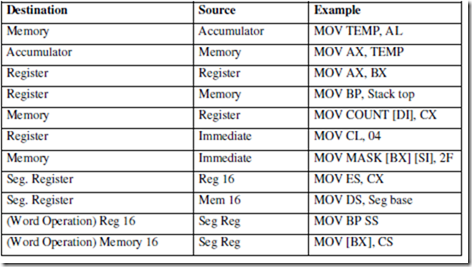
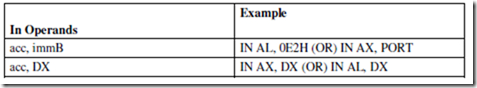
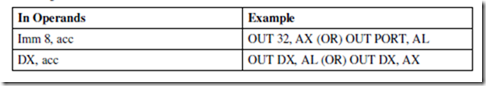
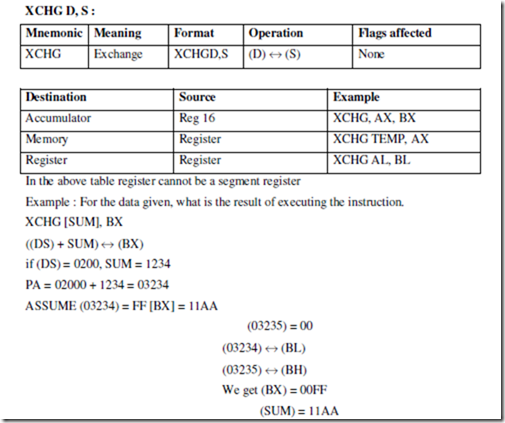
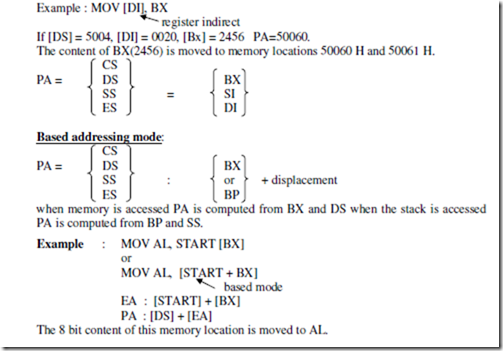
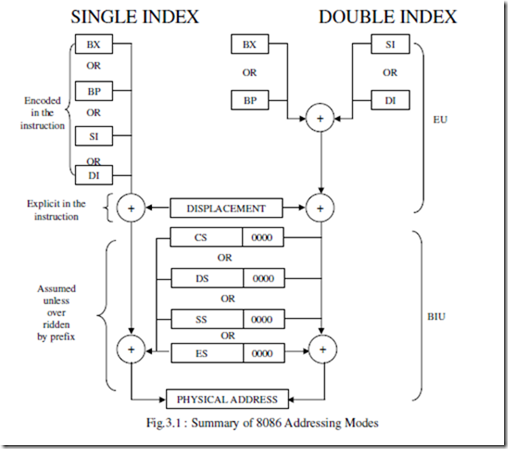
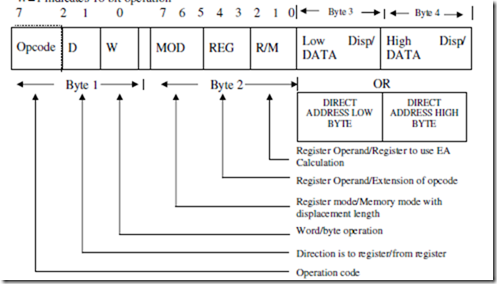
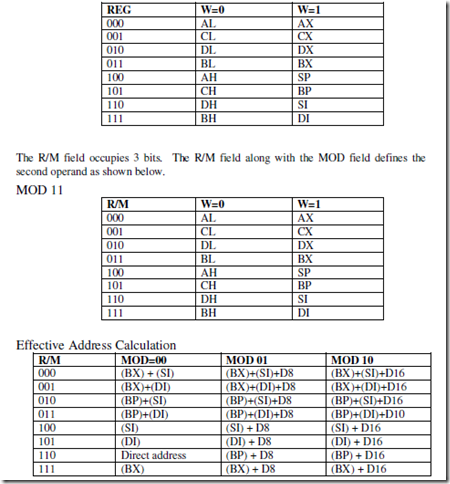
ASSUME CS: PROGRAM, DS: PROGRAM, SS: PROGRAM.
