BRIDGES, GATEWAYS AND REPEATERS
11.3.1 Network bridges
A network bridge is an electronic hardware device for carrying out bidirectional data transmission across a plurality of networks connected via ports. The network bridge is particularly suited to connecting two networks that have the same communication protocol, so allowing the bridge to segment a network. Secondly, a network bridge commonly has two connections between two distinct networks.
Thirdly, the bridge works at the layer 2, data-link layer, in the OSI reference model. Formally both in LAN and Ethernet networks, the term “bridge” means a device that behaves according to the IEEE 802.1D standard, although it is commonly referred to as a network switch in marketing language.
(1) Network bridging algorithms
Bridging is a forwarding technique used in packet-switched computer networks. Unlike routing, the bridging makes no assumptions about where in a network a particular address is located, but depends on broadcasting to locate unknown devices. In routing, once a device has been located, its location is recorded in a routing table to preclude the need for further broadcasting. Bridging depends on broadcasting, and is thus only used in local area networks.
Two different bridging technologies, transparent bridging and source routing, are in widespread use. Transparent bridging predominates in Ethernet networks, whereas source routing is used in token ring networks. Thus, bridging allows two networks to connect seamlessly on the data-link layer in the OSI model. In this respect, network bridges are like network switches.
(a) Transparent bridging
Also known as adaptive bridging, this refers to a form of bridging that is “transparent” to the end systems. The end systems operate as if the bridge does not exist, which leaves the bridge to segment broadcasts between networks, and only allow specific addresses to pass to the other network.
This bridging algorithm has been standardized as IEEE 802.1D. The bridging functions are confined to network bridges which interconnect network segments. The active parts of the network must form a tree, which can be achieved either by physically building the network as a tree, or by using bridges that use the spanning tree protocol. This is briefly discussed below.
The algorithm uses a forwarding database to send frames across network segments. This is initially empty, and entries in the database are built once the bridge receives frames. If an address entry is not found in the forwarding database, the frame is rebroadcast to all ports of the bridge, to all segments except for the source address. By broadcasting these frames, the destination network will respond and a route will be created. Along with recording the network segment to which a particular frame is to be sent, bridges may also record a bandwidth metric to avoid looping when multiple paths are available. Note that both source and destination addresses are used in this algorithm. Source addresses are recorded in entries in the table, while destination addresses are looked up in the broadcasting table and matched to the proper destination segment.
As an example, consider two host computers, A and B, and a network bridge C. The bridge has two ports or interfaces, C1 and C2. The host computer A is connected to C1; and the host computer B is connected to C2. The physical connection is from A to C and then to B, since the bridge C has two ports. The host computer A sends a frame to the bridge C, which records the source MAC address in its broadcasting table. The bridge C now has an address for the host computer A in its table, so it forwards it to the host B by broadcasting it to the MAC address (say FF:FF:FF:FF:FF:FF) or every address possible. It assumes that host B, having received a packet from A, now transmits a packet in response. This time, the bridge has A’s address in the table, so it records B’s address and sends it to A’s unique MAC address specifically. Two-way communication is now possible between A and B without any further broadcasting. Note, however, that only the bridge along the direct path between A and B possesses table entries for B. If a third host computer, D, on the same side as A sends a frame to B, the bridge simply records the address source, and broadcasts it to B’s segment.
(b) Source route bridging
This is based on Section 9 of the IEEE 802.2 standard, which does not need the structure of the spanning tree protocol. The operation of the network bridges is simpler, and much of the bridging functions are performed by the end systems, particularly the sources, giving rise to its name.
A field in the token ring header, the routing information field (RIF), is used to support source-route bridging. Upon sending a packet, a host computer attaches a RIF to the packet indicating the series of bridges and network segments to be used for delivering the packet to its destination. The bridges merely follow the list given in the RIF; if a given bridge is next in the list, it forwards the packet, and otherwise it ignores it. When a host wishes to send a packet to a destination for the first time, it needs to determine an appropriate RIF. A special type of broadcast packet is used, which instructs the network bridges to append their bridge number and network segment number to each packet as it is forwarded. Loops are avoided by requiring each bridge to ignore packets which already contain its bridge number in the RIF’s field. At the destination, these broadcast packets are modified to be standard unicast packets and returned to the source along the reverse path listed in the RIF. Thus, for each route discovery packet broadcast, the source receives back a set of packets, one for each possible path through the network to the destination. It is then up to the source to choose one of these paths (probably the shortest one) for further communications with the destination.
