Security of Files
Security of files refers to the protection of files.
POSSIBLE DANGERS
Files may be in danger of accidentally or intentionally:
1 Being destroyed, for example,
(a) By fire.
(b) By hardware failure such as scratches on a disc caused by dirt.
2 Being modified, for example,
(a) By being unintentionally written over,
(b) For malicious reasons such as fraud,
(c) By being updated with incorrect data.
3 Being accessed by unauthorized people.
METHODS OF PROTECTING DATA
Keeping copies
Data can be protected from destruction or modification by keeping copies, although care has to be taken that this does not make unauthorized access easier. Methods include:
1 Dumping files periodically onto backing store or onto an output device.
2 Keeping generations of a file.
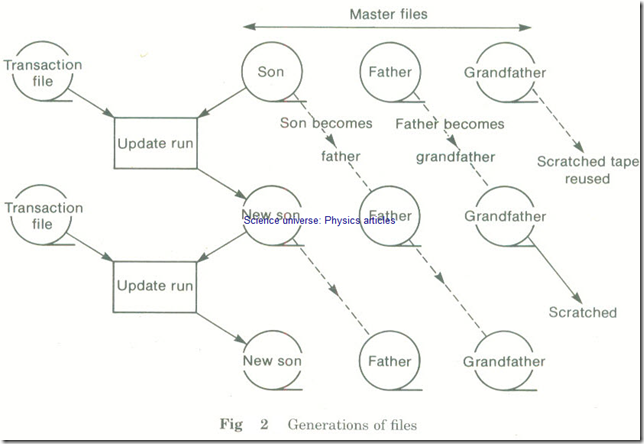
When a file is updated, the new file is called a son. The previous master file, from which it was produced, is called a father and the one before that a grandfather. When the son becomes a father, the father becomes a grandfather (as you might expect). (See Fig 2)
Usually three generations are always kept (son, father and grandfather) so that if data is lost or incorrectly updated it can be recovered.
Fig 2 Generations of files
Physical safeguards
1 To safeguard against fire or theft, important files and software are often kept in another building in a fireproof safe.
2 Magnetic tapes often have to be fitted with write permit rings before data can be written on them. Similar measures can be taken for other media.
3 Only authorized personnel are allowed in certain areas of many computer installations.
Software safeguards
The computer’s operating system may be used to restrict access to the system:
1 Anyone using the computer may have to use a password .
2 Some files may only be accessible to certain passwords.
3 On networks users may be able to give files an access code. This is a code which they add to the filename to indicate which users are allowed access to the file.