LABEL: Label The Label directive is used to assign a name to the current content of the location counter. At the start of the assembly process, the assembler initialises a location counter to keep rack of memory locations assigned to the program. As the program assembly proceeds, the contents of the location counter are updated. During the assembly process, whenever the assembler comes across the LABEL directive, it assigns the declared label with the current contents of the location counter. The type of the label must be specified, i.e. whether it is a NEAR or a FAR label, BYTE or WORD label, etc.
A LABEL directive may be used to make a FAR jump as shown below. A FAR jump cannot be made at a normal label with a colon. The label CONTINUE can be used for a FAR jump, if the program contains the following statement.
CONTINUE LABEL FAR
The LABEL directive can be used to refer to the data segment along with the data type, byte or word as shown.
DATA SEGMENT
DATAS DB 50H DUP (?)
DATA-LAST LABEL BYTE FAR
DATA ENDS
After reserving 50H locations for DATAS, the next location will be assigned a label DATALAST and its type will be byte and far.
LENGTH: Byte Length of a Label This directive is not available in MASM. This is used to refer to the length of a data array or a string.
MOV CX, LENGTH ARRAY
This statement, when assembled, will substitute the length of the array ARRAY in bytes, in the instruction.
LOCAL The lables, variables, constants or procedures declared LOCAL in a module are to be used only by that modul. At a later time, some other module may declare a particular data type LOCAL, which is previously declared LOCAL by an other module or modules. Thus the same label may serve different purposes for different modules of a program. With a single declaration statement, a number of variables can be declared local, as shown.
LOCAL a, b, DATA, ARRAY, ROUTINE
NAME: Logical Name of a Module The NAME directive is used to assign a name to an assembly language program module. The module, may now be referred to by its declared name. The names, if selected to be suggestive, may point out the functions of the different modules and hence may help in the documentation.
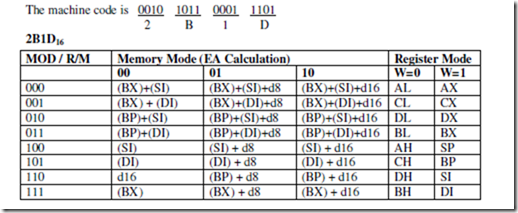
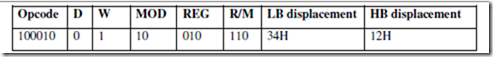
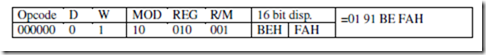
OFFSET: Offset of a Label When the assembler comes across the OFFSET operator along with a label, it first computes the 16-bit displacement (also called as offset interchangeably) of the particular label, and replaces the string ‘OFFSET LABEL’ by the computed displacement. This operator is used with arrays, strings, lables and procedures to decide their offsets in their default segments. The
segment may also be decided by another operator of similar type, viz, SEG. Its most common use is in the case of the indirect, indexed, based indexed or other addressing techniques of similar types, used to refer to the memory indirectly. The examples of this operator are as follows:
Example:
CODE SEGMENT
MOV SI, OFFSET LIST
CODE ENDS
DATA SEGMENT
LIST DB 10H
DATA ENDS
ORG: Origin The ORG directive directs the assembler to start the memory allotment for the particular segment, block or code from the declared address in the ORG statement While starting the assembly process for a module, the assembler initialises a location counter to keep track of the allotted addresses for the module. If the ORG statement is not written in the program, the location counter is initialised to 0000. If an ORG 200H statement is present at the starting of the code segment of that module, then the code will start from 200H address in code segment) In other words, the location counter will get initialised to the address 0200H instead of 0000H. Thus, the code for different modules and segments can be located in the available memory as required by the programmer. The ORG directive can even be used with data segments similarly.
