Chapter 7. BIOS
Think of the Basic Input/Output System of your computer as its crazy Aunt Maud, locked away from public eyes in a cobwebby garret. Except for the occasional deranged laughter that rings through the halls, you might never know she was there, and you don’t think about her again until the next reel of the B-movie that makes up your life.
As with your own old Aunt Maud, your computer’s BIOS is something that you want to forget but is always there, lingering in the background, popping into sight only at the least convenient times. Despite its idiosyncrasies and age, despite the embarrassment it causes, the BIOS is something your computer can’t live without. It defines what your computer is and keeps it in line, just as Aunt Maud defines what your family really is and her antics keep you in line (or at least tangled up in obscure legal proceedings). You’d really like to be rid of Aunt Maud, but only she knows the secret of your family’s jewels, a secret someday you hope you’ll wrest from her.
The BIOS of your computer lingers around like that unwelcome relative, but it also holds the secrets of your computer. You can lock it up, even build a wall around it, but it will always be there. When you switch on your computer, it laughs at you from the monitor screen, appearing in the rags and tatters of text mode before your system jumps off into modern high-resolution color. Most of what you do on your computer now sidesteps the BIOS, so you’d think you could do without it. You might never suspect that behind the scenes the BIOS of your computer tests your system, assures you that everything is okay when you start your system, helps you set up your computer so that it runs at its best, and gracefully steps out of the way when you no longer need it.
Although modern operating systems such as Windows do their best to hide the BIOS and take its place, it always lurks in the background like crazy old Aunt Maud locked in the garret. Just as Aunt Maud may ruin a dinner party when she suddenly pops up babbling about a talking moose, your BIOS bursts onto the scene when you least expect it and ruins your fun (for example, hiding half of your new hard disk).
However, your Aunt Maud might just not be as crazy as she seems, watching over you quietly from her garret, hiding in the background but working in her own mysterious ways to make sure your life goes well.
Background
Although mostly invisible and oft forgotten, your computer’s BIOS is nevertheless one of its most important and enabling parts. The BIOS is, in fact, the one essential constituent that distinguishes one computer from another, even when they both share the same microprocessor, motherboard, and support hardware.
Firmware
Strictly speaking, however, the BIOS isn’t hardware at all, even though it is an essential part of your computer’s hardware. The BIOS is special program code—in a word, software—that’s permanently (or nearly so) encapsulated in ROM chips or, as is most often the case with newer computers, Flash memory. Because of the two-sided aspects of the BIOS, existing in the netherworld between hardware and software, it and other pieces of program code encapsulated in ROM or Flash memory are often termed firmware.
The importance of the BIOS arises from its function. The BIOS tests your computer every time you turn it on. It may even allocate your system’s resources for you automatically, making all the adjustments necessary to accommodate new hardware. The BIOS also determines the compatibility of your computer with both hardware and software and can even determine how flexible your computer is in setup and use.
Firmware can do more. If some enterprising computer-maker wanted to, it could put the entire operating system and application software into firmware. Some portable computers actually came close—early Hewlett-Packard Omnibook sub-notebook computers packed Windows and part of Microsoft Office into their ROMs. Of course, these machines are not very useful any more. The Windows inside is version 3.0, which points out the disadvantage of putting too much into firmware—updates are cumbersome and the code-storage requirements of today’s software would fill more chips than you could comfortably carry. The storage available in a computer’s ROM gives engineers kilobytes to work with, not the gigabytes today’s systems demand for storage of their software.
Today, firmware plays only a subsidiary role in most computers. All modern operating systems enhance the basic BIOS firmware with additional instructions loaded from disk like ordinary software—typically such enhancements totally replace the BIOS firmware. This new code supplied by the operating system performs some of the same functions as the traditional BIOS firmware, linking your computer’s hardware to the software programs that you run. But every computer still requires at least a vestigial piece of BIOS firmware, if just to enable enough of your system to run so that it can load the operating system. Although the BIOS plays a less active role in every operation of your computer, it is essential to getting your computer going, and it remains an essential part of every new computer and future machines still waiting on the engineer’s drawing board.
Functions
The BIOS code of most computers has a number of separate and distinct functions. The BIOS of a typical computer has routines that test the computer, blocks of data that give the machine its personality, special program routines that allow software to take control of the computer’s hardware so that it can more smoothly mesh with the electronics of the system, and even a complete system (in some computers) for determining which expansion boards and peripherals you have installed and ensuring that they do not conflict in their requests for input/output ports and memory assignments. Although all these functions get stored in the same memory chips, the program code of each function is essentially independent of the rest. Each function is a separate module, and the name BIOS refers to the entire group of modules.
This list of functions is not an exhaustive list of what a BIOS could do. It represents only what the makers of current computers use the BIOS for. In fact, there’s little limit on what BIOS code can do. Apple has long (since 1984) put most of the graphics of its Macintosh systems in its BIOS, and IBM for years encapsulated a small programming language in the BIOSs of its first computers.
The classic definition of the computer BIOS is the firmware that gives the computer its personality. This definition refers only to one functional module of the computer—the one that’s invariably replaced by operating system code. The nebulous term personality described how the computer performed its basic functions, those necessary to make it a real computer. Although this definition included a number of different factors, including how quickly and smoothly various operations were completed, the term personality mostly distinguished computers from Apple Macintoshes.
Most of the personality of the computer has moved from its BIOS to the operating system, loaded entirely from disk storage into RAM. The BIOS now plays a subsidiary role. Chiefly it is in charge of getting your computer going and running things until your hard disk can disgorge the hundreds of megabytes of operating system code and software can take over control of your computer.
In most computers, the first thing the BIOS tells the microprocessor to do is to run through all the known components of the system—the microprocessor, memory, keyboard, and so on—and to test to determine whether they are operating properly. After the system is sure of its own integrity, it checks to see whether you have installed any expansion boards that hold additional BIOS code. If you have, the microprocessor checks the code and carries out any instructions it finds. A modern computer may even check to see whether any new expansion boards are plugged in without being set up properly. The BIOS code might then configure the expansion board so that it functions properly in your computer.
When the microprocessor runs out of add-in peripherals, it begins the actual bootup process, which engineers call the Initial Program Load (IPL). The BIOS code tells the microprocessor to jump to a section of code that tells the chip how to read the first sector of your floppy or hard disk. Program code then takes over from the BIOS and tells the microprocessor how to load the operating system from the disk to start the computer running.
Exactly what the BIOS does after the operating system loads depends on the operating system. The first computer operating system, DOS, worked in conjunction with the BIOS. DOS relied on the BIOS firmware, which includes several sets of routines that programs can call to carry out everyday functions, such as typing characters on the screen or to a printer, reading keystrokes, and timing events. Because of this basic library, programmers writing for DOS could create their grand designs without worrying about the tiny details.
With Windows, however, the BIOS gets pushed out of the way. After the BIOS has assured the operating integrity of your system, Windows takes over. First, the operating system starts loading its own boot code. Then, it installs drivers that take over the various interface functions of the BIOS, one by one.
The operating system replaces the BIOS interface routines for several reasons. Because software drivers load into RAM, they are not limited in the amount of space available for their code. Software drivers also extend the capabilities, whereas the BIOS limits them. Using only the BIOS, your computer cannot do anything that the BIOS does not know about. It enables you to use the wide variety of peripherals you’re apt to connect to your computer. Moreover, because the BIOS is designed to run at bootup when your computer is in real mode, it uses only real-mode code, with all the limitations that implies (in particular, a total address space of 1MB). Software drivers can (and nowadays invariably do) run in protected mode. Not only can they access more memory, but protected mode drivers can be written in 32-bit code that executes faster on modern microprocessors.
Initialization Functions
The BIOS starts to work as soon as you switch your system on. When all modern Intel microprocessors start to work, they immediately set themselves up in real mode and look at a special memory location that is exactly 16 bytes short of the top of the 1MB real-mode addressing range—absolute address 0FFFF0(hex). This location holds a special program instruction, a jump that points to another address where the BIOS code actually begins.
The term cold boot describes the process of starting your computer and loading its operating system by turning the power on. If your computer is running, you cold boot by first switching it off and then back on.
Warm boot describes the process of restarting your computer and loading its operating system anew after it has already been running and has booted up at least once before. You start a warm boot by giving the infamous “three-finger salute” by pressing the Ctrl, Alt, and Delete keys at the same time.
Finally, hot boot describes what you get when you slide a piece of footwear into your oven in a mistaken attempt at the preparation of filet of sole. The term is not used to describe the computer bootup process.
At the operating system level, a cold boot and a warm boot are essentially the same. Your computer starts from the beginning and loads the operating system from scratch. A warm boot or switching your computer off for a cold boot signals the microprocessor to reset itself to its “turn-on” condition, erasing the contents of its registers. The microprocessor then loads or reloads the operating system.
The important difference between a cold and warm boot is not what happens to your operating system but the effect on your computer’s internal circuits. A cold boot automatically restores all the circuits in your computer to their original, default condition, whether they are on the motherboard or the expansion boards, because it cuts off their electrical supply. It also wipes away everything in its memory for a fresh start. A warm boot does not affect the supply of electricity to your computer’s circuitry, so memory and the boards installed in your computer are not wiped clean, although some of the contents get overwritten as your operating system reloads.
Because a warm boot does not automatically restore all the expansion boards in your computer to their initial conditions, it sometimes does not solve software problems. For example, your modem may not release the telephone line (hang up) at the end of your Internet session. A warm boot may leave the modem connected, but a cold boot will ensure the modem disconnects and releases your telephone line.
Unless the boards in your computer follow the Plug-and-Play standard that specifies a standard reset condition, your computer has no way of telling the state of each board in your computer after a warm boot. It makes no attempt to find out and just takes what it gets. Ordinarily such blind acceptance is not a problem. If, however, some odd state of an expansion board caused your computer to crash, a warm boot will not solve the problem. For example, sometimes video boards will come up in odd states with strange screen displays after a crash that’s followed by a warm boot. Cold-booting your computer again usually eliminates such problems.
Your computer also behaves differently during the cold- and warm-booting processes. During a cold boot, your computer runs through its Power-On Self Test (POST) procedure to test all its circuitry. During a warm boot, your computer sidesteps POST under the assumption that it has already booted up once, so its circuitry must be working properly.
Your computer must somehow distinguish between a cold and warm boot to decide whether to run its POST diagnostics. To sort things out, your computer uses its normal memory, which it does not wipe out during a warm boot. Each time your computer boots up, it plants a special two-byte signature in memory. When your system boots, it looks for the signature. If it find the signature, it knows it has been booted at least once since you turned on the power, so it does not need to run through POST. When it fails to find the signature, it runs its diagnostics as part of the cold-boot process. Note that if something in your system changes the signature bytes—as crashing programs sometimes do—your computer will run through a cold boot even though you haven’t turned it off.
The signature bytes have the value 1234(hex). Because they are stored in Intel little endian format (that is, the least significant byte comes first), they appear in memory as the sequence 34 12.