As mentioned above, in the transparent bridging algorithm, a network bridge uses the IEEE spanning tree protocol to establish a loop-free forwarding topology. When there are multiple paths in a bridged network, loops can form, and the simple forwarding rules of a bridge can cause forwarding storms: a condition in which the same frame is relayed endlessly from one network segment, across the bridge, to another segment. The spanning tree protocol is an algorithm that provides an automated mechanism to selectively disable bridge forwarding on individual ports as is necessary, in order to ensure that the network topology is loop-free. No configuring of the network bridge is needed to use it.
The main idea of the spanning tree protocol is for the bridges to select the ports over which they will forward frames. Selection proceeds as follows: each bridge has a unique number as its identifier in a given LAN. The algorithm first elects the bridge with the “smallest identifier” as “the root bridge” of the tree in the given LAN. The root bridge always forwards frames out over all its ports. Next, each bridge computes “the shortest path” to the root and notes which of its ports is on this path. This port is also selected as the bridge’s “preferred path” to the root. Finally, all the bridges connected to the given LAN elect a single “designated bridge” that will be responsible for forwarding frames towards the root. Each designated bridge in the LAN is the one that is closest to the root; if two are equally close to the root, then their identifiers are used to break ties, with the smallest being chosen. Of course, each bridge is connected to more than one LAN, so it participates in the election of a designated bridge for each LAN it is connected to. In effect, this means that each bridge decides whether it is the designated bridge relative to each of its ports. The bridge forwards frames over those ports in the designated bridge.
(2) Network bridge applications
Network bridges connect one network to another so that terminals on both of them can communicate as if they were part of a single network. They provide the connectivity required for communications between dissimilar segments of a given LAN. Normally, network bridges send packets between two networks of the same type; receiving packets from a segment connected to one port and forwarding
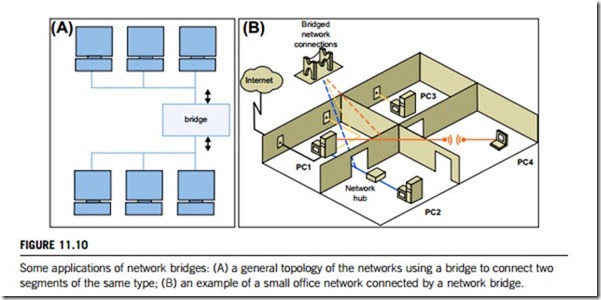
them to another. If a LAN bridge is used to extend the network range, it also relieves the problem of congestion that multiple devices can cause on a single Ethernet segment. Figure 11.10(A) shows this function of network bridges.
The bridge is used to segment a network, holding back the frames intended for the LAN while transmitting those meant for other networks. This reduces traffic (and especially collisions) on all networks, and increases the level of privacy, because information intended for one network cannot be received on another.
Figure 11.10(B) supposes a small office network with four computers (PC1, PC2, PC3, and PC4) and one Ethernet hub. The four computers are running Windows XP; Windows Server 2003, Standard Edition; or Windows Server 2003, Enterprise Edition; and have the following hardware installed:
(a) PC1 has an adapter connecting it to the Internet, an Ethernet network adapter, an HPNA (Home Phone Network Alliance) network adapter, and a wireless adapter;
(b) PC2 has an Ethernet network adapter;
(c) PC3 has an HPNA network adapter;
(d) PC4 has a wireless network adapter.
The Ethernet adapters on PC1 and PC2 are connected to a common Ethernet hub to form the first LAN segment. PC1 is connected to PC3 with the HPNA adapter to form a second LAN segment, and PC1 is connected to PC4 with the wireless adapter to form a third LAN segment. The bridge can be used to connect the Ethernet network adapter, the HPNA network adapter, and the wireless network adapter on PC1, to forward traffic from one LAN segment to another and enable all of the computers to communicate with each other.
Without a network bridge (or additional routing configurations or bridging hardware), only PC1 can communicate with each of the other computers because it is the only computer that has connections to all three LAN segments. Because PC2, PC3, and PC4 use different types of network media, they are on different LAN segments, and they can only communicate with PC1.