PROC: Procedure The PROC directive marks the start of a named procedure in the statement. Also, the types NEAR or FAR specify the type of the procedure, i.e whether it is to be called by the main program located within 64K of physical memory or not. For example, the statement RESULT PROC NEAR marks the start of a routine RESULT, which is to be called by a program located in the same segment of memory. The FAR directive is used for the procedures to be called by the programs located in different segments of memory. The example statements are as follows:
Example
RESULT PROC NEAR
ROUTINE PROC FAR
PTR: Pointer The pointer operator is used to declare the type of a label, variable or memory operand. The operator PTR is prefixed by either BYTE or WORD. If the prefix is BYTE, then the particular label, variable or memory operand is treated as an 8-bit quantity, while if WORD is the prefix, then it is treated as a 16-bit quantity. In other words, the PTR operator is used to specify the data type – byte or word. The examples of the PTR operator are as follows:
Example:
MOV AL, BYTE PTR [SI] ;Moves content of memory location addressed by SI (8-bit) to AL
INC BYTE PTR [BX] ;Increments byte contents of memory location addressed by BX
MOV BX, WORD PTR [2000H] ; Moves 16-bit content of memory location 2000H to BX, i.e. [2000H] to BL [2001 H] to BH
INC WORD PTR [3000H] – Increments word contents of memory location 3000H considering contents of 3000H (lower byte) and 3001 H (higher byte) as a 16-bit number
In case of JMP instructions, the PTR operator is used to specify the type of the jump, i.e. near or far, as explained in the examples given below.
JMP WORD PTR [BX] -NEAR Jump
JMP WORD PTR [BX] -FAR Jump
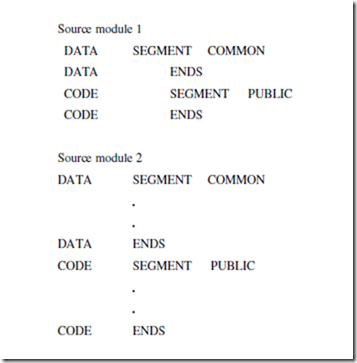
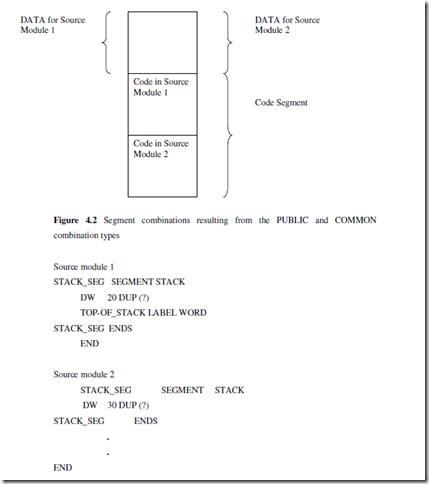
PUBLIC As already discussed, the PUBLIC directive is used along with the EXTRN directive. This informs the assembler that the labels, variables, constants, or procedures declared PUBLIC may be accessed by other assembly modules to form their codes, but while using the PUBLIC declared lables, variables, constants or procedures the user must declare them externals using the EXTRN directive. On the other hand, the data types declared EXTRN in a module of the program, may be declared PUBLIC in at least anyone of the other modules of the same program.
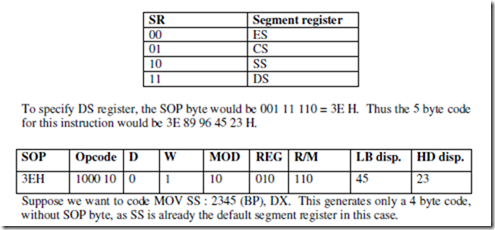
SEG: Segment of a Label The SEG operator is used to decide the segment address of the label, variable, or procedure and substitutes the segment base address in place of ‘SEG label’. The example given below explain the use of SEG operator.
Example
MOV AX, SEG ARRAY ; This statement moves the segment address
MOV DS, AX ;of ARRAY in which it is appearing, to register AX and then to DS.