Programs can also initiate a warm or cold boot simply by jumping to the appropriate section of BIOS code. However, because some expansion boards don’t automatically reset when your computer runs through the cold-boot BIOS code, anomalies may persist after such a program-initiated cold boot. For example, your video board may place itself into an odd state, and a complete reset may not unlock it. For this reason, some programs instruct you to turn your computer off and back on during the installation process to guarantee all the hardware in your system properly resets.
Power-On Self Test
Every time your computer switches on, the BIOS immediately takes command. Its first duty is to run through a series of diagnostic routines (system checks) called the Power-On Self Test routine, or POST. This ensures every part of your computer’s hardware is functioning properly before you trust your time and data to it. One by one, the POST routine checks the circuits of your system board and memory, the keyboard, your disks, and each expansion board. After the BIOS makes sure the system is operating properly, it initializes the electronics so that they are ready for the first program to load.
Error Codes
The BIOS tests are relatively simple. The BIOS sends data to a port or register and then looks to see the results. If it receives expected results, the BIOS assumes all is well. If it finds a problem, however, it reports the failure as well as it can. If the display system is working, it posts an error-code number on your monitor screen. (The limited amount of memory available prevents the BIOS from storing an elaborate—that is, understandable—message for all the hundreds of possible error conditions.) If your computer is so ill that the display system will not even work, the BIOS sends out a coded series of beeps through your system’s loudspeaker.
Many BIOSs also write the code numbers of the ongoing tests to input/output port 80(hex). Special diagnostic boards that plug into a vacant expansion slot can monitor this test procedure and show the test progress and failure. Repair technicians often use such diagnostic boards when servicing systems.
Beep Codes
Displaying an error code on your monitor screen presupposes that at least part of your computer (and a major part at that) is operating properly—namely, the display system. If your video board or monitor is not functioning and you don’t have a diagnostic board, the error code display is useless. Consequently, most BIOSs also generate error identifications that are independent of the display system.
Instead of visual displays, they use audible error codes played through the small speaker system that is standard equipment in all computers. Because the speaker system links to your computer at a rudimentary level—only a single amplifier chip stands between the speaker and its associated input/output port—the basic computer speaker will always function except during the most dire failures, such as a nonworking microprocessor. (Note that this basic computer speaker is separate from the sound board or multimedia sound system present in most new computers.) These audible error messages take the form of beeps from the system speaker. Consequently, they are usually termed beep codes.
As computers have become more complex, the systems of beep codes have become correspondingly elaborate. Some sound more elaborate than a Mayday call from a sinking ocean liner. Ever BIOS-maker uses its own coding scheme for these aural error warnings. Usually a single short beep means your computer is okay; anything else warns of an error.
Should your computer start with a continuous beep that won’t stop until you switch the power off, your computer has a major problem, most likely with its power or logic system. Oftentimes a defective expansion board or an improperly inserted expansion board will elicit such an unending beep. It can also result from a bad microprocessor or other motherboard problem. If you encounter a beep that won’t end, check your expansion boards first. Ensure that all are seated properly and then remove them one by one or en masse until the beep quiets down. (Be sure to switch off your computer before you add or remove an expansion board.)
BIOS Extensions
After the actual testing of your computer and its associated circuitry is complete, its BIOS begins to execute initialization routines that configure the various options inside your computer. Exactly what happens next depends on the design of the BIOS. A conventional BIOS merely looks for add-in BIOS routines, initializes devices using the routines already in the BIOS, and starts the disk bootup.
Every computer assumes that many of its peripherals are loaded with specific data values when it starts up. That is, all the default operating values are loaded by the BIOS, so your timer knows what to time and the speaker knows the frequency at which to beep. The serial ports are set to their default speed. A Plug-and-Play system like those of nearly all new computers runs through a more structured initialization process that amounts to completely setting up system resources each time the computer boots. The “Plug-and-Play” section, later in this chapter, gives a step-by-step outline of this BIOS boot procedure.
By design, the basic computer BIOS knows how to search beyond the confines of the system board. It knows how to locate the extra instructions and data that get added in with some expansion boards. Although some computers require you to replace the BIOS firmware with new chips to add new features, the computer BIOS was designed to be extendible. That is, the full extent of the BIOS is not forever cast in the silicon of the firmware. The extendible BIOS is capable of accepting additional code as its own, creating one integrated whole. Rather than replacing the BIOS chips, this extendibility means that you can add more firmware containing it own BIOS routines to your computer. The BIOS incorporates the new routines into itself.
The key to making the BIOS extendible is itself an extra firmware routine that enables the BIOS to look for add-in code. During the initialization process, the BIOS code reads through the address range looking for code stored on add-in boards. If it finds a valid section of code, it adds those instructions to the BIOS repertory. New interrupt routines may be added, for instance, or the function of existing routines may be changed.
The routine to extend the BIOS works as follows: Following the actual testing portion of the Power-On Self Test, after basic system board functions have been initialized (for example, the interrupt vectors have been loaded into RAM), the resident BIOS code instructs the computer to check through its ROM memory for the occurrence of the special preamble bytes that mark the beginning of add-in BIOS routines. The original IBM BIOS searches for these preamble bytes in the absolute address range 0C8000(hex) to 0F4000(hex); newer BIOSs check the range from 0C0000(hex) to 0EFFFF(hex). Either of these subsets of the full, reserved, high memory range—that is, 0A0000(hex) to 0FFFFF(hex)—exclude the areas used by video memory and the BIOS itself to prevent confusing data with preamble bytes.
If the BIOS finds the special preamble bytes, it verifies that the subsequent section of code is a legitimate BIOS extension by performing a form of cyclical redundancy check on the specified number of 512 byte blocks. The values of each byte in the block are totaled using Modulo 0100(hex) addition—the effect is the same as dividing the sum of all the bytes by 4096. A remainder of zero indicates that the extension BIOS contains valid code.
The preamble bytes take a specific form. Two bytes indicate the beginning of an extension code section—055(hex) followed by 0AA(hex). Immediately following the two-byte preamble bytes is a third byte that quantifies the length of the additional BIOS. The number represents the number of blocks, 512-bytes long, needed to hold the extra code. Plug-and-Play peripherals have a more structured header that follows the preamble bytes.
After a valid section of code is identified, system control (BIOS program execution) jumps to the fourth byte in the extension BIOS and performs any functions specified there in machine language. Typically, these instructions tell the BIOS how to install the extra code. Finally, when the instructions in the extension BIOS have been completed, control returns to the resident BIOS. The system then continues to search for additional blocks of extension BIOS. When it finally completes its search by reaching the absolute address 0F4000(hex), it starts the process of booting up your computer from disk.
The ROM or Flash memory chips containing this extra BIOS code do not have to be present on the system board. The memory locations used also are accessible on the expansion bus. This feature allows new chips that add to the BIOS to be part of expansion boards that slide into the computer. The code necessary to control the expansion accessory loads automatically whenever the system boots up.
Multiple sections of this add-on code fit into any computer, limited only by the address range available. One complication is that no two sections of code can occupy the same memory area. As a result, the makers of conventional ISA expansion boards typically incorporate jumpers, DIP switches, or EEPROM memory on their products to allow you to reassign the addresses used by their BIOS extensions and avoid conflicts. Plug-and-Play designs have made this conflict resolution automatic during the setup process.
Initial Program Load
Once the BIOS of your computer has completed all its tests, checked for additional BIOS code, and set up all the devices it knows about, it yields control over to your operating system. In older computers, the operating system simply takes over and brings your computer to life. In a Plug-and-Play system, the operating system continues the initialization of the devices inside and connected to your computer. In effect, the Plug-and-Play system completes the BIOS configuration process.
In either case, whether your BIOS completes the initialization of your system or transfers control to the operating system to complete the process, somehow your operating system must load. Your computer must know enough about your disks—floppy, hard, and CD-ROM—to be able to find the operating system and get its code running. The process of getting the operating system started is called the Initial Program Load (IPL).
The IPL procedure originally was a design expedient. When the first computer was created, ROM chips, like all other parts of computers, were expensive. The computer’s designers opted to use as little ROM as possible to get the system started. They added a short code routine at the end of the BIOS test procedure that told the BIOS to read the first sector from your computer’s floppy disk (the only drive in the first personal computers). This first sector is sometimes called the boot sector because of its function.
In modern computers, the BIOS is smart enough to look to your hard disk as well as floppy drive, and sometimes even to your CD-ROM drive, to find a boot sector. Many BIOSs allow you to select which of these are searched for and in what order. If the BIOS finds executable code there, it loads that code into memory and executes it. If it finds no executable code or no available disk, the BIOS complains and does nothing because it doesn’t know how to do anything else.
The small amount of code used by the IPL routine is unforgiving. It searches only the first physical sector on your disks. It looks for sectors rather than clusters or allocation units because at this point it doesn’t know what operating system you have and how it organizes disk storage. The BIOS must know how to find the first physical sector on the disk; consequently it requires a BIOS extension associated with the disk to tell it how to make the required access. A disk drive that uses only a software device driver will be invisible to the BIOS and the IPL routines, and consequently such a disk cannot boot the system.
The code in the boot sector is also short and to the point because it has to fit into the confines of a single sector. This code tells your computer how to find the rest of the operating system. Once it locates the main operating system, the boot sector code starts loading that code into memory and yields control to it. The operating system takes command and completes the process of booting your computer.
Plug-and-Play
One of the gravest shortcomings of legacy computers—old computers built in pre-Pentium days—was that their ISA expansion bus lacked automatic configuration procedures. You were left to adjust settings and configure software yourself. And each of the dozens of settings you had to make brought its own potential for error. Putting even one jumper in the wrong place or throwing the wrong switch was often sufficient to turn two thousand dollars of computer into a noisy desk ornament.
To eliminate such setup problems and shift the tedious job of system configuration to someone (or something) better equipped to deal with it, the computer industry developed the Plug-and-Play initiative. The idea was to make your computer responsible for configuring itself. After all, computers specialize in taking over jobs that you find tedious. The goal was to create computers with no switches, no jumpers, and no headaches. So far, they’ve achieved two out of three, a pretty good average.
The straightforward goal belies the arduous journey in reaching today’s reasonably successful automatic configuration systems. Making Plug-and-Play work required changes in every computer’s BIOS, expansion bus, expansion boards, and operating system. The universal adoption of Plug-and-Play was a lengthy transition, one dragged on as compliant products slowly coursed into the market.
Background
The idea behind the Plug-and-Play initiative was to shift responsibility for remembering and assigning setup options from you to your computer system. After all, your computer likely has a better memory than you do, and it doesn’t mind running through a checkup procedure however many times as is needed.
The first stab at a Plug-and-Play specification appeared with the original Intel/Microsoft specification for ISA on May 28, 1993. That effort inspired other companies to join in. Related standards are being developed to extend Plug-and-Play to other troubling configuration processes, particularly SCSI expansion. Compaq Computer Corporation and Phoenix Technologies joined Intel to develop a BIOS specification for Plug-and-Play, first released November 1, 1993.
Toshiba joined Intel and Microsoft to come up with a system to move power-management responsibilities to the operating system. Because configuring the host system was an important part of power management, they extended their specification to embrace setting up all computer accessories, not just power, with one of its foundations being the Plug-and-Play specification. They called the result the Advanced Configuration and Power Interface (ACPI), first published in December 1996. The next major revision of the specification was Revision 2.0, published on July 27, 2000, as a 450-page tome covering the intimate details of the design of new computers. A minor revision on March 31, 2002, brought the standard up to its current version, Revision 2.0a.
