9.3 Network Architecture: Local Area Networks
A local area network (LAN) is a communication medium that interconnects computers over a limited geographical distance of a few kilometers at most. A LAN allows a set of closely grouped computers and other devices to share common resources such as data, software applications, printers, and mass storage.
A LAN consists of hardware, software, and protocols. The hardware may be in the form of cables and interface circuitry. The software is typically embedded in an operating system, and is responsible for connecting a user to the network. The protocols are sets of rules that govern format, timing, sequencing, and error control. Protocols are important for ensuring that data is packaged for injection into the network and is extracted from the network properly. The data to be transmit- ted is decomposed into pieces, each of which is prepended with a header that contains information about parameters such as the destination, the source, error protection bits, and a time stamp. The data, which is often referred to as the pay- load, is combined with the header to form a packet that is injected into the net- work. A receiver goes through the reverse process of extracting the data from the packet.
The process of communicating over a network is normally carried out in a hier- archy of steps, each of which has its own protocol. The steps must be followed in sequence for transmission, and in the reverse sequence when receiving. This leads to the notion of a protocol stack which isolates the protocol being used within the hierarchy.
9.3.1 THE OSI MODEL
The Open System Interconnection (OSI) model is a set of protocols established by the International Standards Organization (ISO) in an attempt to define and standardize data communications. The OSI model has been somewhat displaced by the Internet TCP/IP model (see Section 9.5) but still heavily influences net- work communication, particularly for the telecommunication industry.
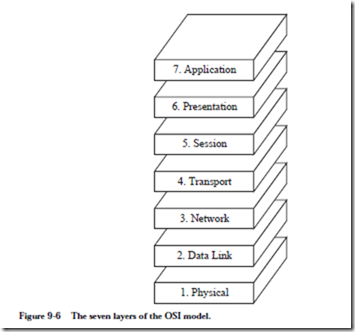
In the OSI model the communication process is divided into seven layers: appli- cation, presentation, session, transport, network, data link, and physical as summarized in Figure 9-6. As an aid in remembering the layers, the mnemonic is sometimes used: A Powered-down System Transmits No Data Packets.
The OSI model does not give a single definition of how data communications actually take place. Instead, the OSI model serves as a reference for how the process should be divided and what protocols should be used at each layer. The concept is that equipment providers can select a protocol for each layer while ensuring compatibility with equipment from other providers that may use different protocols.
The highest level in the OSI model is the application layer, which provides an interface for allowing applications to communicate with each other over the net- work. It offers high level support for applications that interact over the network such as database services for network database programs, message handling for electronic mail (e-mail) programs, and file handling for file transfer programs.
The presentation layer ensures that information is presented to communication applications in a common format. This is necessary because different systems may use different internal data formats. For instance, some systems use a
big-endian internal format while others use a little-endian internal format. The function of the presentation layer is to insulate the applications from these differences.
The session layer establishes and terminates communication sessions between host processes. The session layer is responsible for maintaining the integrity of communication even if the layers below it lose data. It also synchronizes the exchange, and establishes reference points for continuing an interrupted communication.
The transport layer ensures reliable transmission from source to destination. It allocates communication resources so that data is transferred both quickly and cost effectively. The session layer makes requests to the transport layer, which prioritizes the requests and makes trade-offs among speed, cost, and capacity. For example, a transmission may be split into several packets which are transmitted over a number of networks in order to obtain a faster communication time. Packets may thus arrive at the destination out of order, and it is the responsibility of the transport layer to ensure that the session layer receives data in the same order it is sent. The transport layer provides error recovery from source to destination, and also provides flow control (that is, it ensures that the speeds of the sender and receiver are matched).
The network layer routes data through intermediate systems and subnetworks. Unlike the upper layers, the network layer is aware of the network topology, which is the connectivity among the network components. The network layer informs the transport layer of the status of potential and existing connections in the network in terms of speed, reliability, and availability. The network layer is typically implemented with routers, which connect different networks that use the same transport protocol.
The data link layer manages the direct connections between components on a network. This layer is divided into the logical link control (LLC) which is independent of the network topology, and the media access control (MAC) which is specific to the topology. In some networks the physical connections between devices are not permanent, and it is the responsibility of the data link layer to inform the physical layer when to make connections. This layer deals in units of frames (single packets, or collections of packets that may be interleaved), which contain addresses, data, and control information.
The physical layer ensures that raw data is transmitted from a source to a destination over the physical medium. It transmits and repeats signals across network boundaries. The physical layer does not include the hardware itself, but includes methods of accessing the hardware.
9.3.2 TOPOLOGIES
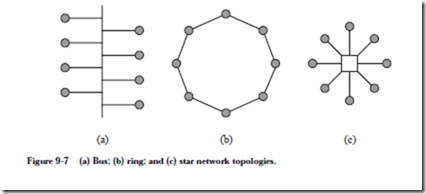
There are three primary LAN organizations, as illustrated in Figure 9-7. The bus
topology is the simplest of the three. Components are connected to a bus system by simply plugging them into the single cable that runs through the network, or in the case of a wireless network, by simply emitting signals into a common medium. An advantage to this type of topology is that each component can communicate directly with any other component on the bus, and that it is relatively simple to add another component to the network. Control is distributed among the components, and so there is no single network component that serves as an intermediary, which reduces the initial cost of this type of network. Disadvantages of this topology include a limit on the length of the cable from the bus to each network component (for a wireline network) and that a break in the cable may be needed in order to add another component to the network, which disrupts the rest of the network. An example of a bus-based network is Ethernet.
