oriented program or more of a batch update or file oriented program?
A transaction oriented program, producing what is sometimes called interactive data, is characterized by short bursts of data followed by variable length pauses due to users reading screen prompts or pauses between transactions. This bursty transaction-oriented traffic, best categorized by banking transactions at an automatic teller machine, must be delivered as quickly and reliably as the network can possibly perform. In addition to data burstiness, time pressures, and reliability constraints are other important data characteristics that will assist in switching methodology decision making.
Applications programs more oriented to large file transfers or batch updates have different data characteristics than transaction oriented programs. Overnight updates from regional offices to corporate headquarters or from local stores to regional offices are typical examples. Rather than occurring in bursts, the data in these types of applications are usually large and flowing steadily. These transfers are important, but often not urgent. If file transfers fail, error detection and correction protocols can retransmit bad data or even restart file transfers at the point of failure.
Defining Terms
Carrier sense multiple access with collision detection (CSMA/CD): A scheme for network communication flow.
Client: The end-users of a network and its resources, typically workstations or personal computers.
Ethernet: A network architecture adhering to IEEE 802.3; a CSMA/CD-based architecture traditionally installed in a bus configuration, but more recently typically in a hub-based star physical topology.
Fiber distributed data interface (FDDI): A networking scheme using separate rings around which data move simultaneously in opposite directions to achieve high speed and operational redundancy.
Gateway: A network device designed to provide a transparent connection between two totally different computing environments.
Hub: The heart of a star physical topology, alternatively known as a concentrator, repeater, or multistation access unit (MAU).
Network interface card (NIC): The physical device or circuit used to interface the network with a local workstation or device.
Network management: The overall task of monitoring and analyzing network traffic and correcting network-related problems.
Open systems interconnection (OSI) model: A framework for organizing networking technology developed by the International Standards Organization.
Router: A device that reads specific network layer protocols in order to maximize filtering and forwarding rates on a network.
Server: The element of a network designed to facilitate and manage the sharing of resources among client devices and workstations.
Token ring: A network architecture adhering to IEEE 802.5, utilizing a star physical topology, sequential message delivery, and a token passing access methodology.
Wireless LAN: An emerging networking system utilizing radio or infrared media as the interconnection method between workstations.
References
Bachus, K. and Longsworth, E. 1993. Road nodes. Corporate Computing 2(3):54–61.
Bradner, S. and Greenfield, D. 1993. Routers: Building the highway. PC Magazine 12(6):221–270.
Derfler, F. 1993. Ethernet adapters: Fast and efficient. PC Magazine 12(3):191.
Derfler, F. 1993. Making the WAN connection: Linking LANs. PC Magazine 12(5):183–206.
Derfler, F. 1993. Network printing: Sharing the wealth. PC Magazine 12(2):249.
Derfler, F. 1993. To catch a thief. PC Magazine 12(16):NE1–NE9.
Derfler, F. 1994. Extend your reach. PC Magazine 13(14):315–351.
Derfler, F. 1994. Peer-to-peer LANs: Peer pressure. PC Magazine 13(8):237–274.
Donovan, W. 1993. A pain-free approach to SNA internetworking. Data Communications 22(16):99.
Gasparro, D. 1994. Putting wireless to work. Data Communications 23(5):57–58.
Goldman, J. 1995. Applied Data Communications: A Business Oriented Approach. Wiley, New York.
Greenfield, D. 1993. To protect and serve. PC Magazine 12(9):179.
Gunnerson, G. 1993. Network operating systems: Playing the odds. PC Magazine 12(18):285–333.
Harvey, D. and Santalesa, R. 1994. Wireless gets real. Byte 19(5):90.
Held, G. 1993. Internetworking LANs and WANs. Wiley, New York.
Held, G. 1994. The Complete Modem Reference. Wiley, New York.
Held, G. 1994. Ethernet Networks: Design Implementation, Operation and Management. Wiley, New York.
Held, G. 1994. Local Area Network Performance Issues and Answers. Wiley, New York.
Heywood, D. et al. 1992. LAN Connectivity. New Riders, Carmel, IN.
Jander, M. and Johnson, J. 1993. Managing high speed WANs: Just wait. Data Communications 22(7):83.
Johnson, J. 1993. LAN modems: The missing link for remote connectivity. Data Communications 22(4):101.
Johnson, J. 1994. Wireless data: Welcome to the enterprise. Data Communications 23(5):42–55.
Karney, J. 1993. Network lasers: Built for speed. PC Magazine 12(20):199.
Madron, T. 1993. Peer-to-Peer LANs: Networking Two to Ten PCs. Wiley, New York.
Mandeville, R. 1994. Ethernet switches evaluated. Data Communications 23(4):66–78.
Mathias, C. 1994. New LAN gear naps unseen desktop chains. Data Communications 23(5):75–80.
Peterson, M. 1993. Network backup evolves. PC Magazine 12(16):277–311.
Pompili, T. 1994. The high speed relay. PC Magazine 13(1):NE1–NE12.
Quiat, B. 1994. V.FAST, ISDN, or switched 56 K. Network Computing 5(3):70.
Raskin, R. 1993. Antivirus software: Keeping up your guard. PC Magazine 12(5):209–264.
Rosen, B. and Fromme, B. 1993. Toppling the SNA internetworking language barrier. Data Communications 22(9):79.
Saunders, S. 1993. Choosing high speed LANs: Too many technologies, too little time? Data Communications 22(13):58–70.
Saunders, S. 1994. Building a better token ring network. Data Communications 23(7):75.
Saunders, S. 1994. Full duplex ethernet: More niche than necessity? Data Communications 23(4):87–92.
Schlar, S. 1990. Inside X.25: A Manager’s Guide. McGraw–Hill, New York.
Shimada, K. 1994. Fast talk about fast ethernet. Data Communications 23(5):21–22.
Stallings, W. 1992. ISDN and Broadband ISDN, 2nd ed. Macmillan, New York.
Stevenson, T. 1993. Best of a new breed: Groupware—Are we ready? PC Magazine 12(11):267–297.
Tabibian, O.R. 1994. Remote access: It all comes down to management. PC Magazine 13(14):NE1–NE22.
Thomas, R. 1994. PPP starts to deliver on interoperability promises. Data Communications 23(6):83.
Tolly, K. 1993. Can routers be trusted with critical data? Data Communications 22(7):58.
Tolly, K. 1993. Checking out channel-attached gateways. Data Communications 22(8):75.
Tolly, K. 1993. Token ring adapters: Evaluated for the enterprise. Data Communications 22(3):73.
Tolly, K. 1994. FDDI adapters: A sure cure for the bandwidth blues. Data Communications 23(10):60.
Tolly, K. 1994. How accurate is your LAN analyzer? Data Communications 23(2):42.
Tolly, K. 1994. The new branch-office routers. Data Communications 23(11):58.
Tolly, K. 1994. Testing dial up routers: Close, but no cigar. Data Communications 23(9):69.
Tolly, K. 1994. Testing remote ethernet bridges. Data Communications 23(8):81.
Tolly, K. 1994. Testing remote token ring bridges. Data Communications 23(6):93.
Tolly, K. 1994. Testing UNIX-to-SNA gateways. Data Communications 23(7):93.
Tolly, K. 1994. Wireless internetworking. Data Communications 22(17):60.
Further Information
Books:
The following two books are excellent additions to a professional library for overall coverage of data communications and networking.
Newton, H., Newton’s Telecom Dictionary, Telecom Library, New York.
Goldman, J. E., Applied Data Communications: A Business Oriented Approach, Wiley, New York.