ACPI is neither a hardware nor software specification. Rather, it details the interface between the two. That makes it not only function like the BIOS, but the specification also details how the BIOS works with hardware and software to configure your computer. Although it is not a BIOS in itself, the specification details how your computer’s BIOS must operate. To wear a Windows logo, new computers must conform to the current ACPI version.
ACPI doesn’t replace Plug-and-Play but instead builds upon it. The basic Plug-and-Play system still takes care of configuring your system, but ACPI gives it new commands and versatility. The automatic configuration process is still termed Plug-and-Play (or, by those who have less faith in its reliability, Plug-and-Pray).
For automatic configuration to work properly, it requires all three elements of the system written to its standards—the computer and its BIOS, the operating system, and the expansion boards and peripherals attached to the computer. Any older device that does not conform to the various Plug-and-Play standards is considered to be a legacy device. The Plug-and-Play system attempts to accommodate legacy devices, but it cannot resolve all conflicts between them. Developers see the ultimate solution as being attrition. As time goes by, old noncompliant products will fade from the market. To accelerate the demise of legacy products, Intel and Microsoft have written support for ISA out of their most recent system standards, although many people still insist on at least one ISA slot in their newest computers.
Expansion Board Support
The basic Plug-and-Play procedure is a three-step process that lends itself to automation: First, the Plug-and-Play BIOS directs your system to check what resources each expansion device needs. Next, the BIOS coordinates the assignments to avoid conflicts. Finally, it tells your system and software which choices it has made.
The configuration process calls upon specific hardware features of ACPI-compliant expansion boards. Most importantly, each board is able to deactivate itself so that it does not respond to the normal control signals inside your computer. The board disconnects itself from all system resources so that when it is inactive it cannot possibly cause conflicts.
In addition, each ACPI-compliant board has several new onboard registers that are reached through a standardized set of three I/O port addresses so that the BIOS or operating system can control the configuration of the board. These ports are designated Address, Write Data, and Read Data.
The Address port functions as a pointer that expands the number of control registers directly accessible to your system without stealing more system resources. Loading a register number in the Address port makes that register available for reading or writing through the Write Data and Read Data ports.
The ACPI specification explicitly defines eight card control registers and reserves two large ranges—one of 24 registers for future elaboration of the standard and the other a 16-port range that board-makers can assign to their own purposes. In addition, the specification allows cards to be configured as multiple logical devices, and it assigns ports for their control. The Address port allows the Write Data port to select which of the logical devices is active and the resources used by each.
ACPI-compliant expansion boards act in one of two ways, depending on whether they are needed for booting the system. Boards that are required for bootup (that is, display adapters and disk controllers) start up active. That is, they come online exactly like conventional expansion boards using the resources assigned them as power-on defaults. They will grab the resources that they need, participate in the normal Power-On Self Test procedure, and let you operate your computer normally. They may also cause the same old resource allocation problems, as will any conventional expansion boards that don’t support Plug-and-Play or ACPI. The other Plug-and-Play devices (those not needed in booting your computer) automatically deactivate themselves when your system comes on, waiting to be told what configuration to use by your operating system.
ACPI-compliant boards not required during bootup normally start up inactive. They do nothing until specifically activated, typically by the ACPI-compliant operating system.
Every ACPI-compliant board has specific circuitry for managing its configuration. This circuitry operates independently from the normal functions of the board. Unlike the functional circuits on the board that can be disconnected from the bus interface, the Plug-and-Play circuits always monitor the signals on the bus. However, the Plug-and-Play circuitry operates in one of four states—Wait for Key, Isolation, Configuration, and Sleep—without regard for whether the functional circuitry is active or inactive.
Boot Operation
All ACPI-compliant boards, whether active or inactive, boot up in their Wait for Key state, in which they refuse to respond until they receive an explicit command called an initiation key. This key is not a simple password but rather a precisely defined 32-step interaction between the host system and each board. All 32 steps must be completed successfully before the board can be set up.
Once a board has been singled out with the initiation key, the BIOS can interrogate it individually and determine whether it is required for booting up the system and what system resources it requires. The BIOS allocates the needed resources to boot devices. If a board is not required to boot the system, however, the BIOS bows out, leaving resource assignment to the operating system. The BIOS only needs to get the system going well enough that the operating system can load and take over.
Plug-and-Play boards on the legacy ISA bus use a different process. They are isolated using card select numbers, assigned by the BIOS. Once each board is uniquely identified, it can be automatically configured by the BIOS (if it is required for booting the system) or by the operating system.
Onboard ROM
The ACPI configuration process and the ability to isolate individual boards hold advantages beyond automatic resource allocation. The greatly enlarge the potential capacity of storing firmware on each board.
In pre–Plug-and-Play days, the BIOS scanned each expansion board for additional BIOS code. That code had to fit in a tight range of addresses, and the code contained on each board could not overlap. Using Plug-and-Play technology, the BIOS scans each board in isolation, so conflicts between boards are not a problem.
The Plug-and-Play BIOS scans for additional code exactly like a pre–Plug-and-Play BIOS, looking for the special add-in ROM signature—the two-byte code 055(hex) followed by 0AA(hex)—that indicates a block of add-in BIOS code follows. The firmware on Plug-and-Play boards adds a pointer that immediately follows this signature to indicate the location of an expansion header in the BIOS code or a chain of several headers. Each header is identified by a special four-byte preamble—024(hex), 050(hex), 06E(hex), or 050(hex)—that corresponds to the ASCII characters $PnP.
The ACPI scheme allows the ROM on each expansion board to hold interface and driver code for multiple operating systems, each coded by its own expansion header. An operating system can identify the code that applies specifically to it by reading the headers.
The ACPI specification allows each board-maker a generous apportionment of the available memory and port addresses. Each board can use up to four noncontiguous ranges of memory base addresses for BIOS code and up to eight noncontiguous base addresses for input/output ports. In addition, a board can use from zero to two separate interrupt levels and up to two DMA channels. Each manufacturer determines the number of resources that a given board can use. Which it uses, however, is a matter left to the board-maker.
As this is written, the current ACPI specification is version 2.0a, and it runs over 500 pages long. You can download a copy from a Web site devoted to it, www.acpi.info.
Interface Functions
Although the primary role for the BIOS today is to get your computer started, it retains the name it earned from its function as the software-to-hardware interface of your machine. It is a control system that operates at the lowest possible level (the most basic) at which the input and output of your computer are designed to link to programs. In effect, it is like a remote control for a television set. The BIOS allows your software to press buttons at a distance from the hardware, just as you control the channel of your TV from your easy chair—and without prying open the set and ratcheting its tuning circuits. In operation, the BIOS is a universal remote control. It lets you push the same buttons, regardless of the model or brand of television at which you point it.
The original purpose of this one-step-removed BIOS design was to allow computer hardware to be revised and updated without the need to change software correspondingly. It helps guarantee the backward compatibility of computers. The extra BIOS step is needed, because all computers have many hardware elements that are located at specific addresses in memory or within the range of certain input/output ports. Other computer components may have registers of their own, used in their control, that also are addressed at specific locations. Because of the number of separate components inside any computer, the potential number of possible variations in the location of these features is limitless. Software that attempts to control any of this hardware must properly reach out to these registers. As long as all computers are crafted exactly the same, with the same ports used for exactly the same hardware with exactly the same registers, no problems should occur. But if a computer designer wants to change the hardware to a technology that delivers better performance or greater reliability, he may be stymied by the old addresses. Software may expect to reach the old design at one set of ports, whereas the new-and-improved design may be memory-mapped and not use ports at all. In this case, the old software would not know how to reach the new hardware, and the new design simply would not work.
The BIOS gives the software a link. The software reaches into the BIOS for the hardware function it wants. Then the BIOS dips down into the hardware. If the design of a computer system is changed radically, only the BIOS needs to be changed to reflect the new way of getting at the features of the computer. The changed BIOS still works the same way as the software, so all older programs run exactly as they did before the change. In effect, the new system design requires a new route to get to an old destination—a detour. The new BIOS is an updated roadmap that shows only the detour.
Certainly today’s driver software easily accomplishes this function of the BIOS. Back in the days when the computer was first created, however, there were no drivers. The original computer BIOS didn’t even have provisions for adding extra hardware, and the first operating system had no intrinsic provisions for adding drivers. Not knowing what was to come of the personal computer, IBM put its reliance on BIOS technology in its first computers and reserved the right to alter the hardware at will. The company made no guarantee that any of the ports or registers of the computer would be the same in any later computer.
In effect, IBM created the computer in a well-ordered dream world in which programs would never need to directly address hardware. Instead, each program would call up a software routine in the BIOS, which would have the addressing part of the instruction permanently set in its code. Later computers with different hardware arrangements would use BIOS routines that worked like the old ones and were indistinguishable from the old ones when used by application software. The addresses inside the routines would be changed, however, to match the updated hardware. The same software could work, then, with a wide variety of hardware designs, giving the designer and manufacturer the flexibility to upgrade the entirety of system hardware, if necessary.
Compatibility
In the days when your computer’s operating system worked cooperatively with the BIOS instead of co-opting its function, BIOS compatibility was a major issue in buying a new computer. A computer had to have a BIOS functionally equivalent to that of an IBM personal computer to work reliably with the software of the day. Consequently, after the IBM BIOS made its debut, it became the most copied set of software routines in the world. The computer BIOS laid out all the entry points used by subsequent IBM BIOSs and most compatible BIOSs as well. It also defined the functions that could—and must—be expected in any BIOS as well as established the way that the BIOS works. The BIOS that IBM developed for its 1984 Personal Computer AT still defines the minimum level of compatibility for all computers.
Today, computer-makers can buy a compatible BIOS off the shelf from any of several sources. It wasn’t always that easy. Achieving off-the-shelf BIOS compatibility was one of the great sagas of computer history.
Because the copyright laws forbade any copying of someone else’s work, compatible BIOSs had to be written “clean.” That is, the programmers were kept from ever viewing the source code or having any knowledge of the routines it contained. Instead, they worked from a list of instructions and the functions that the BIOS carries out when given each specific instruction. In other words, they looked at the BIOS they wanted to copy as a black box that takes an input and gives an output. The programmers then deduced the instructions for the inside of the box that would give the desired results.
Working in this way was time consuming and expensive. Few computer companies had the resources to do it all themselves. Compaq was the first to successfully tackle the job. The vast majority of compatible computer manufacturers bought the necessary BIOS firmware from specialist firms. The first to offer compatible BIOSs was Phoenix Technologies. Now computer-makers also select BIOS chips from American Megatrends, Inc., Award Software, and Mr. BIOS.
Because each BIOS vendor must develop its own product separately, the exact code used by each BIOS version is different. Functionally, however, they all look the same to your software (including your operating system).
