7.2 OPERATING SYSTEMS
The operating system of a computer is a group of programs that manages or oversees all the operations of the computer. The computer transfers information constantly among peripherals such as a floppy disk, printer, keyboard, and video monitor. It also stores user programs under file names on a disk. (A file is defined as related records stored as a single entity.) The operating system is responsible primarily for managing the files on the disk and the communication between the computer and its peripherals. The functional relationship between the operating system and the computer’s various subsystems is shown in Figure 7.3.
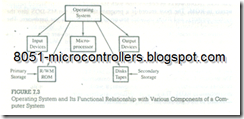
Each computer has its own operating system. Nowadays, the most widely used operating system for IBM PC-compatible microcomputers is MS-DOS. In the 1970s and early 1980s when most microcomputers were designed to use 8-bit microprocessors, the CP/M (Control Program/Monitor) operating system was commonly used. The MS-DOS and CP/M are in many ways similar to each other, except that the MS-DOS is designed to handle 16-bit (or 32-bit) microprocessors and 1 M byte memory, and the CP/M was designed for 8-bit microprocessors and 64K byte memory.
7.2.1 MS-DOS Operating System
In 16-bit microcomputers, such as IBM PC, XT, AT, and PS/2, the MS-DOS (Microsoft Disk Operating System) is so widely used that it has become the industry standard. Initially, when it was installed on IBM PC, it was known as PC-DOS; the terms MS-DOS and PC-DOS are interchangeable. The MS-DOS is designed to handle 16-bit data word and large-size one-megabyte system memory and disks with high memory capacity such as 720K and 1.44M. Similarly, it can support a hard disk and includes a hierarchical file directory. The latest version of MS-DOS is geared toward handling communication between multiuser systems.
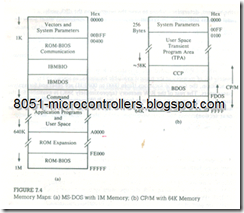
The MS-DOS operating system is divided into four components: Boot Record, IO.SYS, MSDOS.SYS, and COMMAND.COM. In the PC-DOS, these components are identified as ROM-BIOS, IBMBIO, lBM DOS, and COMMAND.COM, respectively. In a typical 1M (1.024K) system, the memory space is divided into 16 blocks from 0 to F, each being 64 K byte memory; the Hex address ranges from 00000 to FFFFFH. Generally, the lowest addresses in 0 block are reserved for system software, the highest block F is used for IO.SYS, and approximately ten blocks (640K) are reserved as the user memory. The remaining blocks are used for such various purposes as video display and BIOS extensions. See Figure 7.4(a).
BOOT RECORD AND ROM-BIOS
The boot record works in conjunction with the set of instructions stored permanently in ROM. The boot record is a program that loads the MS-DOS into the system memory, and ROM includes the program to initialize the hardware. The boot record is stored on track 0 and sector I of a formatted disk. When the system is turned on or reset, the program in ROM initializes the hardware parameters and reads first sector of track 0. Then the boot record loads IO.SYS and MSDOS.SYS into beginning locations of the system memory and passes the control to IO.SYS.
IO.SYS (IBMBIO.COM)
The primary function of this program is to communicate with I/O devices when it receives commands from a user’s program; it works in conjunction with a set of instructions in ROM. The program defines peripheral port addresses and enables additions of new peripherals; thus, it is device-dependent and -modified by hard-
ware manufacturers. The IO.SYS passes the control to MS-DOS after initializing the peripheral.
MS-DOS (IBMDOS)
This program directs the activities of the disk controller and also contains DOS service routines; these service routines include such programs as DIR (Directory), FORMAT (Formatting Disk), and COPY (Copying files). The program generates the tables in memory that are used by the COMMAND.COM program.
COMMAND. COM
This program reads and interprets the commands from the keyboard and differentiates between the DOS services (such as COPY) and the utility programs (such as DEBUG). This is an interface between the user and the MS-DOS.
Once the COMMAND. COM is executed, the booting process is completed, and the MS-DOS is ready to accept commands from the user. Figure 7.4(a) shows where the MS-DOS resides in the system memory and the memory space available for the user’s programs. The user writes programs in a transient portion of the memory, and when the Save command is given, the MS-DOS takes control of the system, determines where to save the program on the disk under a-file name, and regains control of the system.
7.2.2 CP/M Operating System
The CP/M operating system is designed to handle 8-bit data words and 64K bytes ‘system memory. It is divided into three components: BIOS (Basic Input/ Output System), BDOS (Basic Disk Operating System), and CCP (Console Command Processor).