SEGMENT: Logical Segment The SEGMENT directive marks the starting of a logical segment. The started segment is also assigned a name, i.e. label, by this statement. The SEGMENT and ENDS directive must bracket each logical segment of a program. In some cases, the segment may be assigned a type like PUBLIC
can be used by other modules of the program while linking) or GLOBAL (can be accessed by any other modules). The program structure given below explains
the use of the SEGMENT directive.
EXE . CODE SEGMENT GLOBAL ; Start of segment named
EXE.CODE, that can be accessed by any other module.
EXE . CODE ENDS; END of EXE.CODE logical segment.
SHORT The SHORT operator indicates to the assembler that only one byte is required to code the displacement for a jump (i.e. displacement is within -128 to +127 bytes from the address of the byte next to the jump opcode). This method of specifying the jump address saves the memory. Otherwise, the assembler may reserve two bytes for the displacement. The syntax of the statement is as given below.
JMP SHORT LABEL
TYPE The TYPE operator directs the assembler to decide the data type of the specified label and replaces the ‘TYPE label’ by the decided data type. For the word type variable, the data type is 2, for double word type, it is 4, and for byte type, it is 1. Suppose, the STRING is a word array. The instruction
MOV AX, TYPE STRING moves the value 0002H in AX.
GLOBAL The labels, variables, constants or procedures declared GLOBAL may be used by other modules of the program. Once a variable is declared GLOBAL, it can be used by any module in the program. The following statement declares the procedure ROUTINE as a global label.
ROUTINE PROC GLOBAL
Programming Examples:
ALP for addition of two 8-bit numbers
DATA SEGMENT
VAR1 DB 85H
VAR2 DB 32H
RES DB ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AL,VAR1
MOV BL,VAR2
ADD AL,BL
MOV RES,AL
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for Subtraction of two 8-bit numbers
DATA SEGMENT
VAR1 DB 53H
VAR2 DB 2AH
RES DB ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AL,VAR1
MOV BL,VAR2
SUB AL,BL
MOV RES,AL
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for Multiplication of two 8-bit numbers
DATA SEGMENT
VAR1 DB 0EDH
VAR2 DB 99H
RES DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AL,VAR1
MOV BL,VAR2
MUL BL
MOV RES,AX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for division of 16-bit number with 8-bit number
DATA SEGMENT
VAR1 DW 6827H
VAR2 DB 0FEH
QUO DB ?
REM DB ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,VAR1
DIV VAR2
MOV QUO,AL
MOV REM,AH
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for addition of two 16-bit numbers
DATA SEGMENT
VAR1 DW 8560H
VAR2 DW 3297H
RES DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,VAR1
CLC
MOV BX,0000H
ADD AX,VAR2
JNC K
INC BX
K: MOV RES,AX
MOV RES+2,BX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for Subtraction of two 16-bit numbers
DATA SEGMENT
VAR1 DW 8560H
VAR2 DW 3297H
RES DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,VAR1
CLC
SUB AX,VAR2
MOV RES,AX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for Multiplication of two 32-bit numbers
DATA SEGMENT
MULD DW 0FFFFH, 0FFFFH
MULR DW 0FFFFH, 0FFFFH
RES DW 6 DUP(0)
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,MULD
MUL MULR
MOV RES,AX
MOV RES+2,DX
MOV AX,MULD+2
MUL MULR
ADD RES+2,AX
ADC RES+4,DX
MOV AX,MULD
MUL MULR+2
ADD RES+2,AX
ADC RES+4,DX
JNC K
INC RES+6
K: MOV AX,MULD+2
MUL MULR+2
ADD RES+4,AX
ADC RES+6,DX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP to Sort a set of unsigned integer numbers in ascending/ descending
order using Bubble sort algorithm.
DATA SEGMENT
A DW 0005H, 0ABCDH, 5678H, 1234H, 0EFCDH, 45EFH
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV SI,0000H
MOV BX,A[SI]
DEC BX
X2: MOV CX,BX
MOV SI,02H
X1: MOV AX,A[SI]
INC SI
INC SI
CMP AX,A[SI]
JA X3
XCHG AX,A[SI]
MOV A[SI-2],AX
X3: LOOP X1
DEC BX
JNZ X2
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP to find the Greatest Common Deviser of two unsigned integer.