At the other side of the interface—where the BIOS links to your computer’s hardware—BIOSs can be quite different. By design, every BIOS is created to match the specific hardware in the computer in which it operates. That is part of its job—uniting different hardware designs so that they work interchangeably with all software. Every BIOS is customized for the computer it controls. Typically, computer motherboard manufacturers modify a generic BIOS from one of the BIOS-makers to suit their own purposes.
Because each BIOS is customized for a particular model of computer, no generic BIOS can hope to work properly in a given computer. BIOSs are not interchangeable. Moreover, should you want to change or upgrade your computer’s BIOS for any reason—either through buying new chips or downloading code for Flash memory—you need to get one that matches the exact model of computer you own.
Software Interrupts
The BIOS design created for the first computers does its linking through a system of software interrupts. To gain access to the underlying hardware, a program sends out an interrupt, which is a special instruction to the microprocessor. The software interrupt causes the microprocessor to stop what it is doing and start a new routine. It does this by suspending the execution of the code on which it is working, saving its place, and then executing the program code of the BIOS routine.
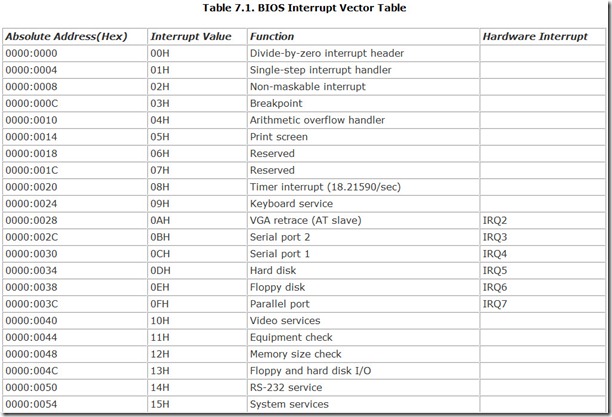
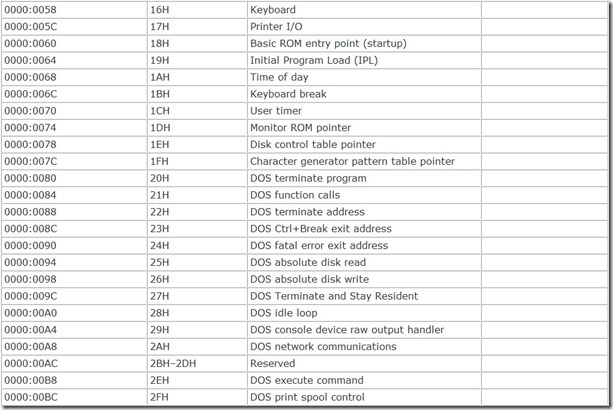
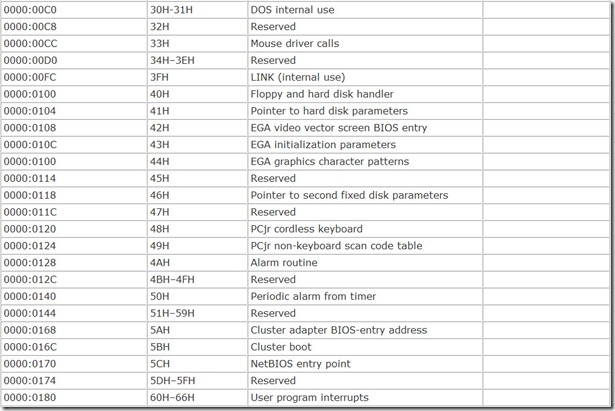
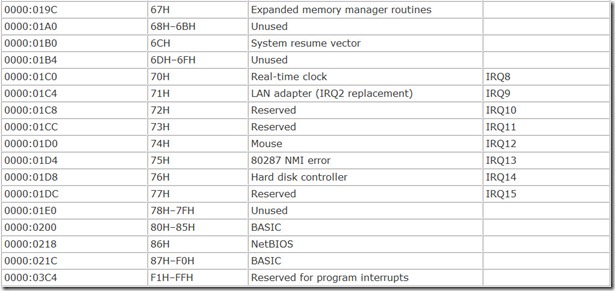
The various functions the BIOS carries out are termed interrupt service routines or interrupt handlers. To call a given interrupt handler, a calling program needs to be able to find the program code that carries out the function. The design of the computer BIOS allows the system to put these interrupt handlers at any convenient address. So that a calling program can find the proper routine, the BIOS reserves part of your computer’s memory for a map called a BIOS interrupt vector table. This map consists of a long list of 32-bit addresses, with one address corresponding to each interrupt handler. These addresses point to the first byte of the program code for carrying out the interrupt and are called interrupt vectors. The microprocessor reads the value of the vector and starts executing the code located at the value stored in the vector.
The table of interrupt vectors begins at the very start of the microprocessor’s memory, address 00000(hex). Each vector comprises four bytes, and all vectors are stored in increasing order. Table 7.1 summarizes the principal BIOS interrupt vectors and the associated functions.
The interrupt vectors are stored in the RAM of your computer so that the values in the table can be changed. For example, a program or software driver may want to alter or update a BIOS routine to take advantage of a special feature of new hardware you install in your computer. The BIOS code itself loads default values for many of these interrupt vectors into the appropriate RAM locations with the vectors pointing at the routines stored in your computer’s ROM.
Sometimes programs add extra routines to a given BIOS function, a process called chaining interrupts. To chain an interrupt, a program looks at the interrupt vector it wants to chain to and remembers its value. It then substitutes the starting location of the program code that it wants to add to the old routine. It then modifies its own code to make the execution of its routines jump to the old interrupt when the processing of the new code finishes. In this way, the new routine added in the interrupt chain executes first and then starts the original interrupt handler.
Parameter Passing
Because fewer interrupts are available than tasks you might want the BIOS to handle, different functions are available for many of the interrupts. These separate functions are identified through a technique called parameter passing. An interrupt needing service from the BIOS—the calling program—passes a number identifying the command to be carried out to the BIOS as a parameter, a value held in one or more of the registers at the time the software interrupt is issued.
The calling program decides what function it wants the BIOS to carry out, loads the parameter value into the proper register, and issues the interrupt. The BIOS code examines the register to determine what function the programs wants.
This same technique may be used to pass information between the calling program and the BIOS. The data to be passed along is simply loaded into one register and the parameter identifying the command into another. To pass new data back to the calling program, the BIOS loads the data into a register, which the calling program can then read.
Using registers to move data into a BIOS routine has its shortcomings. The functions and parameters are limited to those that are common among computers. There’s little room for programs to add their own interrupts. Moreover, the scant number of registers in Intel microprocessors limits the number of parameters that can be passed to and from a function. Most routines use a single byte of data.
To move larger blocks of data, some BIOS routines and most programs use memory. A calling program stores the values it wants to pass to a subroutine in a block of RAM addresses. It then passes to the subroutine the location of the data, and the subroutine digs into the data, changing what it requires, and leaves the block for later access by the program. Although programs and subroutines identify the block of memory by its address, programming languages let you use names for the data. The program chooses the block of addresses to associate with the name and looks to those addresses whenever the programmer uses that name. Similarly, program subroutines may be named, and the program uses the names to find the block of memory holding the microprocessor instructions that comprise the subroutine.
Entry Points
The various code routines in each BIOS start and end at addresses assigned to the BIOS function in the computer memory map. The address at which each routine starts is called that routine’s entry point. The entry point of a BIOS function is completely different from the interrupt that calls that function. When the BIOS in your computer sets itself up—either before or during the actual bootup—it loads the addresses of the entry points into a table in memory that becomes the interrupt vectors. In theory, an entry point can be at any location for any BIOS function—it needs only to be loaded into the slot in the BIOS interrupt vector table to be properly recognized. Unfortunately, some program writers decided to call BIOS routines by their entry points instead of using interrupts, because the direct approach is faster. Consequently, a few applications require that some entry points be at specific physical BIOS addresses. If the entry point of a BIOS differs from what the program expects, the result is likely to be a system crash.
IBM has maintained the same entry points with all its BIOSs, and many compatible BIOSs use exactly the same addresses. A few do not, however. In general, the BIOSs with varying entry points have been written as programming modules that can be combined in various ways to suit the needs of a computer designer. What these modular BIOSs add in flexibility, they lose in compatibility.
Unlike programs that write directly to system hardware, however, programs that require specific BIOS entry points are rare. With the popularity of compatible computers and modular BIOSs, they are sure to become more rare. Modern software, nevertheless, is getting away from a dependency on complete compatibility down to the level of specific entry points. In fact, many programs avoid the BIOS entirely.
The chief beneficiaries of the BIOS are individual programmers who need to create code quickly. In many cases, using BIOS routines can simplify the writing of a program. Certain system operations always are available and can be accessed easily through software. They are reasonably well documented and understood, removing many of the programmer’s concerns.
Linking to Hardware
Controlling the hardware of your computer requires that your system be able to pass commands and data to that hardware. For example, if you have a modem, you need to send the modem commands to dial numbers and change speeds. Once you’re communicating, you have to send bytes, even megabytes, of data to the modem and receive more bytes in return.
The BIOS routines may use memory or I/O ports to pass the commands and data to hardware devices. When a device uses a block of memory to exchange information, it is termed memory mapped. When it uses I/O ports, it is termed I/O mapped.
Memory mapping works exactly as described in the previous section on parameter passing. The BIOS routine and hardware device share a common range of memory addresses they use for passing bytes back and forth. Programs use BIOS routines instead of physical addresses to reach memory-mapped devices, giving the hardware designer the freedom to move the memory window used by a given device. The designer needs only to change the interrupt handler to match the address he chooses.
I/O mapping uses input/output ports to exchange data. An input/output port of a microprocessor is a special range of addresses that is isolated from main memory and has special access instructions.
In the Intel scheme of things, microprocessors have a range of 65,536 input/output ports (compared to over four billion discrete memory addresses). However, due to an aberration in the design of the first expansion boards for computers, only 1024 are commonly assigned to devices that plug into standard computer expansion slots. To cut costs of the first expansion boards, engineers designed boards to decode only 10 of the 16 address lines.
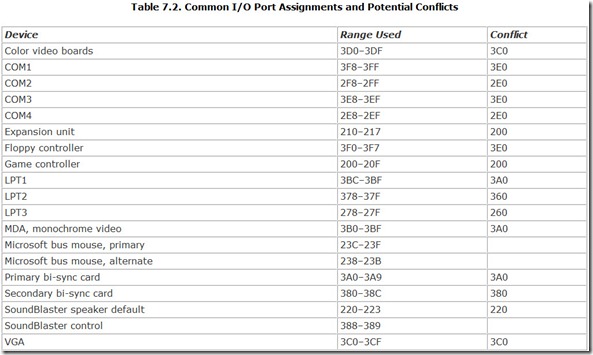
Although newer buses can take advantage of the full range of input/output ports, expansion boards can quickly consume the available ports, or two boards may attempt to use the same port. Such conflicts between boards is the most common reason why expansion boards fail to operate properly. Sometimes installing an expansion board creates a port conflict that prevents the rest of the system from working at all. Table 7.2 lists some of the common conflicts that arise in I/O port assignments.