When CP/M is loaded into a system’s R/W memory, it occupies approximately 6K of memory at the highest available locations, as shown in Figure 7.4(b). In addition, the first 256 locations (from 0000 to 00FFH) are reserved for system parameters. The rest of the R/W memory (approximately 58K) is available for the user. Once the operating system is loaded into R/W memory, the user can write, assemble, test, and debug programs y using utility programs (described in the next section).
7.2.3 Tools for Developing Assembly Language Programs
In addition to the operating system of a computer, various programs called utility programs are necessary to develop assembly language programs. These programs can be classified in two categories: (1) file-management utilities and (2) program development utilities. The file-management utilities are programs that enable the user to perform such functions as copying, printing, erasing, and renaming files. In MS-DOS, some programs such as COPY (Copy), DEL (Delete), and DIR (Directory) are part of the internal commands, meaning these programs are loaded into system memory along with the operating system. Other programs, such as PRINT (Print), FORMAT (Formatting Disk), and MODE (to set up printer options) are part of the external commands, meaning these programs are stored on the disk under file names and copied into system memory whenever they are needed. The program development utilities enable the user to write, assemble, and test assembly language programs; they include programs such as Editor, Assembler Linker (or Loader )Debugger, and cross-assemblers. The descriptions of various programs and the assembly process described below may vary in details depending upon an operating system, its utility programs, and an assembler being used.
EOITOR
The Editor is a program that allows the user to enter, modify, and store a group of instructions or text under a file name. The Editor programs can be classified in two groups: line editors and full-screen editors. Line editors, such as EDLIN (Edit Line) in MS-DOS, work with and manage one line at a time. On the other hand, full-screen editors (also known as word processors), such as PC-Write, ‘Word Star, and Word Perfect, manage the full screen or a paragraph at a time. To write text, the user must call the Editor under the control of the operating system. As soon as the Editor program is transferred from the disk to the system memory, the program control is transferred from the operating system to the Editor program. The Editor has its own commands, and the user can enter and modify text by using those commands. At the completion of writing a program, the exit command of the Editor program will save the program on the disk under the file name and will transfer the program control back to the operating system. This file is known as ‘a source file or a source program. If the source file is intended to be a program in the Z80 assembly language, the user should follow the syntax of the assembly language and the rules of the assembler that are described next.
The Editor program is not concerned with whether one is writing a letter or an assembly language program. The full-screen editors are convenient to write either line- or paragraph-oriented text; they automatically adjust lines as words are typed, and the text can be modified or erased with ease.
ASSEMBLER
The Assembler is a program that translates so’ .rce code or mnemonics into the binary code, called object code, of the microprocessor and generates a file called the Object file. This function is similar to manual assembly, whereby the user looks up the code for each mnemonic in the listing. In addition to translating mnemonics, the Assembler performs various functions, such as error checking and memory allocations. The Assembler is described in more detail in Section 7.3.
LINKER
The Linker (or Loader) is a program that takes the object file generated by the Assembler program and generates a file in binary code called the COM file or the EXE file. The COM (or EXE) file is the only executable file-i.e., the only file that can be executed by the microcomputer. To execute the program, the COM file is called under the control of the operating system and executed. In different assemblers or cross-assemblers, the COM file may be labeled by other names such as TSK file.
DEBUGGER
The Debugger is a program that allows the user to test and debug the object file. The user can employ this program to perform the following functions:
· Make changes in the object code.
· Examine and modify the contents of memory.
· Set breakpoints, execute a segment of the program, and display register con- ‘tents after the execution.
· Trace the execution of the specified segment of the program, and display the register and memory contents after the execution of each instruction .
· Disassemble a section of the program, i.e., convert the object code into the source code or mnemonics.
MS-DOS AND CROSS-ASSEMBLERS
The MS-DOS is an operating system designed primarily for 16-bit microprocessors. This raises a question: Why are we discussing the operating system meant for l6-bit processors in the context of 8-bit microprocessors such as the Z80? The answer lies with the widespread use of IBM PCs or their compatibles on college campuses. However, the microprocessor used in the IBM PC (Intel 8088 type family) has different mnemonics than that of the Z80; thus, we need a program that can translate the Z80 mnemonics but operate under the 16-bit microprocessor. Such a program is called a cross-assembler. The assembly process using a cross-assembler (described in Section 7.4) is similar to that of an assembler under a Z80 system. After assembling a program, the Hex file (discussed later) can be directly transferred to the R/W memory of a Z80 sin le-board microcomputer by using a download program. Thus, programs and/or hardware-related laboratory experiments can be easily performed.