EXAMPLE PROGRAMS
Now that many of the basic programming building blocks have been discussed, we present some example application programs. Although these example programs may seem trivial, they show some additional programming techniques and illustrate programming styles for the microprocessor.
Time/Date Display Program
Although this program does not use assembly language, it does demonstrate how to obtain the date and time from the Windows API and how to format it for display. It also illustrates how to use a timer in Visual C++. Example 8–40 illustrates a program that uses a timer, set to interrupt the program once per second, to display the time and date. The time and date are obtained by using DateTime object to read the computer time and date into a variable called dt. The format member TimeDate is used to format the dt variable. Create a dialog application called DateTime and place two labels on it as shown in Figure 8–13.
Numeric Sort Program
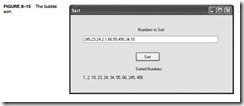
At times, numbers must be sorted into numeric order. This is often accomplished with a bubble sort. Figure 8–14 shows five numbers that are sorted with a bubble sort. Notice that the set of five numbers is tested four times with four passes. For each pass, two consecutive numbers are com- pared and sometimes exchanged. Also notice that during the first pass there are four comparisons, during the second three, and so forth.
Example 8–41 illustrates a program that accepts 10 numbers from the keyboard (32-bit integers). After these 32-bit numbers are accepted and stored in memory section numbers, they are sorted by using the bubble-sorting technique. This bubble sort uses a swap flag to determine whether any numbers were exchanged in a pass. If no numbers were exchanged, the numbers are in order and the sort terminates. This early termination normally increases the efficiency of the sort because numbers are rarely completely out of order.
Once the numbers are sorted, they are displayed in ascending order. Figure 8–15 shows how the application appears after it is executed.
Data Encryption
Data encryption seems to be the vogue at this time because of the security aspect of many systems. To illustrate simple data encryption for a character string, suppose that each character in a string is exclusive-ORed with a number called an encryption key. This certainly changes the code of the character, but to make it a bit more random, suppose that the encryption key is changed after each character is encrypted. In this way patterns are much harder to detect in the encrypted message, making it harder to decipher.
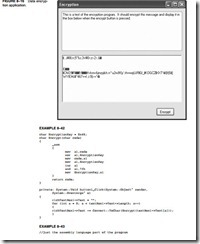
To illustrate this simple scheme, Figure 8–16 shows a screen shot of the program to test the scheme, using a textbox control to accept a character string and a label to display the encrypted message. This example was generated using an initial encryption key of 0×45. If the initial value is changed, the encrypted message will change.
Example 8–42 lists the program used to generate the message in its encrypted form in a rich textbox control. The button event handler reads the contents of the textbox control, used for entering the character string to be encrypted, and uses a short assembly language function to encrypt the string. Notice how the program uses assembly language to Exclusive-OR each character of the string with the EncryptionKey and then how the EncryptionKey is modified for the next character. The technique used here increments the Encryption key and prevents the key from becoming larger than 7FH. This technique can be made more intricate to make it even more difficult to decipher. For example, suppose that the key is incremented on every other character and that is alternated with inverting the key, as shown in Example 8–43. Almost any combination of operations can be used to modify the key between passes to make it very difficult to decode. In practice we use a 128-bit key and the technique for modification is different, but nonetheless, this is basically how encryption is performed. Because Example 8–40 uses an 8-bit key, the encrypted message could be cracked by trying all 256 (28) possible keys, but if a 128-bit key is used, it requires far many more attempts (2128) to crack—an almost impossible number of attempts.