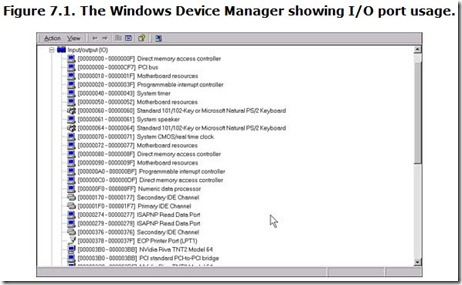
If you’re running Windows on your computer, you can view the actual I/O port assignments used by your computer. To view these assignments, consult the Device Manager by selecting the System icon in Control Panel. Select your computer on the Device menu and click the Properties button. From the View Resources menu that pops on your screen, select the Input/Output (I/O) radio button. You’ll see a screen akin Figure 7.1, listing all the input/output ports in use and the hardware using them.
Through Plug-and-Play and the manual options of the Add Hardware process, Windows generally will make the proper assignments of I/O ports. If you want to reserve one or more I/O ports so that devices you install later cannot steal them, click the Reserve Resources tab and enter the ports you want to reserve.
New expansion buses such as PCI provide access to the full range of I/O ports, thus reducing the chance of conflicts. Plug-and-Play expansion boards are supposed to automatically resolve port conflicts entirely. Eventually, worries about I/O conflicts should disappear. For most computers, however, eventually has not yet arrived.
Storage Functions
Because the BIOS comes in the physical form of ROM chips, its storage functions should not be surprising. For example, the BIOS stores its own name and the date it was written inside its own code. But the BIOS also incorporates storage functions that go beyond the bytes encapsulated in its ROM silicon. Although physically separate from the BIOS chips themselves, the setup memory of your computer is controlled by BIOS functions and is often considered with—and even as part of—the BIOS. This memory records vital details about your computer hardware so that you don’t have to set up each expansion board and disk drive every time you switch on your computer. In addition, the BIOS tells your computer to reserve several small blocks of memory for dynamic data that your computer and its operating system use for tracking several system functions.
Legacy Data
As with any computer program, the BIOS code uses data for its operations and produces data as its result. The BIOS stores some of this data to be used as a reference by your programs. The BIOS acquires some of this information as it sets up the system. By storing it all in one place, the BIOS eliminates the need for every program to waste its time looking up common features. Other data is encoded as part of the BIOS itself so that programs can determine what kind of computer—and what kind of BIOS—they have to work with.
BIOS Data Area
During the initialization process, the BIOS searches through the system for specific features. It checks the number and kinds of ports installed, the type of display adapter (monochrome or color), and other options. Included among the data that it stores are equipment flags, the base addresses of input/output adapters, keyboard characters, and operating modes. The BIOS then stores this information in specific memory locations so that your programs can check to see which features are available or being used. For example, the BIOS looks for serial ports at specific addresses (see Chapter 11, “Ports”). As it finds them, the BIOS records the base address that each serial port uses.
All this self-descriptive information about your system is stored in a special part of RAM called the BIOS data area. Located just above the interrupt vectors, the BIOS data area comprises 256 bytes of memory, starting at absolute memory location 000400(hex) and running to 0004FF(hex).
Date
Nearly every BIOS identifies itself with a copyright message and (usually) a version number so that you can determine who made it. (More specifically, the copyright message protects the writers of the BIOS from other people copying their work.) This identification information may appear anywhere within the BIOS code range.
In addition, the revision date of your BIOS helps you identify how recently its code was updated. As computers have expanded their capabilities, BIOSs have been revised to enable new operations. Sometimes older BIOSs will not work with new peripherals. For example, many BIOSs from before 1998 don’t let you use all the space on hard disks larger than 8GB. Older BIOSs may impose even more severe limits.
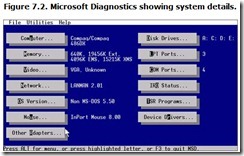
You can determine the date of your BIOS in several ways. The most convenient include catching the bootup screen of your computer, which usually displays the date and revision number of the BIOS, and using a diagnostic utility. Microsoft Diagnostics, supplied with most versions of Windows, will show you the detail of your computer’s BIOS—its date and manufacturer. This program is located in the Command subfolder of your Windows folder as MSD.EXE. You can either click its icon or run it from the MS-DOS prompt by typing MSD and then pressing Enter. Click the Computer button, and it will list some of the BIOS details of your computer, as shown in Figure 7.2.
Note that Microsoft has not updated the diagnostic program for years, so the most recent microprocessor it will recognize is a 486DX! The System Information program found under System Tools in Accessories from the Programs option at the Start button is Microsoft’s preferred tool. It shows your system in exquisite, even painful, detail, but it offers no direct display of your system’s BIOS date.
System Identification Bytes
The original computer BIOS included a byte of data to identify the kind of computer in which the BIOS was installed. Programs that might react differently depending on the processor or other aspects of the computer could use this byte to identify the hardware and adjust themselves accordingly. At least that was the idea of the IBM engineers who came up with it in 1981.
The scheme had its problems, however. Allowing for a single byte soon seemed shortsighted, so this memory area was expanded to two bytes, starting with the IBM XT Model 286, introduced in 1985. The overall storage area was termed the system identification bytes, and in IBM nomenclature, it was divided into the model byte and the submodel byte. A third byte was reserved to indicate any major revision to the system.
IBM created an elaborate table of designations for the various computer models it offered. Unfortunately, the company made no provision to coordinate the use of this storage area for other manufacturers. Consequently, the rest of the industry used designations marking their IBM equivalent. Because all systems since 1984 follow the architecture of the IBM AT system, nearly all computers now define themselves as using the AT code. In other words, the system identification bytes store essentially meaningless data.
The model byte is located at absolute memory address 0FFFFE(hex) and is FC(hex) in nearly all current computers. The submodel byte follows it with a value of 01(hex). The revision byte follows next and is usually zero.
The BIOS also has its own individual identification encoded into its bytes. Although it may be nothing more than a copyright notice, each BIOS has some code identifying its origins. Most BIOS makes have their own codes to identify the version of the BIOS, which revision it is, and even the model of computer for which it is meant.
Disk Parameter Tables
One of the more important entries in the BIOS data area is the disk parameter table. Most computers store the parameters used by user-defined hard disks, typically reflected as hard disk type 47 in the setup program, in the BIOS data area. The most common memory location for this information is absolute address 0000:0300. Some BIOSs give you the option of locating the disk parameter table in an alternate location, typically DOS memory. In any case, interrupt vector 41(hex) points to the location of the disk parameter table for the first hard disk in a computer. Interrupt vector 46(hex) points to the location of the parameters of the second hard disk.
In general, the best location for your disk parameter table is absolute address 0000:0300. However, some peripherals, such as older sound cards and network adapters, use this address for their own purposes. Conflicts between the peripheral and your hard disk may render either or both inoperable. Relocating the disk parameter table through a BIOS setting solves the problem.
You may encounter two kinds of disk parameter tables. A standard fixed disk parameter table (FDPT) contains a single description of the vital parameters of the associated hard disk, listing the number of cylinders, heads, and sectors used by the disk. An enhanced fixed disk parameter table (EDPT) has two entries: the logical cylinder-head-sector values and the physical cylinder-head-sector values. The logical values reflect the way your computer sees and accesses the disk. The physical values reflect the actual number of cylinders, heads, and sectors used by the disk.
The standard FDPT is sufficient only for smaller disks, those with both fewer than 1024 cylinders and a capacity less than 504MB. Due to the design of the standard FDPT, only ten bits are allowed for storing the number of cylinders, so numbers larger than 1024 cannot be encoded. The EDPT defaults to 16 heads for all disks, allowing four more bits for storing the number of cylinders.
Your computer deals with any disk by the logical values in the EDPT. Programmers check the value stored here using software interrupt 13(hex).
DOS Tables
DOS stores many of the parameters it uses for managing your computer and its programs in a series of tables. To achieve the utmost in compatibility, DOS locates these tables at the lowest available reaches of conventional memory. Among the data stored here are file handle identifications (FILES), the last referenced disk data (BUFFERS), file control information (FCBS), drive tables (LASTDRIVE), and system operating information (STACK).
Most memory managers allow you to relocate this data into XMS memory to free up more space in the conventional area. Although this technique is commonplace and well tested, you will sometimes encounter compatibility problems, such as a crash of your system. For example, early incarnations of most network operating systems expect to find this data in conventional memory (along with COMMAND.COM itself). The only way to avoid this problem is to avoid the network, avoid DOS, or refrain from relocating this data with your memory manager—the last usually being the most viable option. You’ll want to avoid relocating any of these DOS tables if your system exhibits compatibility problems or its network redirector behaves oddly.
ACPI Tables
One of the chief responsibilities of an ACPI-compliant BIOS is to set up the ACPI tables that describe the interfaces to the hardware installed in the system. The operating system can then read the tables to determine not only the resources required by a specific board but also the code with initialization routines or arbitrary operation sequences needed to make the hardware function. The ACPI tables may contain not only data but also program code in p-code, the programming code or the language of the ACPI system.
The ACPI specification describes a programming language, called the ACPI Source Language (ASL), in which engineers can write their code for their device interfaces. ASL is then compiled into ACPI Machine Language (AML), the object code that is actually stored in the ACPI tables. The ACPI-compatible operating system reads the AML as a set of program instructions.
The BIOS sets up the tables during the boot process. It reads the data for each table from the devices it scans and then stores each table separately in system memory. It makes one master table, called the root system description table, which holds the location of each of the separate data tables.
The BIOS itself does nothing with the data it puts in these tables. It is only an agent that moves the data from device to memory. The ACPI-compliant operating system uses the data or p-code contained in the tables.
To enable the operating system to find the root system description table, the BIOS plants a pointer in the Extended BIOS data area of memory. The operating system identifies this root system description pointer by looking for the character sequence “RSD PTR” (including the trailing space) in the Extended BIOS data area. The pointer stores the base address of the root system description table from which the operating system can find the rest of the tables.
System Configuration
In order to properly test a computer, the BIOS needs to know exactly what it is testing—what peripherals are installed, how much memory it must look through, and whether you have installed a coprocessor. In order to boot a computer, the BIOS needs to know exactly what kind of disk is connected to it. In order for you to see what is going on when your system boots up, the BIOS needs to know what kind of display system you have.
In some cases, the BIOS code itself can be written to search out and find the vital information it needs to get your system going. Such a search is not always accurate, nor is it easy to write the proper search method into a few kilobytes of BIOS code. Even if the proper program could be written and packed into ROM, you probably do not want to sit around and wait—and wait—while the BIOS probes into every nook and cranny to see if something is there.
To let the BIOS (and the rest of the computer) know what options are installed in a given system, all computers record vital setup information that can be referenced quickly. The storage system for this data—that is, system setup memory—has one requirement: It must be nonvolatile. Other than that, the storage format and method are flexible because the BIOS isolates them from the rest of your software. The BIOS looks up this system data and transfers it to the BIOS data area for reference by your programs.
This flexibility has given designers freedom to use a number of storage technologies for this setup information. Among the most popular have been physical memory (switches), nonvolatile electronic memory, and magnetic (disk) memory. Since the AT was introduced a decade and a half ago, however, the basic form of this setup memory used by most computers has been the same—a few bytes of CMOS memory kept fresh (that is, continuously operating) by battery power.
