files
CASE STUDY
Opposite each of the following statements ring whether it is true or false.
|
statement |
||
|
Vehicle records are divided into fields |
true |
false |
|
Vehicle fields are divided into files |
true |
false |
|
Vehicle files are divided into records |
true |
false |
|
Vehicle records are divided into files |
true |
false |
Which of the following is suitable for storing in a fixed length field of 6 characters?
A Address
B Birthplace
C Date of birth D Name
A stock file is held on magnetic disc so that records can be read and updated in any order.
(a) What is the name of this type of access?
(b) Could the stock file reasonably be held on magnetic tape?
Explain your answer.
CASE STUDY
Two files used by the DVLC are the vehicle transaction file and the vehicle main file.
Write either transaction or main against each of these two descriptions.
(a) A file containing details of any changes to be made.
(b) A file holding a record of every vehicle registered in the U.K.
SEB Standard Specimen
(a) Peter has written a COMAL program for a project. He wants to make a back-up copy on another disc. His teacher gives him a disc. Explain why a new disc must first be formatted before it can be used to store programs.
(b) Peter has a computer system with one disc drive. He wants to make the back-up copy using the LOAD and SAVE commands. Write out a list of instructions for him to do this.
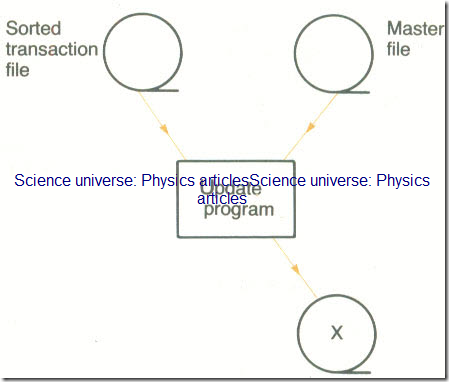
A master file and a sorted transaction file are stored on magnetic tapes. The transaction file has been checked and is known to contain only new records to be inserted into the master file. Describe how a new master file can be generated using the existing master file and the transaction file.
In the diagram below what is X?
A Grandfather file
B New master file
C New transaction file
D Unsorted transaction file
The contents of four files are shown below.
|
file A |
file B |
file C |
File D |
|
27 |
93 |
34 |
27 |
|
36 |
60 |
39 |
34 |
|
38 |
34 |
45 |
36 |
|
97 |
39 |
60 |
38 |
|
102 |
93 |
39 |
|
|
45 |
102 |
45 |
|
|
60 |
|||
|
93 |
|||
|
97 |
|||
|
102 |
(a) State how utility routines could have been used to produce files C and D from files A and B.
(b) Describe the function of one other utility routine.
‘Hacking’ is where someone tries to gain illegal access to a computer system. This is usually done using a remote terminal or microcomputer.
(a) Give one example of harm that a ‘hacker’ might do if successful in breaking into a
computer system.
(b) One method of protecting computer systems from ‘hackers’ is to have a system of passwords or codes. These should be secret and known only to legal users. Some people use names of people close to them because they are easy to remember. Why is this not a good idea?
(c) Give a suitable password for a remote access computer system. Say why you have given it.
(d) Give one further simple method of protecting a computer system from ‘hackers’ trying to use remote terminals.
CASE STUDY
Several generations of vehicle master file are kept by the DVLC.
Why do they keep them when they are no longer up to date?
Which of these is used to guard against accidental loss of data?
A Keeping back-up copies of files
B Keeping files under lock and key
C Keeping terminals under lock and key
D Using passwords
In an application three generations of the master file are kept. What are these three generations normally called and why are they considered necessary? Why is it also necessary to keep generations of the transaction file?