The ring topology uses a single cable, in which the ends are joined. Packets are passed around the ring through each network component until they reach their destinations. At the destinations, the packets are extracted from the network and are not passed farther along the ring. If a packet makes its way back to the originating system, then the transmission is unsuccessful, and so the packet is stopped and a new transmission can be attempted. An example of a ring-based LAN is IBM’s Token Ring.
In a star topology, each component is connected to a central hub which serves as an intermediary for all communication over the network. In a simple configuration, the hub receives data from one component and forwards it to all of the other components, leaving it to the individual components to determine whether or not they are the intended target. In a more sophisticated configuration, the hub receives data and forwards it to a specific network component.
An advantage of a star topology is that most of the network service, troubleshooting, and wiring changes take place at the central hub. A disadvantage is that a problem with the hub affects the entire network. Another disadvantage is that geometrically, the star topology requires more cable than a bus or a ring because a separate cable connects each network component to the hub. An example of a star topology is ARCnet (although it is actually a bus-based network).
9.3.3 DATA TRANSMISSION
Communication within a computer is synchronized by a common clock, and so the transmission of a 1 or a 0 is signalled by a high or low voltage that is sampled at a time determined by the clock. This scheme is simple, but does not work well over longer distances, as in a LAN. The problem is that there is no timing reference to signal the start or stop of a bit. When there is a long string of 1’s or 0’s, timing with respect to the sending and receiving clocks may drift because the clocks are not precisely synchronized. The distances over a LAN are too great to maintain both a global clock and high speed at the same time. LANs thus typically use the Manchester encoding scheme (see Section 8.5), in which timing is embedded in the data.
Manchester encoding is applied at the lowest level of transmission. At the next level, a data stream is decomposed into packets and frames that are transmitted over the network, not necessarily in order. The data link layer is responsible for decomposing a data stream into packets, forming packets into frames, and injecting frames into the network. When receiving frames, the data link layer extracts the packets and assembles them into a format that the higher level network layers can use. The size of a data packet is commonly on the order of a kilobyte, and requires a few microseconds for transmission at typical speeds and distances.
Ethernet is one of the most prevalent bus-based networks. Ethernet uses carrier sense multiple access with collision detection (CSMA/CD) for transmission. Under CSMA/CD, when a network component wants to transmit data, it first listens for a carrier. If there is a carrier present on the line, which is placed there by a transmitting device, then it transmits nothing and listens again after a random waiting period. The random waiting period is important in order to avoid a deadlock in which components that are trying to access the bus perpetually lis- ten and wait in synchrony.
If there is no traffic on the line, then transmission can begin by placing a carrier on the line with the data. The source also listens for collisions, in which two or more components simultaneously transmit. A collision is detected by the presence of more than one carrier. Collisions can occur in a fully operational network as a result of the finite time it takes for a signal to travel the length of the bus. The propagation of signals on the bus is bounded by the speed of light over the length of the bus, which can be 500 m in a generic Ethernet installation. When a collision occurs, the transmitting components wait for a random interval before retransmitting.
Transmitted data moves in both directions over the bus. Every component sees every packet of data, but only extracts those packets with corresponding destination addresses. After a packet is successfully delivered, the destination can generate an acknowledgment to the sender, typically at the transport layer. If the
sender does not receive an acknowledgment after a fixed period of time (which must be greater than the round trip delay through the network), then it retransmits the message.
Collisions should occur infrequently in practice, and so the overhead of recovering from a collision is not very significant. A serious degradation in Ethernet performance does not occur until traffic increases to about 35% of network capacity.
9.3.4 BRIDGES, ROUTERS, AND GATEWAYS
As networks grow in size, they can be subdivided into smaller networks that are interconnected. The smaller subnetworks operate almost entirely independently of each other, and can use different protocols and topologies.
If the subnetworks all use the same topology and the same protocols, then it may be the case that all that is needed to extend the network are repeaters. A repeater amplifies the signals on the network, which become attenuated in proportion to the distance traveled. The overall network is divided into subnetworks, in which each subnetwork operates somewhat independently with respect to the others. The subnetworks are not entirely independent because every subnetwork sees all of the traffic that occurs on the other subnetworks. A network with simple repeaters is not extensible to large sizes. Since noise is amplified as well as the signal, the noise will eventually dominate the signal if too many repeaters are used in succession.
A bridge (different from a bus bridge, introduced in Chapter 10) does more than simply amplify signal levels. A bridge restores the individual signal levels to logical 1 or 0, which prevents noise from accumulating. Bridges have some level of intelligence, and can typically interpret the destination address of a packet and route it to the appropriate subnetwork. In this way, network traffic can be reduced, since the alternative method would be to blindly send each incoming packet to each subnetwork (as for a repeater based network).
Although bridges have some level of intelligence in that they sense the incoming bits and make routing decisions based on destination addresses, they are unaware of protocols. A router operates at a higher level, in the network layer. Routers typically connect logically separate networks that use the same transport proto- col.
A gateway translates packets up through the application layer of the OSI model (layers 4 through 7). Gateways connect dissimilar networks by performing proto- col conversions, message format conversions, and other high level functions.