CMOS
When the world and computers were young, all the differences between computers could be coded by one or two banks of DIP switches. But as the options began to pile up, the switch proved to be more a problem than a panacea. A reasonable number of switches couldn’t allow for the number of options possible in a modern computer. Another problem with switches is that they are prone to mechanical problems—both of their own making and otherwise. Switch contacts naturally go bad, and they can be helped along the path of their own destruction by people who attempt to adjust them with pencils (the graphite that scrapes off the point is conductive and can short out the switches). People often set switches wrong and wonder what is awry.
Background
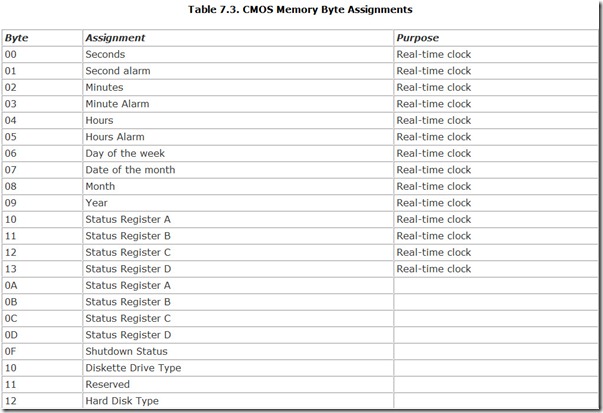
IBM developed a better scheme for the AT. Vital system parameters would be stored in a special, small block of battery-backed CMOS memory, a total of 64 bytes, in the form of a special chip, a Motorola MC146818, which also held a real-time clock. The lower 14 of those bytes are used by the real-time clock to hold the current time and an alarm time, leaving 40 bytes for storage of setup information. Locations were assigned for storing information about floppy and hard disks, the presence of a coprocessor, the amount of installed memory, and the type of display system (monochrome or color). Because CMOS memory is volatile, every system has a battery of some kind to keep this memory fresh and the real-time clock running. (See Chapter 31, “Power.”)
Most computers followed the basic IBM scheme, minimally augmenting it to reflect the increasing capabilities of their systems. Although the MC146818 chip rarely appears in computers anymore, its functions are carried over into new support chips. For example, clock modules from Dallas Semiconductor incorporate all the functions of the Motorola chip, a built-in lithium battery, and more. The only major change in CMOS storage that has been made is the almost universal adoption (under the aegis of Microsoft) of the Plug-and-Play system.
Basic Memory Assignments
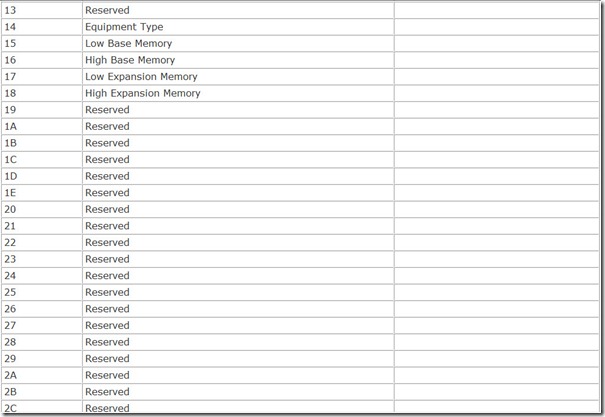
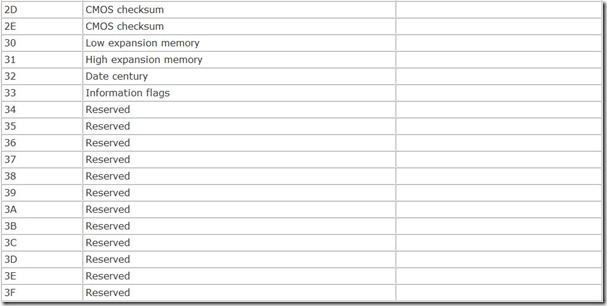
The basic CMOS data remains the same regardless of the manufacturer of the computer, and the various bytes of data are stored in the same rigidly structured format. Table 7.3 summarizes the basic storage assignments that are common across nearly all modern computers.
Although the CMOS that holds this data is conventional memory, it is not in the direct reach of your computer’s microprocessor. Unlike normal system memory, this CMOS setup memory was I/O mapped. That is, its contents were accessed through two input/output ports. Port 070(hex) indicates the memory byte you want to access, and port 071(hex) provides the pathway to the indicated byte. Reading or writing a byte of CMOS setup memory requires two steps. First, you write to port 070(hex) with the byte location in the CMOS range you want to read or write. Reading port 071(hex) tells you the value stored at the location you have chosen. Writing to port 071(hex) changes the byte value at the appointed location.
The contents of most of the storage locations in this CMOS setup memory are monitored by storing a checksum in bytes 02E and 02F(hex). If the checksum does not agree with the modular total of the monitored bytes, your system reports a CMOS memory error. The diagnostic status byte, 00E(hex), indicates the gross nature of the error and additionally reports whether battery power has failed. If all systems are go, this byte has a zero value; any bit set indicates a specific error (with two bits reserved).
Newer computers have elaborated on this CMOS storage scheme, adding more bytes to hold the status of other system features. In function and operation, however, all follow the pattern set by the AT.
Resetting CMOS
The chief reason you’re advised not to tinker with the advanced settings of your computer’s BIOS is that the control they afford allows you to set your computer up so that it does not work. For example, if you err by setting too few wait states for the memory you have installed in your computer, you may encounter a memory error as soon as your computer switches on and checks its BIOS settings. You won’t have an opportunity to jump back into setup to fix the problem. You’ll be stuck with a dead computer and have no way of bringing it back to life.
Well, not quite. Most computer BIOSs have factory defaults that are set conservatively enough that the machine will operate with whatever you’ve installed. The only trick is to restore the factory defaults.
Switch or Jumper Reset
Many computers have jumpers or a DIP switch that forces the reset. Check the documentation of your computer or motherboard to see if this option is available to you. Typically you’ll find this information using the index of your instruction manual and looking under “factory defaults” or “BIOS defaults.”
The exact procedure usually takes one of two forms, depending on the design of your computer. The easiest requires only that you move a jumper or slide a DIP switch and then turn your computer back on. The position of the switch or jumper doesn’t matter. All that counts is that you move it. The most complicated procedure isn’t much more difficult. You move the jumper or slide the switch, wait a few minutes, and then move it back. The delay allows the tiny amount of power that’s locked in the CMOS circuitry to drain away.
Power Deprivation
The alternate procedure for resetting your CMOS works for nearly every computer and is based on the same power-depravation principle. You only need to deprive your computer’s CMOS of its battery power so that the contents of its memory evaporate. Exactly how to deprive your CMOS of its lifeblood electricity depends on the design of your system.
If your computer’s motherboard uses an external battery, simply unplug it from the motherboard. If your computer uses a replaceable disc-style battery in a matching battery holder, pop the battery out. In either case, allow ten minutes for the residual power in the CMOS to drain away before reconnecting or reinstalling the battery.
Some motherboards use permanently installed rechargeable nickel-cadmium batteries instead of replaceable cells. Usually these computers have some provision for electrically disconnecting the battery power from the CMOS (a jumper or switch, as noted in the preceding section). A few computer motherboards make no provision for disconnecting their nickel-cadmium batteries (also known as ni-cads). If you have such a computer and have put your BIOS in a nonfunctional configuration, as a last resort you can sometimes force a reset to the factory defaults by discharging the battery. The battery will recharge the next time you operate your computer.
Never short out a nickel-cadmium battery to discharge it. The low resistance of ni-cad cells produces high currents (even with small batteries), sufficient to melt circuit board traces and even set your computer on fire. Instead of shorting out the battery, discharge it through a resistor. A half-watt, 39-ohm resistor will safely discharge a ni-cad cell in about half an hour without danger to you or your computer. Alternately, you can use a six-volt lamp, such as one designed for battery-powered lanterns, as a battery load. The lamp will show you the progress of the discharge, glowing brightly at first and dimming as the battery’s charge gets drained away. Connect either the resistor or the lamp directly between the terminals of the battery using clip leads.
Advanced Setup
After you press the right combination of keys to bring up your computer’s setup menu, you are usually allowed to jump to Advanced Setup. This extension of Setup allows you to alter vital system operating parameters that are controlled by the motherboard chipset. The Advanced Setup procedure alters additional, often proprietary, storage in CMOS and, sometimes, in other parts of your computer. Typically, Advanced Setup is a second menu (or series of menus) accessed through the initial Setup menu.
Altering the options can have a dramatic effect on the performance of your computer. Importune tinkering often can lead to having a machine that will not work. Performance becomes zero. On the other hand, you can sometimes optimize your system to take best advantage of the options you’ve installed (for example, to coax the best possible performance from the memory system or highest transfer rate from your expansion bus).
The range of features controlled by advanced setup varies with both the BIOS and the chipset inside your computer. Most chipsets give you a wide range of options to wade through. However, one of the most popular, Intel’s Triton chipset, provides very limited control range. For example, the only way to alter the ISA bus speed is to change jumper or DIP switch settings, and you cannot alter cache timing at all.
Some of the options available with different chipsets and BIOSs are detailed in the following subsections.
Parity Check
Some systems permit you to switch off memory parity checking, thus disabling error detection. Taking this option prevents your system from halting when memory parity errors are detected. You are well advised to leave parity checking enabled except when attempting to find elusive memory problems. Because this option is meaningful only for computers that have parity-checked memory, it offers you no savings as would a system that used 8-bit SIMMs instead of parity-checked 9-bit SIMMs. Your system is likely to halt when a parity-error occurs in program code, but the crash is less controlled than an error-warning message. Files may be destroyed. If the error occurs within data, you may never know when your information is inaccurate.
Memory Testing
Testing the prodigious amounts of RAM in a modern computer can take a long time, indeed, adding a minute or more to the cold boot sequence. To minimize the wear and tear on your patience, many BIOSs allow you to defeat the entire memory test sequence or specific portions of it. With the claims of extreme reliability for today’s memory systems, you may want to consider switching off your computer’s memory test.
Commonly you’ll find an option called Above 1MB Memory Check that allows you to switch off memory testing beyond the base megabyte in your computer. Selecting this option will cut your bootup time from a few minutes to a few dozen seconds. Checking the base megabyte of memory in your computer usually is not an option because your computer needs error-free real-mode memory for running the setup program.
Some systems give you the option of adding an audible click or beep each time a memory block of a megabyte or so is tested. The sound is simply reassurance that your computer is successfully coursing through its lengthy memory test. Some people find this sound obnoxious rather than reassuring, and the Memory Test Click Sound setup option allows them to silence their systems.
Numeric Processor Testing
The BIOSs of some older computers offer the option of defeating the numeric processor test. Although you might be tempted to forgo this test to accelerate the boot process, you may be surprised at its effect. Many BIOSs assume that if you tell them not to test the numeric processor, you don’t have one. They set a flag that tells your applications you don’t have a coprocessor installed, so your software won’t use the coprocessor even if one is installed—even as part of your microprocessor.