DATA SEGMENT
NUM1 DW 0017H
NUM2 DW 0007H
GCD DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,NUM1
MOV BX,NUM2
X1: CMP AX,BX
JE X4
JB X3
X2: MOV DX,0000H
DIV BX
CMP DX,0000H
JE X4
MOV AX,DX
JMP X1
X3: XCHG AX,BX
JMP X2
X4: MOV GCD ,BX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP to find the Sum and average of unsigned integer.
DATA SEGMENT
A DW 1234H,3223H,0FFFFH,4326H,0FEF3H,4325H
N DW 0006H
SUM DW 2 DUP(0)
AVG DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV SI,0000H
MOV DX,0000H
MOV CX,N
MOV AX,0000H
CLC
X: ADD AX,A[SI]
JC K
X1: INC SI
INC SI
LOOP X
JMP QUIT
K: ADD DX,0001H
JMP X1
QUIT: MOV SUM,AX
MOV SUM+2,DX
DIV N
MOV AVG,AX
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for conversion of 16-bit HEX number into its equivalent BCD number.
DATA SEGMENT
HEX DW 0FFFFH
BCD DW 5 DUP(0)
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV SI ,OFFSET BCD
MOV AX,HEX
MOV CX,2710H
CALL SUB1
MOV CX,03E8H
CALL SUB1
MOV CX,0064H
CALL SUB1
MOV CX,000AH
CALL SUB1
MOV [SI],AL
MOV AH,4CH
INT 21H
SUB1 PROC NEAR
MOV BH,0FFH
X1: INC BH
SUB AX,CX
JNC X1
ADD AX,CX
MOV [SI] ,BH
INC SI
RET
SUB1 ENDP
CODE ENDS
END START
ALP for conversion of 16-bit BCD number into its equivalent HEX number.
DATA SEGMENT
BCD DB 06H,05H,05H,03H,05H
HEX DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV CL,05H
MOV BP,000AH
MOV AX,2710H
PUSH AX
MOV DI,0000H
MOV SI, OFFSET BCD
X: MOV BL,[SI]
MUL BX
ADD DI,AX
POP AX
DIV BP
PUSH AX
INC SI
LOOP X
MOV HEX,DI
MOV AH,4CH
INT 21H
CODE ENDS
END START
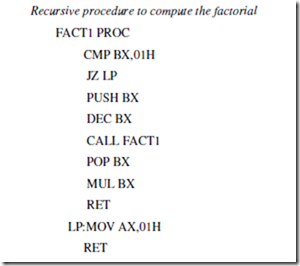
Develop and execute an ALP to compute factorial of a positive integer
number using recursive procedure.
DATA SEGMENT
NUM DW 0006H
FACT DW ?
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV AX,01H
MOV BX,NUM
CMP BX,0000H
JZ X1
CALL FACT1
X1: MOV FACT,AX
MOV FACT+2,DX
MOV AH,4CH
INT 21H
FACT1 PROC
CMP BX,01H
JZ X
PUSH BX
DEC BX
CALL FACT1
POP BX
MUL BX
RET
X: MOV AX,01H
RET
FACT1 ENDP
CODE ENDS
END START
ALP to copy the string of successive memory locations from one memory to
other
i. Using string instructions
DATA SEGMENT
SOURCE DB “BIOMEDICAL”
DATA ENDS
EXTRA SEGMENT
DEST DB ?