Computers based on the 386 and 486 microprocessors may also give you the option of selecting a Weitek coprocessor. You must select this option to enable your software to take advantage of the Weitek chip.
Cache Operation
Some systems require that you set the size of secondary (external) memory cache you have installed. You’ll want to change this setting only if you install additional SRAM chips to increase the size of your computer’s memory cache.
Some BIOSs allow you to switch on or off the cache. Some allow the individual control of the internal (primary) cache inside your microprocessor and the external (secondary) cache. The only time you should switch off your system’s caches is when you want to pin down software problems or diagnose hardware errors.
Wait States
This setting controls the number of wait states injected during memory accesses. Typically, you have a choice of zero, one, two, or possibly three wait states. Some systems allow the separate setting of read and write wait states. Choosing fewer wait states makes your computer faster, but choosing too few to accommodate the speed of your system’s memory leads to memory errors. Set this value too low and your computer may not boot at all. If you are a die-hard tinkerer and want to explore the potentials of this setting, adjust it downward one step at a time. Then run your computer for a while to check its reliability. Toying with this may also familiarize you with the location of the CMOS reset jumper.
Bus Clock
Many ISA systems allow you to adjust the clock speed of their expansion buses so that you can eke the most performance from your old expansion boards. Some systems give you a choice of clock speeds in megahertz; others express the speed in terms of the microprocessor clock (for example, CLOCKIN/4 implies one-quarter the microprocessor clock speed—8.25MHz with a 33MHz system). Higher speeds (lower divisors) can deliver more performance, but rates above about 12MHz may sacrifice reliability. In VL Bus and PCI systems, the bus clock setting has less effect on overall performance because the devices that need the most bus bandwidth (that is, a faster bus speed) will be connected to the higher-speed local bus. The clock speed of the local bus is not affected by the bus clock setting.
ROM Shadowing
Manufacturers may provide any of a number of options to enable or disable the shadowing of ROM code in fast RAM memory. Some merely allow the simple enable/disable choice. Others allow you to control ROM elements separately. One variety of BIOS lets you individually enable/disable system ROM and expansion ROM. System ROM means the BIOS code on your motherboard; expansion ROM is the code on expansion boards, which typically includes your video card and hard disk host adapter. Another variety of BIOS gives the choice of system, video, or adapter. A fourth BIOS type lets you choose whether to shadow ROM memory by address range, letting you select enabling or disabling by 16K, 32K, or 64K blocks.
In general, you should shadow only those memory ranges actually in use by ROM. Shadowing unused ranges wastes memory. Shadowing memory ranges used for buffers by network adapters or ancient expanded memory (EMS) boards may actually degrade system performance or cause compatibility problems.
Remember, shadowing only helps the performance of applications that use BIOS code in ROM, which for the most part means only DOS. If you primarily run any version of Windows or OS/2 that makes little use of the BIOS, shadowing yields no performance improvement and may cause compatibility problems. You will probably want to switch off shadowing when using any modern operating system.
Experimenting with shadowing can also lead to a system that does not boot. It is best to enable one block or shadowing feature at a time and then run your system to observe the result.
Concurrent Refresh
Most early computers must devote 10 percent or more of their active time to refreshing memory. Newer systems are able to refresh memory concurrently (that is, while they are performing normal tasks). Concurrent refreshing ekes more performance from your system, so it is the preferred operating mode. Some BIOS-makers call this kind of memory refresh hidden refresh. Normally your computer will deliver better performance with concurrent refresh. Some older RAM designs (used mostly in 386 and older computers) cannot handle concurrent refreshing and may cause memory errors when this feature is enabled.
Page Interleave
Some systems with two or four identical banks of RAM chips or memory modules can operate in an interleaved fashion (that is, alternating banks in back-to-back memory requests). Statistically, interleaving can cut wait states by nearly half. Although the effect is less pronounced in modern cached systems, enabling page interleave (when supported with sufficient memory) can improve performance.
Page Mode
Page mode memory chips and modules also can trim wait states. Page mode SIMMs can make repeated accesses to one memory page without wait states. If you equip your system with page mode memory and enable this option, you should get better performance.
Virus Protection
With all the concern in the industry about computer viruses, some BIOS-makers have added their own form of protection, a warning message that appears when software attempts to write to the boot sector of your hard disk. When the protection is switched on, you’re given the option of canceling the write operation to prevent infection. Because some operating systems, such as the OS/2 Boot Manager, rewrite boot sector data when you switch between boot modes, you can’t simply obstruct all boot sector write operations.
The protection afforded by this system is limited in two ways. It potentially stops only boot sector viruses. It does not stop those that afflict the active operating system files. Also, it protects only hard disks controlled through the computer BIOS. SCSI disks that rely on separate BIOS code in your SCSI host adapter are not protected.
Typematic Rate
Many BIOSs allow you to alter the way the keyboard reacts to your keystrokes, repeating them if you hold a key down. This feature, called typematic, is fully discussed in Chapter 20, “Keyboards.”
Many BIOSs have an overall toggle, typically termed Typematic Programming, that enables or disables the settings for the typematic feature. You must enable typematic programming to alter other typematic settings. In addition, your keyboard must allow its typematic feature to be programmed. You can control the typematic feature through Windows 95 and 98 no matter what kind of keyboard you have or the BIOS typematic settings.
If a BIOS and keyboard support typematic programming, you can generally alter two aspects of this feature. Typematic Rate Delay specifies how long you must hold down a key before the typematic feature kicks in and characters start repeating. This setting is generally specified in milliseconds. Typematic Rate controls how quickly the characters repeat after the initial delay. This value is usually specified as a number of characters per second that will appear on your screen and in your text.
Num Lock
Some BIOSs let you configure the toggle state of some keyboard keys. The most common option is the setting of the Num Lock key. Most systems default to booting up with Num Lock switched off. This option lets you have your system boot with Num Lock on so you can go right to work crunching numbers. This option is an aid primarily for systems with old 84-key keyboards that lack a separate cursor pad. MS-DOS 6.0 and later enable you to accomplish the same effect as this option by adding the line NUMLOCK=ON to your CONFIG.SYS file.
Boot Device or Sequence
By design, computers normally try to boot from the floppy disk first, and only if they find no disk in the floppy drive do they attempt to boot from the hard disk. This strategy helps you get going when something happens to your hard disk so that it’s no longer bootable. On the downside, it slows the boot process and forces you to wait for the buzz of the first floppy drive access. It also requires you keep disks out of your floppy drive until after your computer boots up.
Although neither of these shortcomings is fatal, they can be bothersome. Consequently, some BIOS-makers give you the option of setting the order that the BIOS searches for a bootable disk drive. Depending on the computer and BIOS-maker, several options are possible.
Some BIOS-makers enable you to directly specify the boot order of your computer’s disk drives. Typically your options will be listed as “A:, C:” or “C:, A:.” Sometimes only the first drive letter will be listed. Specify A: to make your system attempt first to boot from floppy or C: to skip the floppy and try your hard disk first.
Other BIOSs have the option Floppy Seek at Bootup, which lets you toggle between Yes or No. If you select No, the BIOS will ignore the floppy disk drive when attempting to boot your computer, even if it has a valid system disk in it. You can take advantage of this option to prevent inexperienced users from booting your computer from their own, possibly virus-infected, floppy disks.
Recent systems also give you the option Auto Boot Sequence, or Smart Boot. This is an attempt at the best of both worlds. Most of the time the intelligence of this technique is limited to sampling the floppy disk drive to determine whether it contains a disk, booting from it if the disk is a system disk, and ignoring the drive and booting from hard disk if the disk in the floppy drive is not a system disk or no disk is there at all.
Passwords
Many BIOSs have built-in password protection so that you can limit who uses your computer. The setup program typically gives you the option to enable or disable password protection. When you enable protection, the system stores your password in its CMOS memory. If the battery that backs up your CMOS gets low, you’ll lose password protection until you replace the battery.
Tuning for Performance
Extra speed is hidden in each of the major components of your computer—the microprocessor, the memory, and your chipset. It takes the form of component tolerances and safety factors, a little bit more than the ratings that every electronic part is good for. By pushing a little harder, you can gain more power from your computer. Although you won’t double your system’s overall speed, you could gain several percent, enough to give you an edge in game-playing or quicken your daily grind.
Fine-tuning your BIOS is the key to unlocking the extra speed potential of your computer. A suitable BIOS will allow you to tweak the configuration of your motherboard chipset and alter microprocessor and memory timing. Each adjustment promises an extra dollop of speed.
Unfortunately, the tenability of BIOSs varies widely. Large computer companies—Compaq, Dell, Hewlett-Packard, IBM, Sony, and Toshiba—give you control only over a handful of setup parameters that enable you to customize security, add a few peripherals, and configure ports. They don’t let you try to eke more performance from your computer because, well, they figure you’re likely to screw up. Set the wrong value for a vital parameter, and your computer will stop working and the manufacturer will get a support call—and may have to send out a technician to get your machine running again. By not giving you such intimate control, the manufacturer saves on support.
Smaller computer-makers—say, the one operating in the garage next door—get a competitive edge by using motherboards with tunable BIOSs. They can tweak in more performance than the bigger computer-makers and give you a faster system. Most makers of motherboards not affiliated with one of the big computer companies have learned that they gain a competitive edge with power users by giving them complete setup flexibility. The pioneer among these companies was Abit, which developed its extremely tweakable SoftBIOS in 1994. Through it and its successors, you can adjust nearly every controllable parameter of your motherboard’s chipset. Not only can you adjust the clock speed of the microprocessor to edge up performance by overclocking, you can shave cycles off the inevitable waits for memory refresh and access. With some systems, you can even adjust the voltage supplied to the microprocessor, monitor the environment inside your computer, and set limits on its operation.
Most computer-makers—and the major brands in particular—are conservative in the demands they make on computer components, such as the microprocessor and memory. They prefer to err on the cautious side because it minimizes the need for support. Moreover, they make no allowances for the differences between individual components. You may be lucky and get memory that’s rated at 133MHz but will function fine at 150MHz. No motherboard-maker wants to take on the burden of testing the limits of each component when preparing a product. But you can do the testing yourself and set your computer to take advantage of the full potential of its major components.
Realistically speaking, the major manufacturers’ caution is justifiable. The gains from fine-tuning your BIOS setup are modest, typically a few percentage points. If you’re the slightest bit greedy and push your chipset too hard, you can render your computer completely unusable and even destroy the data stored on your hard disk. Go too far, and you can even kiss off an investment in $1000 silicon when your microprocessor melts down into worthless sand.
Play it safe. Backup anything that’s important on your system before you begin. Familiarize yourself with your motherboard and locate its CMOS reset (if it has one). Also, check for jumper or switch settings for the basic microprocessor and bus operating parameters. Some BIOSs, although they allege to give you complete control through the setup, actually require hardware settings of some vital parameters. Your BIOS may or may not be able to override these hardware settings. If in the process of trying to set the chip speed through your BIOS your system does not cooperate, double-check your motherboard manual for hardware adjustments.
Clock Speeds
The obvious way to eke more speed from a system is to up the microprocessor speed, an enhancement usually termed overclocking because it requires operating the chip over and beyond the clock speed rating set by its manufacturer. Kick up the microprocessor’s clock, and you can expect a corresponding linear increase in performance.
Raising memory speed also influences the overall performance of your system. The effect can be dramatic because memory performance has not kept in step with microprocessor speed. All modern computer memory systems operate at a fraction of microprocessor speed, requiring the microprocessor to slow down or wait for memory access. On-chip memory caching reduces, but does not eliminate, the waiting.
Optimizing the performance of your computer requires considering both the speed at which you operate the microprocessor and the speed at which you operate memory. Not only do you need to consider adjusting both, but in most systems you will also be forced to adjust both. The two speeds interact, and their control is often linked.
Most BIOS setup systems do not give you the option of simply changing the microprocessor clock speed because of the design of the chips themselves. Most microprocessors accept a single external clock frequency, which controls the operation of the front side bus or memory bus. The microprocessor speed is derived from this value through a multiplier. Consequently, if you do not vary the multiplier, microprocessor and memory speed settings interact. Up the memory speed and you’ll raise the microprocessor speed.
The multiplier guarantees that the jump in microprocessor speed will be substantially higher than the memory speed increase (it multiplies the effect—what did you expect?), and you may soon run past the microprocessor’s inherent speed limit.
Depending on the actual memory modules installed in your computer, your system’s memory system may be more or less tolerant of speed adjustments, as is your microprocessor, even after allowing for the effect of the multiplier. Consequently, you may need to adjust both the clock speed setting and multiplier setting to achieve optimum performance from your system.
A further clocking issue is that the design of some motherboards links the PCI expansion bus clock to the front side bus (memory) clock. Although the PCI bus is designed to allow asynchronous operation (it need not be linked to memory speed), many systems do forge such a connection. This linkup can be problematic because PCI devices can be the most speed sensitive in your system. Typical expansion boards—modems, network interface cards (NICs), and SCSI disk controllers—often develop problems when you raise the PCI bus from its nominal 33MHz speed past about 37MHz.
Cycle Shaving
In addition to adjusting the clock speed of memory, many BIOSs allow you to adjust intimate aspects of memory timing (for example, the number of clock cycles required for the operation of the memory system). Most of the available settings control the number of cycles of delay between memory control signals. The opportunities for fine-tuning are amazing—you could spend weeks testing the potential combinations of adjustments.
Such attempts will likely be fraught with problems, however. Most adjustments will yield nonworking systems. Moreover, many of them interact, and most make no discernable difference in system performance.
The most worthwhile memory parameter to experiment with is the Column Address Strobe latency, or CAS latency. This setting adjusts the number of clock cycles the system waits in between reading bits in the same memory column. A lower value means less waiting and thus a faster computer.
Typical CAS latency values in Pentium III-class and Athlon systems range from two to four cycles. Some BIOSs may even allow half-cycle values (for example, 2.5 cycles).
From a technical standpoint, adjusting CAS latency rather than clock speed holds an advantage of a different type. Changing the CAS latency does not raise the operating speed of any part of the computer. Hence, it should not add to the heat stress of any computer component and should not affect the life of your computer’s circuits.
System Integrity
Pushing any component beyond its rating runs the risk that the component will no longer operate. A single malfunctioning component can lead to your computer no longer booting. But just because your computer boots after you make a BIOS adjustment that affects performance does not mean all is well. You still run the risk that one or more of the parts inside your computer are on the edge of failing. As a result, your computer may boot, but may not operate reliably.
Memory errors are among the most likely problems to arise from pushing memory speed up. Although server memory often has built-in error correction to ward against memory problems, most modern workstations, desktops, and notebook computers lack even parity-checking memory that warns of memory errors (by halting the system). These unprotected systems can develop memory errors without warning, and these errors can ripple though your system until it crashes. In other words, adjust memory speed cautiously, and don’t depend on a souped-up system until you’ve given it time to prove itself.
Microprocessors, too, become unreliable if operated at speeds that are too high. Some BIOSs, however, allow you to help your microprocessor cope with high clock speeds by increasing the core voltage. Higher voltages allow the chip to operate faster without sacrificing data integrity. If you increase your microprocessor speed significantly, you may want to increase its core voltage to ensure its reliable operation. The corollary also applies. If you increase the core voltage of your microprocessor, you should be able to increase the chip’s clock frequency more than would have otherwise been possible.
You won’t find guidance as to the relationship between voltage and potential speed increases anywhere. Chip-makers test only at design voltages and frequencies. Motherboard-makers defer to the chip-makers, warning only that you should keep within the range specified by the chip-maker. Your only choice is to try and see.
Before adjusting microprocessor core voltage, be sure that you have adequate cooling for your chip. Microprocessor power use—and therefore heat output—increases to the square of the increase in voltage. Consequently, a small voltage increase can quickly lead to the overheating of your microprocessor and, potentially, its self-immolation.
BIOS-makers provide some help with this issue, however. Among the settings for most BIOSs affording voltage control are temperature sensors that allow you to monitor both chip temperature and the temperature inside your computer’s case. Some allow for warning when temperatures exceed the limits you set. You may be able to set a shutdown temperature for your microprocessor.
Even these shutdown temperature settings don’t guarantee the safety of your expensive silicon, however. The temperature probes measure the microprocessor’s external temperature, not the temperature at the semiconductor junctions where damage actually occurs. If you grossly increase the voltage to the microprocessor, the junction temperature can skyrocket into the meltdown range well before any external chip sensor detects a significant temperature change. In other words, step cautiously. If you are tempted to try increasing chip core voltage, do so in small increments—and carefully monitor chip temperature after each change.
Other Options
Speeding up clocks and shaving cycles aren’t the only ways you can potentially pluck more performance from your system through BIOS adjustments. Many BIOSs afford you some opportunity to optimize the waits inherent in bus access. In addition, nearly all modern BIOSs allow you to shadow the BIOS code itself.
Although these adjustments sound promising, in reality they do little to improve the overall speed of your system. For example, the real purpose of the bus recovery time adjustments is to help achieve compatibility with older expansion boards. Both the 8-bit I/O recovery time and 16-bit I/O recovery time settings present in the BIOSs of systems with both PCI and ISA expansion buses let you slow down the system to accommodate marginal expansion boards connected through the legacy or ISA bus. Although increasing the recovery time, usually measured in bus cycles, may allow you to use older ISA expansion boards, decreasing it will not affect normal system performance.
BIOS shadowing copies the BIOS firmware from ROM to RAM. In theory, it enables your system to read the BIOS code from RAM (32-bit or 64-bit) memory instead of 8- or 16-bit ROM memory. This should speed up BIOS-mediated operations substantially. However, modern operating systems, including Linux and all varieties of Windows from 95 through XP, sidestep the BIOS by using drivers that take direct control of system hardware. Shadowing will not affect the performance of programs run under any of these modern operating systems. In other words, shadowing is a carryover from the days of DOS that’s essentially irrelevant to modern computers. Leaving BIOS shadowing off will help ensure system stability and slightly increase available memory.
Video shadowing is similarly ineffectual in accelerating today’s software. Windows uses its own drivers that directly access video hardware, so video shadowing does not affect normal system performance.
Some BIOSs also offer adjustments for your system’s memory cache. Depending on the BIOS, you may have individual control of both Level 1 (L1) and Level 2 (L2) caches, which are sometimes termed primary and secondary, or more confusingly, internal and external (confusing because both the L1 and L2 caches are internal with many microprocessors, such as current Athlon, Duron, Pentium III, and Pentium 4 chips). Your BIOS may also allow you to selectively switch off the microprocessor read cache or write cache.
No matter. In any case, the only potential here is for slowing down your system by turning the cache off. These cache controls are not designed to adjust performance. Rather, they are useful only for troubleshooting or preventing problems with software. But programs that have problems with the cache are probably programs you shouldn’t be running.
Tuning your system with its BIOS is inevitably a trial-and-error experience. You are investing your time to make tests more rigorous than those made by chip manufacturers so that you can run all of your computer’s components as close to the edge as possible.
Upgrades
At one time, engineers viewed the BIOS as a great sculpture or other great work of art, fixed forever in time, perfect and immutable. The BIOS code would be written in read-only memory chips that could not be altered, at least by mere mortals without electrical engineering degrees. But human frailties and rapidly changing technologies forced them to change their minds. They made mistakes in writing some BIOSs that only became apparent after they were shipped off to consumers in finished computers. Or, a few months after they had finished work on their BIOSs—and after computers using them found their ways into consumers’ hands—someone decided it would be great if hard disks could store twice as much as the BIOS made allowances for. The only way to make up for the shortcoming of the permanent BIOS was to replace the memory chips, a task most people face with the same calm ease as disarming a tactical nuclear weapon.
Consequently, today most computers come with their BIOS code written in Flash ROM chips, which can be rewritten with relative safety and without even removing the lid from your computer system. If your BIOS needs an upgrade, either to fix an error or to accommodate a new technology, you can usually download a new BIOS from the Web site of the computer’s manufacturer.
Updating a Flash BIOS usually involves two files: a binary file that contains the actual BIOS code, and a special program called a loader. The loader activates the motherboard circuitry required to write to the BIOS chips and then transfers the contents of the binary BIOS file to the chips. The loader’s job is one of the most delicate in the operation of a computer because if it makes a mistake, your system may be rendered inoperable. It might not be able to boot up and rerun the loader. Consequently, for your security, some system-makers require you take elaborate precautions before you try making a BIOS upgrade. For example, the manufacturer may require you to use both the battery and AC power supplies of a notebook computer to make a BIOS update.
To prevent a BIOS upgrade from accidentally rendering your computer inoperable, many computers include boot block protection. This feature simply protects or prevents the block of the Flash ROM used for the essential bootup code—the code necessary to let your system read a floppy disk—from being erased during the upgrade. The protected code is sufficient to get your floppy going so that you can try upgrading your BIOS once again (or if the new BIOS itself is the problem, restore your old BIOS).
Because motherboard circuitry varies among different computer brands and models, the BIOS loader made for one system may not work with another. Unless you’re advised otherwise by your computer’s manufacturer or a BIOS-maker, you should assume that you need a matched pair of files—the BIOS code and loader—to make a BIOS upgrade. In general a loader will warn if it is not meant for your particular system, but don’t depend on such a warning to avoid incompatibilities. A loader that makes a mistake can mean your computer must go back to the factory for new BIOS chips before it will boot again.
Along with fixing problems, upgrading a flash BIOS can sometimes cause them, too. BIOS-makers usually design their flash BIOS loaders to reset your computer’s setup parameters to the factory defaults so your system gets a fresh start with its new BIOS. If you’ve customized your system before making the upgrade (for example, adjusting the energy conservation options of a notebook machine), you’ll have to re-establish your settings after the upgrade. Sometimes you may find that the load process has altered the date set in CMOS. Operating your system without checking and resetting the date can cause problems with programs sensitive to the relationship between the current time and file date codes. For example, your backup system or disk maintenance program may not work properly after you’ve upgraded your BIOS if you don’t properly restore your system clock.