EXTRA ENDS
CODE SEGMENT
ASSUME CS:CODE , DS:DATA, ES:EXTRA
START : MOV AX,DATA
MOV DS,AX
MOV AX,EXTRA
MOV ES,AX
MOV SI,00H
MOV DI,00H
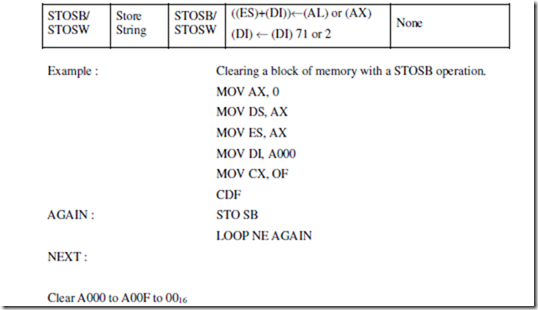
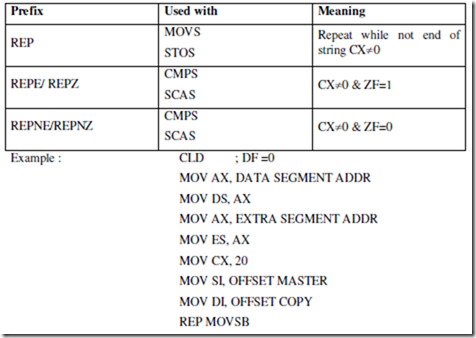
CLD
MOV CX,000AH
REP MOVSB
X: MOV AL,SOURCE [SI]
MOV DEST [DI],AL
INC SI
INC DI
LOOP X
MOV AH,4CH
INT 21H
CODE ENDS
END START
ii. Without using string instructions
DATA SEGMENT
SOURCE DB “BIOMEDICAL”
DATA ENDS
EXTRA SEGMENT
DEST DB ?
EXTRA ENDS
CODE SEGMENT
ASSUME CS:CODE ,DS:DATA,ES:EXTRA
START : MOV AX,DATA
MOV DS,AX
MOV AX,EXTRA
MOV ES,AX
MOV SI,00H
MOV DI,00H
MOV SI,OFFSET SOURCE
MOV DI,OFFSET DEST
MOV CX,000AH
X: MOV AL,SOURCE [SI]
MOV DEST [DI],AL
INC SI
INC DI
LOOP X
MOV AH,4CH
INT 21H
CODE ENDS
END START
ALP for conversion BCD number 7-Segment
DATA SEGMENT
TABLE DB 7EH, 30H, 60H, 79H, 33H, 5BH, 5FH,
70H,7FH, 73H
A DB 09H,01H,06H
B DB ?
DATA ENDS
CODE SEGMENT
ASSUME CS:CODE,DS:DATA
START: MOV AX,DATA
MOV DS,AX
MOV ES,AX
LEA BX,TABLE
LEA SI,A
LEA DI,B
MOV CX,03H
CLD
X1: LODS A
CMP AL,09H
JA X2
XLAT TABLE
STOS B
LOOP X1
X2: MOV AH,4CH
INT 21H
CODE ENDS
END START
Develop and execute ALP that implements Binary search algorithm. The data
consists of sorted 16 bit unsigned integers. The search key is also a 16 bit unsigned
integer.
DATA SEGMENT
ARR DW 05H,0111H,2161H,4541H,7161H,8231H
SR EQU 4541H
MSG1 DB ‘ELEMENT FOUND AT ‘
RES DB ‘ RD POSITION’,’$’
MSG2 DB ‘ELEMENT NOT FOUND’,’$’
DATA ENDS
ASSUME CS:CODE,DS:DATA
CODE SEGMENT
START: MOV AX,DATA
MOV DS,AX
MOV BX,00H
MOV CX,SR
MOV DX,05H
LP: CMP BX,DX
JA FAILURE
MOV AX,BX
ADD AX,DX
SHR AX,01
MOV SI,AX
ADD SI,SI
CMP CX,ARR[SI]
JAE BIGGER
DEC AX
MOV DX,AX
JMP LP
BIGGER: JE SUCCESS
INC AX
MOV BX,AX
JMP LP
SUCCESS:ADD AL,01H
ADD AL,2FH
MOV RES,AL
LEA DX,MSG1
JMP DISPLAY
FAILURE: LEA DX,MSG2
DISPLAY: MOV AH,09H
INT 21H
MOV AH,4CH
INT 21H
CODE ENDS
END START